RIVERBANK LABS
Acoustic Alchemy
Pioneering Esoteric Lab & Think Tank
How Decoding Shakespeare and Levitation Led to NSA
& Helped Win Two World Wars
by Iona Miller, (c)2010, All Rights Reserved
ESOTERICS TO WEIRD SCIENCE
PRO: Riverbank produced book on Baconian Cipher
http://books.google.com/books?id=dPwsAAAAYAAJ&printsec=frontcover&dq=riverbank+laboratories&source=bl&ots=0DnT5fZGfh&sig=C1QFk4f3hJ5_-Qw7ADgRQSnxsQE&hl=en&ei=NQu4TLGQGJG-sAP1zYGWDw&sa=X&oi=book_result&ct=result&resnum=3&ved=0CB0Q6AEwAjgK#v=onepage&q&f=false
PRO: Riverbank produced book on Baconian Cipher
http://books.google.com/books?id=dPwsAAAAYAAJ&printsec=frontcover&dq=riverbank+laboratories&source=bl&ots=0DnT5fZGfh&sig=C1QFk4f3hJ5_-Qw7ADgRQSnxsQE&hl=en&ei=NQu4TLGQGJG-sAP1zYGWDw&sa=X&oi=book_result&ct=result&resnum=3&ved=0CB0Q6AEwAjgK#v=onepage&q&f=false
Bacon Ciphers in Shakespeare were proposed in The Great Cryptogram by Ignatius Donnelly
http://books.google.com/books?id=Z5INAAAAYAAJ&printsec=frontcover&dq=%22The+Great+Cryptogram%22+Ignatius+Donnelly&source=bl&ots=pR09NdGhvR&sig=BRRZfeXu5XpXS7h_xrB5vkiVz2I&hl=en&ei=jU3nTIjYG4WisAPGib2xCw&sa=X&oi=book_result&ct=result&resnum=1&ved=0CBMQ6AEwAA#v=onepage&q&f=false
http://books.google.com/books?id=Z5INAAAAYAAJ&printsec=frontcover&dq=%22The+Great+Cryptogram%22+Ignatius+Donnelly&source=bl&ots=pR09NdGhvR&sig=BRRZfeXu5XpXS7h_xrB5vkiVz2I&hl=en&ei=jU3nTIjYG4WisAPGib2xCw&sa=X&oi=book_result&ct=result&resnum=1&ved=0CBMQ6AEwAA#v=onepage&q&f=false
RIVERBANK THINKTANK,
West of Chicago:
From a Baconian Levitation Machine to Acoustic Alchemy

How a Seemingly Failed Levitation Machine Led to the Founding of NSA & the Secrets of Ciphers
First Thinktank * First Privately Owned Research Laboratory * First US Decryptions * Genetics * Acoustics
Original US Esoterics Lab & Thinktank
"Some rich men go in for art collections, gay times on the Riviera, or extravagant living. But they all get satiated. That’s why I stick to scientific experiments, spending money to discover valuable things that universities can’t afford. You never get sick of too much knowledge." --Col. George Fabyan
"Less Noise; More Hearing": Geneva, Illinois. Riverbank Engineering Bldg.
Somewhere between a step pyramid and Tibetan architecture, Riverbank Labs reflects the eccentricities of its builder. The Villa residence, 40 miles west of Chicago, is now a museum that houses collections of photos and memorabilia of cotton-fortune heir Col. George Fabyan. The Villa was designed by Frank Lloyd Wright in 1907. In 1914, landscape architect Taro Otsuka designed Fabyan’s Japanese Garden. An imported Dutch windmill stands in another portion of the 600-acre estate. The garden was restored in 1971 and again in 1994, and is open to the public.
Many different research activities occurred at Riverbank, including decoding and deciphering enemy messages during World War I, deciphering alleged secret messages in the works of William Shakespeare, research in the field of architectural acoustics, groundbreaking research in the field of cryptology, fieldwork in the use of hand grenades and military trenches, research and development of tuning forks, and studies of human fitness and anatomy. Teams of researchers lived and worked at Riverbank, devoting years of their lives to frontier science. Many scientists from around the nation and world have visited Riverbank and stayed at The Lodge. The United State’s military successes in World War I and World War II were supported by Riverbank, which is a direct lineal predecessor of the National Security Agency and Central Intelligence Agency.
As Friedman and his staff in the Riverbank Department of Codes and Ciphers worked on solving messages coming in from various federal agencies and foreign governments, they became the first unofficial cryptologic organization in the United States. It was still many months before Military Intelligence was formed as the nation’s first official cipher bureau. Friedman invented the words "cryptanalysis" and "cryptology", the first being code-breaking, and the latter being the overall term used to describe the science. In 1929, he became widely known as one of the world’s leading authorities on cryptology when the Encyclopedia Britannica published his article on "Codes and Ciphers." The Black Chamber was dissolved in 1929 and the Signal Intelligence Service was created with William Friedman as its first director. His first task was to set up an adequate program to provide training for officers in cryptology. The result was the Signal Intelligence School. He also wrote three textbooks on military cryptography for these courses. These comprise the finest, most lucid exposition of the solution of basic ciphers that has ever been published. The Black Chamber, otherwise known as MI-8 or Cipher Bureau, was the United States' first peacetime cryptanalytic organization, and a forerunner of the National Security Agency. The only prior codes and cypher organizations maintained by the US government had been some intermittent, and always abandoned, attempts by Armed Forces branches prior to World War I.
The American Black Chamber By Herbert Osborn Yardley
http://books.google.com/books?id=Y2GI32l-hXIC&printsec=frontcover&dq=%22The+Black+chamber%22&source=bll&ots=xg4UEBzEhn&sig=D4sT-ij1zkXbSmytjinLpUietnY&hl=en&ei=Kbe4TKPWPJDksQPH74D7Dw&sa=X&oi=book_result&ct=result&resnum=11&ved=0CEQQ6AEwCg#v=onepage&q&f=false
BACON & SCRAMBLED CIPHERS: Eventually, Fabyan’s estate grew to cover 600 acres and was the home to award-winning flowers, livestock and other animals. Fabyan imported scientists from the fields of plant genetics and acoustics as well as cryptography to his estate. The cryptographers were mainly there to prove that Bacon wrote Shakespeare's plays, but still ended up being the foundation for the NSA. Under the theoretical spell of Elizebeth Wells Gallup, Fabyan read in one of Bacon's works a description of a levitation device that allegedly worked on acoustic principles. He built one, but couldn't get it to fly, so he sent to Harvard University for some acoustic experts to help him. Revealed by the code, previously known only to the Rosicrucians, is an acoustical levitating machine. A huge drum with piano strings stretched along its surface is rotated within an outer casing with corresponding strings. As the strings vibrate, the outer shell is made to levitate.
It had been known for some time that Francis Bacon belonged to a secret society called the Rosicrucian Society. They believed in conducting scientific experiments that in those times was often considered witchcraft. Due to Bacon’s position with the Queen of England, he ran the Queen’s printing press, and had devised what was called a biliteral cipher utilizing wide and thin letters to represent the alphabet. Colonel Fabyan also believed in the Baconian theory. Mrs. Gallup believed Bacon was the real Shakespeare for two reasons: 1) Bacon had invented the biliteral cipher and used it in printed publications, and 2) the original printed folios of Shakespeare’s plays used a variety of different typefaces.
So goes the theory; trouble is, it doesn't work. Or, at least acoustic alchemy had not yet come into its own. Fabyan invited the famous professor Wallace Sabine to his estate to study the problem. The professor made a few calculations, and convinced Fabyan there would never be enough sound energy to lift anything. Might the old gentleman be interested in underwriting some genuine scientific research, such as a reverberation chamber?
So began decades of discovery: Sabine's formula for sound absorption is still used in many standard acoustical tests, and the unit of absorption now bears his name, "sabin." The wonders recorded included sound absorbers that seemed to absorb more sound than fell upon them; an acoustical consultant, never hired for a certain concert hall project, who was criticized for its poor acoustics (while another acoustical consultant was praised for the excellent acoustics of the very same hall); the standard color of sound used in an acoustical laboratory; the required height, weight and shoes for a lady floor-walker; and much, much more, equally exotic.
The Colonel died May 17, 1936; his wife died two years later, and the executors of her will sold Riverbank to the Kane County Forest Preserve for $70,500. Various guests to the estate supposedly included Albert Einstein, P.T. Barnum and Wallace Clement Sabine (American physicist and pioneer founder of the field of architectural acoustics). The work in cryptology done there by William Friedman, work in acoustical research done by Wallace Clement and Paul (a distant cousin) Sabine, and Fabyan's strange desire to prove that the works of Shakespeare were in fact not written by Shakespeare but contained Baconian ciphers. Elizabeth Wells Gallup studied Shakepeare’s First Folio to see if the differences in variations of type represented Bacon’s use of the biliteral cipher. One of the messages she deciphered was: "Queen Elizabeth is my true mother, and I am the lawful heir to the throne. Find the Cypher storie my books contain; it tells great secrets, every one of which, if imparted openly, would forfeit my life. F. Bacon" They also worked unsuccessfully on the inscrutable Voynich Manuscript.
One of the scientific experiments documented by Sir Francis Bacon was a levitating machine.
The machine was a wooden tube with metal strings attached to it, around which fit another wooden tube with metal strings attached to the inside of it. The center tube was supposed to spin and by sympathetic vibration cause the strings on the outer tube to vibrate. The resonance from the striking would create a force field, which would levitate the outer tube off of the ground. Colonel Fabyan hired Bert Eisenhour, an engineer from Chicago, to construct this machine at Riverbank. Though the machine was constructed, it did not work. Eisenhour was convinced that the strings were not tuned properly, and suggested they consult someone knowledgeable in acoustics.
Decipherment from Shakespeare's first folio produced the plans for the Baconian Acoustical Levitation Device, which Fabyan and his army managed to build. [See photo] It was: A wooden tube with metal strings attached to it, around which fit another wooden tube with metal strings attached to the inside of it. The center tube was supposed to spin and by sympathetic vibration cause the strings on the outer tube to vibrate. The resonance from the striking would create a force field, which would levitate the outer tube off of the ground.
First Thinktank * First Privately Owned Research Laboratory * First US Decryptions * Genetics * Acoustics
Original US Esoterics Lab & Thinktank
"Some rich men go in for art collections, gay times on the Riviera, or extravagant living. But they all get satiated. That’s why I stick to scientific experiments, spending money to discover valuable things that universities can’t afford. You never get sick of too much knowledge." --Col. George Fabyan
"Less Noise; More Hearing": Geneva, Illinois. Riverbank Engineering Bldg.
Somewhere between a step pyramid and Tibetan architecture, Riverbank Labs reflects the eccentricities of its builder. The Villa residence, 40 miles west of Chicago, is now a museum that houses collections of photos and memorabilia of cotton-fortune heir Col. George Fabyan. The Villa was designed by Frank Lloyd Wright in 1907. In 1914, landscape architect Taro Otsuka designed Fabyan’s Japanese Garden. An imported Dutch windmill stands in another portion of the 600-acre estate. The garden was restored in 1971 and again in 1994, and is open to the public.
Many different research activities occurred at Riverbank, including decoding and deciphering enemy messages during World War I, deciphering alleged secret messages in the works of William Shakespeare, research in the field of architectural acoustics, groundbreaking research in the field of cryptology, fieldwork in the use of hand grenades and military trenches, research and development of tuning forks, and studies of human fitness and anatomy. Teams of researchers lived and worked at Riverbank, devoting years of their lives to frontier science. Many scientists from around the nation and world have visited Riverbank and stayed at The Lodge. The United State’s military successes in World War I and World War II were supported by Riverbank, which is a direct lineal predecessor of the National Security Agency and Central Intelligence Agency.
As Friedman and his staff in the Riverbank Department of Codes and Ciphers worked on solving messages coming in from various federal agencies and foreign governments, they became the first unofficial cryptologic organization in the United States. It was still many months before Military Intelligence was formed as the nation’s first official cipher bureau. Friedman invented the words "cryptanalysis" and "cryptology", the first being code-breaking, and the latter being the overall term used to describe the science. In 1929, he became widely known as one of the world’s leading authorities on cryptology when the Encyclopedia Britannica published his article on "Codes and Ciphers." The Black Chamber was dissolved in 1929 and the Signal Intelligence Service was created with William Friedman as its first director. His first task was to set up an adequate program to provide training for officers in cryptology. The result was the Signal Intelligence School. He also wrote three textbooks on military cryptography for these courses. These comprise the finest, most lucid exposition of the solution of basic ciphers that has ever been published. The Black Chamber, otherwise known as MI-8 or Cipher Bureau, was the United States' first peacetime cryptanalytic organization, and a forerunner of the National Security Agency. The only prior codes and cypher organizations maintained by the US government had been some intermittent, and always abandoned, attempts by Armed Forces branches prior to World War I.
The American Black Chamber By Herbert Osborn Yardley
http://books.google.com/books?id=Y2GI32l-hXIC&printsec=frontcover&dq=%22The+Black+chamber%22&source=bll&ots=xg4UEBzEhn&sig=D4sT-ij1zkXbSmytjinLpUietnY&hl=en&ei=Kbe4TKPWPJDksQPH74D7Dw&sa=X&oi=book_result&ct=result&resnum=11&ved=0CEQQ6AEwCg#v=onepage&q&f=false
BACON & SCRAMBLED CIPHERS: Eventually, Fabyan’s estate grew to cover 600 acres and was the home to award-winning flowers, livestock and other animals. Fabyan imported scientists from the fields of plant genetics and acoustics as well as cryptography to his estate. The cryptographers were mainly there to prove that Bacon wrote Shakespeare's plays, but still ended up being the foundation for the NSA. Under the theoretical spell of Elizebeth Wells Gallup, Fabyan read in one of Bacon's works a description of a levitation device that allegedly worked on acoustic principles. He built one, but couldn't get it to fly, so he sent to Harvard University for some acoustic experts to help him. Revealed by the code, previously known only to the Rosicrucians, is an acoustical levitating machine. A huge drum with piano strings stretched along its surface is rotated within an outer casing with corresponding strings. As the strings vibrate, the outer shell is made to levitate.
It had been known for some time that Francis Bacon belonged to a secret society called the Rosicrucian Society. They believed in conducting scientific experiments that in those times was often considered witchcraft. Due to Bacon’s position with the Queen of England, he ran the Queen’s printing press, and had devised what was called a biliteral cipher utilizing wide and thin letters to represent the alphabet. Colonel Fabyan also believed in the Baconian theory. Mrs. Gallup believed Bacon was the real Shakespeare for two reasons: 1) Bacon had invented the biliteral cipher and used it in printed publications, and 2) the original printed folios of Shakespeare’s plays used a variety of different typefaces.
So goes the theory; trouble is, it doesn't work. Or, at least acoustic alchemy had not yet come into its own. Fabyan invited the famous professor Wallace Sabine to his estate to study the problem. The professor made a few calculations, and convinced Fabyan there would never be enough sound energy to lift anything. Might the old gentleman be interested in underwriting some genuine scientific research, such as a reverberation chamber?
So began decades of discovery: Sabine's formula for sound absorption is still used in many standard acoustical tests, and the unit of absorption now bears his name, "sabin." The wonders recorded included sound absorbers that seemed to absorb more sound than fell upon them; an acoustical consultant, never hired for a certain concert hall project, who was criticized for its poor acoustics (while another acoustical consultant was praised for the excellent acoustics of the very same hall); the standard color of sound used in an acoustical laboratory; the required height, weight and shoes for a lady floor-walker; and much, much more, equally exotic.
The Colonel died May 17, 1936; his wife died two years later, and the executors of her will sold Riverbank to the Kane County Forest Preserve for $70,500. Various guests to the estate supposedly included Albert Einstein, P.T. Barnum and Wallace Clement Sabine (American physicist and pioneer founder of the field of architectural acoustics). The work in cryptology done there by William Friedman, work in acoustical research done by Wallace Clement and Paul (a distant cousin) Sabine, and Fabyan's strange desire to prove that the works of Shakespeare were in fact not written by Shakespeare but contained Baconian ciphers. Elizabeth Wells Gallup studied Shakepeare’s First Folio to see if the differences in variations of type represented Bacon’s use of the biliteral cipher. One of the messages she deciphered was: "Queen Elizabeth is my true mother, and I am the lawful heir to the throne. Find the Cypher storie my books contain; it tells great secrets, every one of which, if imparted openly, would forfeit my life. F. Bacon" They also worked unsuccessfully on the inscrutable Voynich Manuscript.
One of the scientific experiments documented by Sir Francis Bacon was a levitating machine.
The machine was a wooden tube with metal strings attached to it, around which fit another wooden tube with metal strings attached to the inside of it. The center tube was supposed to spin and by sympathetic vibration cause the strings on the outer tube to vibrate. The resonance from the striking would create a force field, which would levitate the outer tube off of the ground. Colonel Fabyan hired Bert Eisenhour, an engineer from Chicago, to construct this machine at Riverbank. Though the machine was constructed, it did not work. Eisenhour was convinced that the strings were not tuned properly, and suggested they consult someone knowledgeable in acoustics.
Decipherment from Shakespeare's first folio produced the plans for the Baconian Acoustical Levitation Device, which Fabyan and his army managed to build. [See photo] It was: A wooden tube with metal strings attached to it, around which fit another wooden tube with metal strings attached to the inside of it. The center tube was supposed to spin and by sympathetic vibration cause the strings on the outer tube to vibrate. The resonance from the striking would create a force field, which would levitate the outer tube off of the ground.
Levitation with Acoustics Actually Does Work

Investigative journalist, Charles W. Stone of MRU claims, "I did find evidence and a wood model of a device at the Geneva History Center of a "Baconian levitation device." It reportedly was workable, in principle. It is only a few steps to time travel. The Time travel which was developed by DARPA and the CIA after WW II was based on specialized music at The Vatican. (Also a form of acoustics)."
Chronovision allegedly came from the Vatican-based music experiments in the 50s. Chronovisor, a type of time machine which would bring pictures and sounds from the past into the present. Looking a bit like a television, the machine worked by detecting all the sights and sounds that humanity had made that still floated through space. The Chronovisor was portrayed as a large cabinet with a normal cathode ray tube for viewing the received events and a series of buttons, levers, and other controls for selecting the time and the location to be viewed. It could also focus and track specific people. According to its inventor, Father Pellegrino Ernetti, it worked by receiving, decoding and reproducing the electromagnetic radiation left behind from past events, though it could also pick up sound waves. Ernetti began by filtering harmonics from Gregorian chants. Instead they heard paranormal voices. The Pope wanted them to confirm faith in the Beyond.
Ernetti formulated theories to answer the questions: what happened to all the sights and sounds humans make? Did they disappear completely or do they continue to exist in some way? Through Papal connections and backing, he was introduced to a team of 12 of the world’s greatest scientific minds in order to further this research. A team which included Enrico Fermi, winner of the Nobel Prize for Physics in 1938 and designer of the world’s first nuclear reactor, as well as NASA rocket scientist Werner Von Braun, former SS Colonel, head of the Nazi rocket program and later the man who would lead the American Apollo space program. The research was conducted in complete secrecy, with no leaks or mentions made until the early 1960’s. The machine was supposedly destroyed.
It is possible that time travel was also investigated earlier at Riverbank Labs as there is a similarity to acoustics and music.
It does appear that levitation was also developed there. There is a relationship between standing waves and musical instruments. Resonance is a fundamental principle from micro to macrocosm as are harmonics. Musical tones are produced by musical instruments, or by the voice, which, from a physics perspective, is a very complex wind instrument. So the physics of music is the physics of the kinds of sounds these instruments can make. What kinds of sounds are these? They are tones caused by standing waves produced in or on the instrument. So the properties of these standing waves, which are always produced in very specific groups, or series, have far-reaching effects on music theory.
Most sound waves, including the musical sounds that actually reach our ears, are not standing waves. Normally, when something makes a wave, the wave travels outward, gradually spreading out and losing strength, like the waves moving away from a pebble dropped into a pond. But when the wave encounters something, it can bounce (reflection) or be bent (refraction). In fact, you can "trap" waves by making them bounce back and forth between two or more surfaces. Musical instruments take advantage of this; they produce pitches by trapping sound waves. Why are trapped waves useful for music? Any bunch of sound waves will produce some sort of noise. But to be a tone - a sound with a particular pitch - a group of sound waves has to be very regular, all exactly the same distance apart. That's why we can talk about the frequency and wavelength of tones.
You can produce a tone in a sound wave trap and keep sending more sound waves into it. Picture a lot of pebbles dropped into a very small pool. As the waves start reflecting off the edges of the pond, they interfere with the new waves, making a jumble of waves that partly cancel each other out and mostly just roils the pond - noise. But if you arrange the waves so that reflecting waves, instead of canceling out the new waves reinforce them, the high parts of the reflected waves meet the high parts of the oncoming waves and make them even higher. The low parts of the reflected waves would meet the low parts of the oncoming waves and make them even lower. Instead of a roiled mess of waves canceling each other out, we find a pond of perfectly ordered waves, with high points and low points appearing regularly at the same spots again and again. A single wave can reflect back and forth and standing waves.
Riverbank Lab was a giant resonant chamber, essentially an acoustic instrument.
Orderliness is actually hard to get from water waves, but relatively easy to get in sound waves, so that several completely different types of sound wave "containers" have been developed into musical instruments. The two most common are strings and hollow tubes. In order to get the necessary constant reinforcement, the container has to be the perfect size (length) for a certain wavelength, so that waves bouncing back or being produced at each end reinforce each other, instead of interfering with each other and canceling each other out. And it really helps to keep the container very narrow, so that you don't have to worry about waves bouncing off the sides and complicating things. So you have a bunch of regularly-spaced waves that are trapped, bouncing back and forth in a container that fits their wavelength perfectly. If you could watch these waves, it would not even look as if they are traveling back and forth. Instead, waves would seem to be appearing and disappearing regularly at exactly the same spots, so these trapped waves are called standing waves.
According to Charles Stone, Enrico Fermi was involved in acoustics and time travel. Riverbank was for many years the leading acoustics testing facility in the world. So that fits in with the time travel story. Riverbank is operated or maintained now by a medium sized high tech company in Tyson's Corner. The CEO was formerly the President of Illinois Institute of Technology which is closely linked to Riverbank. I know most of the senior Execs of the company of which a number are retired Navy and Army officers. The CEO even calls his own home The Villa, like the residence at Riverbank.
Iona Miller reports from 2008-2010 contact with Black Swan "Julian West": "This is of utmost importance to one of my own obsessive investigations. My paternal grandfather worked at the legendary Riverbank Labs for the infamous Col. George Fabyan. One of the many controversial/occult studies undertaken at Riverbank was the attempt to prove that Shakespeare was Bacon. (Elizebeth Friedman, for example, was one of Fabyan's most important colleagues. It is through her work that a connection can be established between Fabyan and Atlantis-scholar Ignatius Donnelly.)
Also conducted at Riverbank: Experiments in teleportation and acoustic time-travel via the use of acoustics.
Quantum teleportation of electrons in quantum wires with surface acoustic waves. lionization and trigger the formation of ion-acoustic oscillations. The external triggers may initiate spontaneous teleportation. In 1931, Charles Fort, an American writer, tried to describe the random disappearances and appearances of different anomalies. He felt that these sudden disappearances and appearances were connected and therefore felt that they were "teleporting." While he came up with this theory to try and explain why certain paranormal phenomena acted, many suggest that Fort probably didn't subscribe to the theory and was using it as a way of suggesting mainstream science didn't provide enough information on why these phenomena happened.
Dematerialising This is the transmission of data from one area and then the reconstruction of that object at its final destination. This is a theory that is presented in Star Trek when the individuals are "beamed down" to the planet. While the uncertainty principle suggests that humans are unable to be dematerialized because rebuilding their body as perfectly as they had previously been is nearly impossible. However, in 1998, scientists at Caltech were able to make a true teleportation occur. This resulted in energy being transmitted from one point to another with a distance of about one meter. While the scientists admit that it was only one meter, they argue that they feel they could make the energy transmit to distances much larger.
Dimensional Teleportation This theory of teleportation suggests that an object existing in one universe leaves that universe, enters another one and then returns to the original, but in a different place. However, this theory is not considered often because it goes against the argument that time travel is not possible. Wormhole According to some, a wormhole is a shortcut through time and space. It is suggested that an individual could go into a wormhole and this would be the "effective" method of getting from point A to point B without needing any form of time travel machines. However, little is known about whether these wormholes actually exist or not. Is Teleportation Possible? Teleportation has always been a sign of intrigue in the science fiction world; however, there is still little research available to suggest whether teleportation is actually possible. There have been successful experiments, though, that suggest that teleportation is possible. However, since this is only energy, it is argued that it would take a considerable amount of time to create a method of teleporting an individual. Even then, there are so many theories that suggest that it is impossible because regnerating a human would be nearly impossible.
West continues, "My grandfather had a very old set of Shakespeare's complete works (heavily annotated in more than one handwriting), which is now unfortunately lost, due to the ignorance and carelessness of his widow. (He never discussed the true nature of his work with his family; I myself have spent free time over several years just beginning to gather some real facts together (--discovering your work, linking Bacon to St. Germain, may be a big breakthrough in this research into the true nature and import of the experimental research conducted at Riverbank)). I also have in my own possession a few artifacts from Fabyan's estate, which came down from my grandfather."
Ms. Miller began investigating Riverbank Labs in 2006 with another high IQ MRU alumni, a spy-entist with intelligence connections, (a former military intel internal security officer) responding to questions about the NSA cryptographer in Dan Brown's proposal on "Solomon's Key" which appeared later as the book "Lost Symbol." The father of his childhood friend "disposed of the incriminating walk-in vaults in old NSA HQ at Riverbank Labs....the first overt attempt to voluntarily recruit me was Jan 4, 1967 at that same Riverbank Labs."
The MRU spyentist continues, "I wasn't excited about the spiel Carl [Schleicher] apparently agreed to. I had been warned two years previously by Dale Williams, son of Riverbank director, and also in 6th grade by Mrs. Jones, former OSS cipherhead. I took those warnings lightly until personnel got used up due to Viet Nam and TEXACO-linked side of NSA started using heavier tactics like extortion, threats and financial incentives. The author, William Shirer and son in law of Joe McCarthy (William Tierney) were both close friends of Friedman but never disclosed that, as far as I know. Shirer almost killed himself because he thought nobody would read Rise and Fall of Third Reich; he was also an associate of NSA/Norris at Tribune. I am pleased to contest any difference between what I say and NSA official version, with perfect confidence. They probably they won't even try. You might see that I fill in the large blank spots in official history." "Don't ever think that NSA began in 1952. I've seen their charter and it isn't the public one. Until 1970, NSA considered themselves the real OSS and they were run until 1990 by about 10 military men most of whom were among the few who managed to fight back effectively on Dec 7, 1941. They considered NSA Directors and US Presidents to be hired help and figureheads. BTW, Elizebeth Smith Friedman was a cousin of Dan Quayle's wife."
Long Range Acoustic Devices are now used for crowd control along with other Directed Energy Weapons (DEW). Ultrasound is cyclic sound pressure with a frequency greater than the upper limit of human hearing. Although this limit varies from person to person, it is approximately 20 kilohertz (20,000 hertz) in healthy, young adults and thus, 20 kHz serves as a useful lower limit in describing ultrasound. The production of ultrasound is used in many different fields, typically to penetrate a medium and measure the reflection signature or supply focused energy. The reflection signature can reveal details about the inner structure of the medium, a property also used by animals such as bats for hunting. The most well known application of ultrasound is its use in sonography to produce pictures of foetuses in the human womb. There are a vast number of other applications as well.
Chronovision allegedly came from the Vatican-based music experiments in the 50s. Chronovisor, a type of time machine which would bring pictures and sounds from the past into the present. Looking a bit like a television, the machine worked by detecting all the sights and sounds that humanity had made that still floated through space. The Chronovisor was portrayed as a large cabinet with a normal cathode ray tube for viewing the received events and a series of buttons, levers, and other controls for selecting the time and the location to be viewed. It could also focus and track specific people. According to its inventor, Father Pellegrino Ernetti, it worked by receiving, decoding and reproducing the electromagnetic radiation left behind from past events, though it could also pick up sound waves. Ernetti began by filtering harmonics from Gregorian chants. Instead they heard paranormal voices. The Pope wanted them to confirm faith in the Beyond.
Ernetti formulated theories to answer the questions: what happened to all the sights and sounds humans make? Did they disappear completely or do they continue to exist in some way? Through Papal connections and backing, he was introduced to a team of 12 of the world’s greatest scientific minds in order to further this research. A team which included Enrico Fermi, winner of the Nobel Prize for Physics in 1938 and designer of the world’s first nuclear reactor, as well as NASA rocket scientist Werner Von Braun, former SS Colonel, head of the Nazi rocket program and later the man who would lead the American Apollo space program. The research was conducted in complete secrecy, with no leaks or mentions made until the early 1960’s. The machine was supposedly destroyed.
It is possible that time travel was also investigated earlier at Riverbank Labs as there is a similarity to acoustics and music.
It does appear that levitation was also developed there. There is a relationship between standing waves and musical instruments. Resonance is a fundamental principle from micro to macrocosm as are harmonics. Musical tones are produced by musical instruments, or by the voice, which, from a physics perspective, is a very complex wind instrument. So the physics of music is the physics of the kinds of sounds these instruments can make. What kinds of sounds are these? They are tones caused by standing waves produced in or on the instrument. So the properties of these standing waves, which are always produced in very specific groups, or series, have far-reaching effects on music theory.
Most sound waves, including the musical sounds that actually reach our ears, are not standing waves. Normally, when something makes a wave, the wave travels outward, gradually spreading out and losing strength, like the waves moving away from a pebble dropped into a pond. But when the wave encounters something, it can bounce (reflection) or be bent (refraction). In fact, you can "trap" waves by making them bounce back and forth between two or more surfaces. Musical instruments take advantage of this; they produce pitches by trapping sound waves. Why are trapped waves useful for music? Any bunch of sound waves will produce some sort of noise. But to be a tone - a sound with a particular pitch - a group of sound waves has to be very regular, all exactly the same distance apart. That's why we can talk about the frequency and wavelength of tones.
You can produce a tone in a sound wave trap and keep sending more sound waves into it. Picture a lot of pebbles dropped into a very small pool. As the waves start reflecting off the edges of the pond, they interfere with the new waves, making a jumble of waves that partly cancel each other out and mostly just roils the pond - noise. But if you arrange the waves so that reflecting waves, instead of canceling out the new waves reinforce them, the high parts of the reflected waves meet the high parts of the oncoming waves and make them even higher. The low parts of the reflected waves would meet the low parts of the oncoming waves and make them even lower. Instead of a roiled mess of waves canceling each other out, we find a pond of perfectly ordered waves, with high points and low points appearing regularly at the same spots again and again. A single wave can reflect back and forth and standing waves.
Riverbank Lab was a giant resonant chamber, essentially an acoustic instrument.
Orderliness is actually hard to get from water waves, but relatively easy to get in sound waves, so that several completely different types of sound wave "containers" have been developed into musical instruments. The two most common are strings and hollow tubes. In order to get the necessary constant reinforcement, the container has to be the perfect size (length) for a certain wavelength, so that waves bouncing back or being produced at each end reinforce each other, instead of interfering with each other and canceling each other out. And it really helps to keep the container very narrow, so that you don't have to worry about waves bouncing off the sides and complicating things. So you have a bunch of regularly-spaced waves that are trapped, bouncing back and forth in a container that fits their wavelength perfectly. If you could watch these waves, it would not even look as if they are traveling back and forth. Instead, waves would seem to be appearing and disappearing regularly at exactly the same spots, so these trapped waves are called standing waves.
According to Charles Stone, Enrico Fermi was involved in acoustics and time travel. Riverbank was for many years the leading acoustics testing facility in the world. So that fits in with the time travel story. Riverbank is operated or maintained now by a medium sized high tech company in Tyson's Corner. The CEO was formerly the President of Illinois Institute of Technology which is closely linked to Riverbank. I know most of the senior Execs of the company of which a number are retired Navy and Army officers. The CEO even calls his own home The Villa, like the residence at Riverbank.
Iona Miller reports from 2008-2010 contact with Black Swan "Julian West": "This is of utmost importance to one of my own obsessive investigations. My paternal grandfather worked at the legendary Riverbank Labs for the infamous Col. George Fabyan. One of the many controversial/occult studies undertaken at Riverbank was the attempt to prove that Shakespeare was Bacon. (Elizebeth Friedman, for example, was one of Fabyan's most important colleagues. It is through her work that a connection can be established between Fabyan and Atlantis-scholar Ignatius Donnelly.)
Also conducted at Riverbank: Experiments in teleportation and acoustic time-travel via the use of acoustics.
Quantum teleportation of electrons in quantum wires with surface acoustic waves. lionization and trigger the formation of ion-acoustic oscillations. The external triggers may initiate spontaneous teleportation. In 1931, Charles Fort, an American writer, tried to describe the random disappearances and appearances of different anomalies. He felt that these sudden disappearances and appearances were connected and therefore felt that they were "teleporting." While he came up with this theory to try and explain why certain paranormal phenomena acted, many suggest that Fort probably didn't subscribe to the theory and was using it as a way of suggesting mainstream science didn't provide enough information on why these phenomena happened.
Dematerialising This is the transmission of data from one area and then the reconstruction of that object at its final destination. This is a theory that is presented in Star Trek when the individuals are "beamed down" to the planet. While the uncertainty principle suggests that humans are unable to be dematerialized because rebuilding their body as perfectly as they had previously been is nearly impossible. However, in 1998, scientists at Caltech were able to make a true teleportation occur. This resulted in energy being transmitted from one point to another with a distance of about one meter. While the scientists admit that it was only one meter, they argue that they feel they could make the energy transmit to distances much larger.
Dimensional Teleportation This theory of teleportation suggests that an object existing in one universe leaves that universe, enters another one and then returns to the original, but in a different place. However, this theory is not considered often because it goes against the argument that time travel is not possible. Wormhole According to some, a wormhole is a shortcut through time and space. It is suggested that an individual could go into a wormhole and this would be the "effective" method of getting from point A to point B without needing any form of time travel machines. However, little is known about whether these wormholes actually exist or not. Is Teleportation Possible? Teleportation has always been a sign of intrigue in the science fiction world; however, there is still little research available to suggest whether teleportation is actually possible. There have been successful experiments, though, that suggest that teleportation is possible. However, since this is only energy, it is argued that it would take a considerable amount of time to create a method of teleporting an individual. Even then, there are so many theories that suggest that it is impossible because regnerating a human would be nearly impossible.
West continues, "My grandfather had a very old set of Shakespeare's complete works (heavily annotated in more than one handwriting), which is now unfortunately lost, due to the ignorance and carelessness of his widow. (He never discussed the true nature of his work with his family; I myself have spent free time over several years just beginning to gather some real facts together (--discovering your work, linking Bacon to St. Germain, may be a big breakthrough in this research into the true nature and import of the experimental research conducted at Riverbank)). I also have in my own possession a few artifacts from Fabyan's estate, which came down from my grandfather."
Ms. Miller began investigating Riverbank Labs in 2006 with another high IQ MRU alumni, a spy-entist with intelligence connections, (a former military intel internal security officer) responding to questions about the NSA cryptographer in Dan Brown's proposal on "Solomon's Key" which appeared later as the book "Lost Symbol." The father of his childhood friend "disposed of the incriminating walk-in vaults in old NSA HQ at Riverbank Labs....the first overt attempt to voluntarily recruit me was Jan 4, 1967 at that same Riverbank Labs."
The MRU spyentist continues, "I wasn't excited about the spiel Carl [Schleicher] apparently agreed to. I had been warned two years previously by Dale Williams, son of Riverbank director, and also in 6th grade by Mrs. Jones, former OSS cipherhead. I took those warnings lightly until personnel got used up due to Viet Nam and TEXACO-linked side of NSA started using heavier tactics like extortion, threats and financial incentives. The author, William Shirer and son in law of Joe McCarthy (William Tierney) were both close friends of Friedman but never disclosed that, as far as I know. Shirer almost killed himself because he thought nobody would read Rise and Fall of Third Reich; he was also an associate of NSA/Norris at Tribune. I am pleased to contest any difference between what I say and NSA official version, with perfect confidence. They probably they won't even try. You might see that I fill in the large blank spots in official history." "Don't ever think that NSA began in 1952. I've seen their charter and it isn't the public one. Until 1970, NSA considered themselves the real OSS and they were run until 1990 by about 10 military men most of whom were among the few who managed to fight back effectively on Dec 7, 1941. They considered NSA Directors and US Presidents to be hired help and figureheads. BTW, Elizebeth Smith Friedman was a cousin of Dan Quayle's wife."
Long Range Acoustic Devices are now used for crowd control along with other Directed Energy Weapons (DEW). Ultrasound is cyclic sound pressure with a frequency greater than the upper limit of human hearing. Although this limit varies from person to person, it is approximately 20 kilohertz (20,000 hertz) in healthy, young adults and thus, 20 kHz serves as a useful lower limit in describing ultrasound. The production of ultrasound is used in many different fields, typically to penetrate a medium and measure the reflection signature or supply focused energy. The reflection signature can reveal details about the inner structure of the medium, a property also used by animals such as bats for hunting. The most well known application of ultrasound is its use in sonography to produce pictures of foetuses in the human womb. There are a vast number of other applications as well.
Founding of NSA in Cryptoanalysis

DEAN OF CRYPTOLOGY - National Security Agency Bust of Friedman on display at the National Cryptologic Museum, where he is identified as the "Dean of American Cryptology". Following World War II, Friedman remained in government signals intelligence. In 1949 he became head of the cryptographic division of the newly-formed Armed Forces Security Agency (AFSA) and in 1952 became chief cryptologist for the National Security Agency (NSA) when it was formed to take over from AFSA. Friedman produced a classic series of textbooks, "Military Cryptanalysis", which was used to train NSA students. (These were revised and extended, under the title "Military Cryptanalytics", by Friedman's assistant and successor Lambros D. Callimahos, and used to train many additional cryptanalysts.) During his early years at NSA, he encouraged it to develop what was probably the first super-computers, although he was never convinced a machine could have the "insight" of a human mind.
Friedman retired in 1956 and, with his wife, turned his attention to the problem that had originally brought them together: examining Bacon's supposed codes. Together they wrote a book entitled The Cryptologist Looks at Shakespeare which won a prize from the Folger Library and was published under the title The Shakespearean Ciphers Examined. The book demonstrated flaws in Gallup's work and in that of others who sought hidden ciphers in Shakespeare's work.
At NSA's request Friedman prepared Six Lectures Concerning Cryptography and Cryptanalysis, which he delivered at NSA. But later the Agency, concerned about security, confiscated the reference materials from Friedman's home.
Friedman retired in 1956 and, with his wife, turned his attention to the problem that had originally brought them together: examining Bacon's supposed codes. Together they wrote a book entitled The Cryptologist Looks at Shakespeare which won a prize from the Folger Library and was published under the title The Shakespearean Ciphers Examined. The book demonstrated flaws in Gallup's work and in that of others who sought hidden ciphers in Shakespeare's work.
At NSA's request Friedman prepared Six Lectures Concerning Cryptography and Cryptanalysis, which he delivered at NSA. But later the Agency, concerned about security, confiscated the reference materials from Friedman's home.
TOP CODEBREAKERS

William Frederick Friedman (September 24, 1891 – November 12, 1969) was a US Army cryptographer who ran the research division of the Army's Signals Intelligence Service (SIS) in the 1930s, and parts of its follow-on services into the 1950s. In the late 1930s, subordinates of his led by Frank Rowlett broke Japan's PURPLE cipher, thus disclosing Japanese diplomatic secrets beginning before World War II era.
Another of Fabyan's pet projects was research into secret messages which Sir Francis Bacon had allegedly hidden in various texts during the reigns of Elizabeth I and James I. The research was carried out by Elizabeth Wells Gallup. She believed that she had discovered many such messages in the works of William Shakespeare, and convinced herself that Bacon had written many, if not all, of Shakespeare's works. Friedman had become something of an expert photographer while working on his other projects, and was asked to travel to England on several occasions to help Gallup photograph historical manuscripts during her research. He became fascinated with the work as he courted Elizebeth Smith, Mrs. Gallup's assistant and an accomplished cryptographer. They married, and he soon became director of Riverbank's Department of Codes and Ciphers as well as its Department of Genetics. During this time, Friedman wrote a series of 23 papers on cryptography, collectively known as the "Riverbank publications", included the first description of the index of coincidence, an important mathematical tool in cryptanalysis.
With the entry of the United States into World War I, Fabyan offered the services of his Department of Codes and Ciphers to the government. No Federal department existed for this kind of work (although both the Army and Navy had had embryonic departments at various times), and soon Riverbank became the unofficial cryptographic center for the US Government. During this period, the Friedmans broke a code used by German-funded Hindu radicals in the US who planned to ship arms to India to gain independence from Britain. Analyzing the format of the messages, Riverbank realized that the code was based on a dictionary of some sort, a cryptographic technique common at the time. The Friedmans soon managed to decrypt most of the messages, but only long after the case had come to trial did the book itself come to light: a German-English dictionary published in 1880.
Friedman turned out to be the true find. He fell in love with cryptographer Elizebeth Smith, and taught himself her specialty in a matter of weeks. He soon proved capable of cracking Britain's most sophisticated field code at a speed that was previously believed impossible. But as Friedman improved the code-breaking, Gallup's anticipated breakthrough on the authorship question failed to occur. The cryptanalysis simply didn't find anything useful and Friedman began to suspect that no cipher existed. After retirement, he and his wife returned to the Baconian ciphers. They proved false the Baconian theory in an incisive report that won them the Folger Shakespeare Library literary prize in 1955. This work was published in 1957 as "The Shakespearean Ciphers Examined."
The cryptology project might have dissolved had the United States not entered World War I in April 1917. The federal government had virtually no cryptographers, and Fabyan had plenty, so Riverbank became the NSA of its day. Newlyweds William and Elizebeth Friedman were soon cracking German and Mexican codes for the U.S. military and helping Scotland Yard expose anti-British agents in North America. When the U.S. Army finally established its own Cipher Bureau, its first 88 officers were trained by Fabyan and the Friedmans at Riverbank. When they graduated, William Friedman took a commission himself and went to France. William Friedman became the nation's top code breaker and led the successful effort to crack the Japanese codes before World War II. Elizebeth Friedman did her code breaking for the Coast Guard and the Treasury Department, and later established a secure communications system for the International Monetary Fund.
William Frederick Friedman (September 24, 1891 - November 12, 1969) served as a US Army cryptologist, running the research division of the Army's Signals Intelligence Service through the 1930s and its follow-on services right into the 1950s. He supervised the breaking of the Japanese Purple code in the late 1930s. Frank Rowlett led the SIS team which cracked the cypher machine. The output provided considerable information about Japanese diplomacy at the highest level througout World War II and afterwards, until Congressional hearings made public the fact that the US had been reading messages processed by that crypto system. Many consider Friedman one of the greatest cryptologists of all time, and his application of statistical methods to code-breaking one of the most significant advances in the field. He also coined much of the language used in decryption, introducing terms such as cryptography and cryptanalysis.
Friedman was born in Russia, the son of a postal worker who migrated to Pittsburgh in 1892. He studied at the Michigan Agricultural College in East Lansing and received a scholarship to work on genetics at Cornell University . Meanwhile George Fabyan, who ran a private research laboratory to study any project that caught his fancy, decided to set up his own genetics project and was referred to Friedman. Friedman joined Fabyan's Riverbank Laboratories outside Chicago in September 1915. As head of the Department of Genetics, one of the projects he ran studied the effects of moonlight on crop growth, and so he experimented with the planting of wheat during various phases of the moon.
Another of Fabyan's pet projects funded Elizabeth Wells Gallup's research into the coded messages which Sir Francis Bacon had allegedly hidden in various texts during the reign of Elizabeth I and King James. Believing that she had detected that many of Shakespeare's works also included such hidden messages, Gallup became convinced that Bacon wrote many, if not all, of William Shakespeare's works. Friedman had become something of an expert photographer while working on his other projects, and was asked to travel to England on several occasions to help Gallup photograph historical manuscripts during her research. At this point he became fascinated with cryptology, while he courted Elizebeth Smith, Mrs. Gallup's assistant and an accomplished cryptologist. They married, and soon after he became the director of the Department of Codes and Ciphers as well as of the Department of Genetics at Riverbank.
With the US's entry into World War I, Fabyan offered the services of his Department of Codes and Ciphers to the government. No Federal department existed for this kind of work (although both the Army and the Navy had had embryonic departments at various times), and soon Riverbank became the unofficial cryptographic center for the Federal GovernmentUS. During this period the Friedmans cracked a code used by German-funded Hindu radicals in the US who planned to ship arms to India to gain independence from Britain. Analysing the format of the messages, Riverbank realized that the code was based on a dictionary of some sort, a common encryption technique. The Friedmans soon managed to decode most messages, but only long after the case had come to trial did the book itself come to light: a German-English dictionary published in 1880.
The United States government decided to set up its own code-breaking service, and sent Army officers to Riverbank for training under Friedman. To support their training, Friedman produced a series of technical monographs, completing seven by early 1918. He then enlisted in the Army, and travelled to France to serve as the personal code-breaker for General John Pershing. He returned to the US in 1920 and published an eighth monograph, "The Index of Coincidence and its Applications in Cryptography", which is considered to be the most important single publication in modern cryptology to that time.
In 1921 he joined the government's American Black Chamber where he was placed in charge of researching new codes and ways to break them, and in 1922 he was promoted to head the Research and Development Division. After the dissolution of the Black Chamber in 1929, Friedman moved to the Army's Signals Intelligence Service (SIS) in a similar capacity.
During the 1920s a series of new cyphers processed by machines gained popularity, based largely on typewriter mechanicals attached to basic electrical circuitry - batteries, switches and lights. The first of such machines had been the Hebern Rotor Machine, designed in the US in 1915 by Edward Hebern. This system offered such security and simplicity of use that Hebern heavily promoted his company to investors, feeling that all companies would soon be using them and his company would clearly be successful. But the company went bankrupt when the war ended, and Hebern eventually landed in prison, convicted of stock manipulation.
Friedman realized that the new rotor machines would be important, and devoted some time to cracking Hebern's design. Over a period of years he discovered a number of problems common to most of the rotor machine designs. Examples of some dangerous features included having the rotors turn once with every keypress, and making the fast rotor (the one that turns with every keypress) at either end of the rotor stack. In this case the output generated by the machines will have strings of 26 letters that form a simple substitution cipher, and by collecting enough cyphertext and applying a standard statistical method known as the kappa test, he showed that he could, albeit with great difficulty, crack any code generated by such a machine.
Friedman then used his understanding of the rotor machines to develop several of his own that remained immune to his own attacks. He eventually developed nine designs, six of which remain still secret today. Some of his inventions while developing these systems only gained patents decades later, since the Defense Department regarded them as so critical that granting a patent would harm national security. The culmination of various earlier designs resulted in the SIGABA, which became the US's highest security encryption system during World War II. It was similar to the British Typex machine, and adapters were apparetnly built which could allow the two machines to interoperate. Neither was, as far as is publicly known, broken during WWII. In fact, SIGABA would still be quite good tady, in the computer era. computers.
In 1939 the Japanese introduced a new cypher machine system for their most secure diplomatic traffic to and from important embassies, replacing an earlier system SIS referred to as Red. The new cypher, referred to as Purple, proved quite difficult to crack. The Navy's OP-20-G and the SIS thought it might relate to the earlier mechanical cypher machines, and the SIS set about attacking it. After spending several months studying the cyphertexts and trying to discover the underlying patterns. Eventually, in an extraordianry achievement, the SIS team figured it out. Like the some of the prior Japanese designs, Purple didn't use 'rotors' unlike the German Enigma or the Hebern design, but used stepper switches like those used in automated telephone exchanges. Leo Rosen of the SIS built a machine and, astonishingly, used the same telephone stepper switch that the Japanese designer had used.
By the end of 1940 Friedman's team at the SIS had constructed an exact duplicate of the Purple machine, even though they had never seen one. With an understanding of Purple and duplicate machines of their own to use, the SIS could then decrypt an increasing amount of the Japanese traffic. One such intercept was the message to the Japanese Embassy in Washington ordering an end (on December 7th 1941) to the negotiations with the US. The message gave a clear indication of impending war, and was to have been delivered to the US State Department only hours prior to the attack on Pearl Harbor.
The pressure of his responsibilites, including the Purple effort was too much and Friedman entered a hospital in 1941 with a nervous breakdown. After his release, he served as Director of Communications Research for the SIS for the rest of the war. Friedman visited the British code-breaking operations at the Government Code and Cipher School at Bletchley Park in 1941. He exchanged information on the techniques for attacking Purple for the British information on how they had broken the Enigma.
Following the WWII, Friedman remained in government signals intelligence. In 1949 he became head of the code division of the newly-formed Armed Forces Security Agency (AFSA), and in 1952 become the chief cryptologist for the National Security Agency (NSA) when it formed to take over from the AFSA.
Friedman retired in 1956 and turned his attention, with his wife, to the problem that had originally brought them together: examining Bacon's codes. In 1957 they wrote The Shakespearean Ciphers Examined, in which they demonstrated unfortunate flaws in Gallup's work. His health began to fail in the late 1960s, and he died in 1969.
Elizebeth Friedman was also heavily involved in cryptography throughout much of the inter-War period, although typically on the civilian side. During the 1920s she gained some fame for repeatedly breaking the cyphers and codes being used by "rum runners" bringing alcohol into the US during Prohibition, and in 1927 the US Coast Guard hired her to help them with their policing operations. By 1930 she had cracked over 12,000 messages for the Coast Guard, the Bureau of Customs, the Bureau of Narcotics, the Bureau of Prohibition, the Bureau of Internal Revenue, and the Department of Justice.
In 1934 she became involved in a particularly odd case, in which a Canadian-registered ship, the I'm Alone, sank after being chased into international waters off the US. She decoded several messages that demonstrated that a US citizen had actually paid for the ship, which therefore had ostensibe US-ownership. The result expanded the law regarding police chases, allowing a ship involved in illegal activity to be followed into international waters, and thereby extracting the US from an embarrassing political scandal.
During World War II Elizebeth Friedman moved to the OSS and became one of their chief cryptologists. She became involved in a particularly famous case in which a husband-and-wife team were sending coded messages to the Japanese, written on dolls that the wife sold through a thriving mail-order business. Velvalee Dickinson became known as "The Doll Woman" when the case was broken to the press. Elizebeth retired after her husband's death in 1969 and lived on until 1980.
* http://www.nsa.gov/honor/w_friedman.html
* http://www.sans.org/rr/history/friedman.php
In 1929, Secretary of State Henry L. Stimson withdrew the Bureau's funds, on the ground that "gentlemen do not read each other's mail." Yardley, jobless in the Depression, awoke America to the importance of cryptology in his best-selling The American Black Chamber (1931). His bureau's work was assumed by the army's tiny Signal Intelligence Service (SIS) under the brilliant cryptologist William F. Friedman. During World War I, Friedman, at the Riverbank Laboratories, a think tank near Chicago, had broken new paths for cryptanalysis; soon after he joined the War Department as a civilian employee in 1921, he reconstructed the locations and starting positions of the rotors in a cipher machine. His work placed the United States at the forefront of world cryptology.
Beginning in 1931, he expanded the SIS, hiring mathematicians first. By 1940, a team under the cryptanalyst Frank B. Rowlett had reconstructed the chief Japanese diplomatic cipher machine, which the Americans called purple. These solutions could not prevent Pearl Harbor because no messages saying anything like "We will attack Pearl Harbor" were ever transmitted; the Japanese diplomats themselves were not told of the attack. Later in the war, however, the solutions of the radiograms of the Japanese ambassador in Berlin, enciphered in purple, provided the Allies with what Army Chief of Staff General George C. Marshall called "our main basis of information regarding Hitler's intentions in Europe." One revealed details of Hitler's Atlantic Wall defenses.
The U.S. Navy's OP-20-G, established in 1924 under Lieutenant Laurence F. Safford, solved Japanese naval codes. This work flowered when the solutions of its branch in Hawaii made possible the American victory at Midway in 1942, the midair shootdown of Admiral Isoroku Yamamoto in 1943, and the sinking of Japanese freighters throughout the Pacific war, strangling Japan. Its headquarters in Washington cooperated with the British code breaking agency, the Government Code and Cypher School, at Bletchley Park, northwest of London, to solve U-boat messages encrypted in the Enigma rotor cipher machine. This enabled Allied convoys to dodge wolf packs and so help win the Battle of the Atlantic. Teams of American cryptanalysts and tabulating machine engineers went to the British agency to cooperate in solving German Enigma and other cipher systems, shortening the land war in Europe. No other source of information— not spies, aerial photographs, or prisoner interrogations—provided such trustworthy, high-level, voluminous, detailed, and prompt intelligence as code breaking.
Wallace Clement Sabine (1868-1919)
Sabine's Reverberation Formula
Wallace Clement Sabine was a pioneer in architectural acoustics. A century ago he started experiments in the Fogg lecture room at Harvard, to investigate the impact of absorption on the reverberation time. It was on the 29th of October 1898 that he discovered the type of relation between these quantities. Sabine derived an expression for the duration T of the residual sound to decay below the audible intensity, starting from a 1,000,000 times higher initial intensity:
T = 0.161 V/A
where V is the room volume in cubic meters, and A is the total absorption in square meters. Sabine's reverberation formula has been applied successfully for many years to determine material absorption coefficients by means of reverberation rooms. Keeping in mind some conditions with regard to the sound field diffusion and the value of A, Sabine's formula is still widely accepted as a very useful estimation method for the reverberation time in rooms.
Sabin as Unit of Sound Absorption
The unit of sound absorption is square meter, referring to the area of open window. This unit stems from the fact that sound energy travelling toward an open window in a room will not be reflected at all, but completely disappear in the open air outside. The effect would be the same if the open window would be replaced with 100 % absorbing material of the same dimensions.
Therefore, 1 square meter of 100 % absorbing material has an absorption of 1 square meter of open window. In honor of W.C. Sabine, the unit of absorption is also named sabin or metric sabin. However, these units are used not very often. One sabin is the absorption of one square foot of open window, and one metric sabin is the absorption of one square meter of open window.
Symphony Hall
The first auditorium that was designed by Sabine, applying his new insight in acoustics, was the new Boston Music Hall, currently known as the Symphony Hall. It was formally opened on October 15, 1900. Nowadays, it is still considered one of the three finest concert halls in the world.
Another of Fabyan's pet projects was research into secret messages which Sir Francis Bacon had allegedly hidden in various texts during the reigns of Elizabeth I and James I. The research was carried out by Elizabeth Wells Gallup. She believed that she had discovered many such messages in the works of William Shakespeare, and convinced herself that Bacon had written many, if not all, of Shakespeare's works. Friedman had become something of an expert photographer while working on his other projects, and was asked to travel to England on several occasions to help Gallup photograph historical manuscripts during her research. He became fascinated with the work as he courted Elizebeth Smith, Mrs. Gallup's assistant and an accomplished cryptographer. They married, and he soon became director of Riverbank's Department of Codes and Ciphers as well as its Department of Genetics. During this time, Friedman wrote a series of 23 papers on cryptography, collectively known as the "Riverbank publications", included the first description of the index of coincidence, an important mathematical tool in cryptanalysis.
With the entry of the United States into World War I, Fabyan offered the services of his Department of Codes and Ciphers to the government. No Federal department existed for this kind of work (although both the Army and Navy had had embryonic departments at various times), and soon Riverbank became the unofficial cryptographic center for the US Government. During this period, the Friedmans broke a code used by German-funded Hindu radicals in the US who planned to ship arms to India to gain independence from Britain. Analyzing the format of the messages, Riverbank realized that the code was based on a dictionary of some sort, a cryptographic technique common at the time. The Friedmans soon managed to decrypt most of the messages, but only long after the case had come to trial did the book itself come to light: a German-English dictionary published in 1880.
Friedman turned out to be the true find. He fell in love with cryptographer Elizebeth Smith, and taught himself her specialty in a matter of weeks. He soon proved capable of cracking Britain's most sophisticated field code at a speed that was previously believed impossible. But as Friedman improved the code-breaking, Gallup's anticipated breakthrough on the authorship question failed to occur. The cryptanalysis simply didn't find anything useful and Friedman began to suspect that no cipher existed. After retirement, he and his wife returned to the Baconian ciphers. They proved false the Baconian theory in an incisive report that won them the Folger Shakespeare Library literary prize in 1955. This work was published in 1957 as "The Shakespearean Ciphers Examined."
The cryptology project might have dissolved had the United States not entered World War I in April 1917. The federal government had virtually no cryptographers, and Fabyan had plenty, so Riverbank became the NSA of its day. Newlyweds William and Elizebeth Friedman were soon cracking German and Mexican codes for the U.S. military and helping Scotland Yard expose anti-British agents in North America. When the U.S. Army finally established its own Cipher Bureau, its first 88 officers were trained by Fabyan and the Friedmans at Riverbank. When they graduated, William Friedman took a commission himself and went to France. William Friedman became the nation's top code breaker and led the successful effort to crack the Japanese codes before World War II. Elizebeth Friedman did her code breaking for the Coast Guard and the Treasury Department, and later established a secure communications system for the International Monetary Fund.
William Frederick Friedman (September 24, 1891 - November 12, 1969) served as a US Army cryptologist, running the research division of the Army's Signals Intelligence Service through the 1930s and its follow-on services right into the 1950s. He supervised the breaking of the Japanese Purple code in the late 1930s. Frank Rowlett led the SIS team which cracked the cypher machine. The output provided considerable information about Japanese diplomacy at the highest level througout World War II and afterwards, until Congressional hearings made public the fact that the US had been reading messages processed by that crypto system. Many consider Friedman one of the greatest cryptologists of all time, and his application of statistical methods to code-breaking one of the most significant advances in the field. He also coined much of the language used in decryption, introducing terms such as cryptography and cryptanalysis.
Friedman was born in Russia, the son of a postal worker who migrated to Pittsburgh in 1892. He studied at the Michigan Agricultural College in East Lansing and received a scholarship to work on genetics at Cornell University . Meanwhile George Fabyan, who ran a private research laboratory to study any project that caught his fancy, decided to set up his own genetics project and was referred to Friedman. Friedman joined Fabyan's Riverbank Laboratories outside Chicago in September 1915. As head of the Department of Genetics, one of the projects he ran studied the effects of moonlight on crop growth, and so he experimented with the planting of wheat during various phases of the moon.
Another of Fabyan's pet projects funded Elizabeth Wells Gallup's research into the coded messages which Sir Francis Bacon had allegedly hidden in various texts during the reign of Elizabeth I and King James. Believing that she had detected that many of Shakespeare's works also included such hidden messages, Gallup became convinced that Bacon wrote many, if not all, of William Shakespeare's works. Friedman had become something of an expert photographer while working on his other projects, and was asked to travel to England on several occasions to help Gallup photograph historical manuscripts during her research. At this point he became fascinated with cryptology, while he courted Elizebeth Smith, Mrs. Gallup's assistant and an accomplished cryptologist. They married, and soon after he became the director of the Department of Codes and Ciphers as well as of the Department of Genetics at Riverbank.
With the US's entry into World War I, Fabyan offered the services of his Department of Codes and Ciphers to the government. No Federal department existed for this kind of work (although both the Army and the Navy had had embryonic departments at various times), and soon Riverbank became the unofficial cryptographic center for the Federal GovernmentUS. During this period the Friedmans cracked a code used by German-funded Hindu radicals in the US who planned to ship arms to India to gain independence from Britain. Analysing the format of the messages, Riverbank realized that the code was based on a dictionary of some sort, a common encryption technique. The Friedmans soon managed to decode most messages, but only long after the case had come to trial did the book itself come to light: a German-English dictionary published in 1880.
The United States government decided to set up its own code-breaking service, and sent Army officers to Riverbank for training under Friedman. To support their training, Friedman produced a series of technical monographs, completing seven by early 1918. He then enlisted in the Army, and travelled to France to serve as the personal code-breaker for General John Pershing. He returned to the US in 1920 and published an eighth monograph, "The Index of Coincidence and its Applications in Cryptography", which is considered to be the most important single publication in modern cryptology to that time.
In 1921 he joined the government's American Black Chamber where he was placed in charge of researching new codes and ways to break them, and in 1922 he was promoted to head the Research and Development Division. After the dissolution of the Black Chamber in 1929, Friedman moved to the Army's Signals Intelligence Service (SIS) in a similar capacity.
During the 1920s a series of new cyphers processed by machines gained popularity, based largely on typewriter mechanicals attached to basic electrical circuitry - batteries, switches and lights. The first of such machines had been the Hebern Rotor Machine, designed in the US in 1915 by Edward Hebern. This system offered such security and simplicity of use that Hebern heavily promoted his company to investors, feeling that all companies would soon be using them and his company would clearly be successful. But the company went bankrupt when the war ended, and Hebern eventually landed in prison, convicted of stock manipulation.
Friedman realized that the new rotor machines would be important, and devoted some time to cracking Hebern's design. Over a period of years he discovered a number of problems common to most of the rotor machine designs. Examples of some dangerous features included having the rotors turn once with every keypress, and making the fast rotor (the one that turns with every keypress) at either end of the rotor stack. In this case the output generated by the machines will have strings of 26 letters that form a simple substitution cipher, and by collecting enough cyphertext and applying a standard statistical method known as the kappa test, he showed that he could, albeit with great difficulty, crack any code generated by such a machine.
Friedman then used his understanding of the rotor machines to develop several of his own that remained immune to his own attacks. He eventually developed nine designs, six of which remain still secret today. Some of his inventions while developing these systems only gained patents decades later, since the Defense Department regarded them as so critical that granting a patent would harm national security. The culmination of various earlier designs resulted in the SIGABA, which became the US's highest security encryption system during World War II. It was similar to the British Typex machine, and adapters were apparetnly built which could allow the two machines to interoperate. Neither was, as far as is publicly known, broken during WWII. In fact, SIGABA would still be quite good tady, in the computer era. computers.
In 1939 the Japanese introduced a new cypher machine system for their most secure diplomatic traffic to and from important embassies, replacing an earlier system SIS referred to as Red. The new cypher, referred to as Purple, proved quite difficult to crack. The Navy's OP-20-G and the SIS thought it might relate to the earlier mechanical cypher machines, and the SIS set about attacking it. After spending several months studying the cyphertexts and trying to discover the underlying patterns. Eventually, in an extraordianry achievement, the SIS team figured it out. Like the some of the prior Japanese designs, Purple didn't use 'rotors' unlike the German Enigma or the Hebern design, but used stepper switches like those used in automated telephone exchanges. Leo Rosen of the SIS built a machine and, astonishingly, used the same telephone stepper switch that the Japanese designer had used.
By the end of 1940 Friedman's team at the SIS had constructed an exact duplicate of the Purple machine, even though they had never seen one. With an understanding of Purple and duplicate machines of their own to use, the SIS could then decrypt an increasing amount of the Japanese traffic. One such intercept was the message to the Japanese Embassy in Washington ordering an end (on December 7th 1941) to the negotiations with the US. The message gave a clear indication of impending war, and was to have been delivered to the US State Department only hours prior to the attack on Pearl Harbor.
The pressure of his responsibilites, including the Purple effort was too much and Friedman entered a hospital in 1941 with a nervous breakdown. After his release, he served as Director of Communications Research for the SIS for the rest of the war. Friedman visited the British code-breaking operations at the Government Code and Cipher School at Bletchley Park in 1941. He exchanged information on the techniques for attacking Purple for the British information on how they had broken the Enigma.
Following the WWII, Friedman remained in government signals intelligence. In 1949 he became head of the code division of the newly-formed Armed Forces Security Agency (AFSA), and in 1952 become the chief cryptologist for the National Security Agency (NSA) when it formed to take over from the AFSA.
Friedman retired in 1956 and turned his attention, with his wife, to the problem that had originally brought them together: examining Bacon's codes. In 1957 they wrote The Shakespearean Ciphers Examined, in which they demonstrated unfortunate flaws in Gallup's work. His health began to fail in the late 1960s, and he died in 1969.
Elizebeth Friedman was also heavily involved in cryptography throughout much of the inter-War period, although typically on the civilian side. During the 1920s she gained some fame for repeatedly breaking the cyphers and codes being used by "rum runners" bringing alcohol into the US during Prohibition, and in 1927 the US Coast Guard hired her to help them with their policing operations. By 1930 she had cracked over 12,000 messages for the Coast Guard, the Bureau of Customs, the Bureau of Narcotics, the Bureau of Prohibition, the Bureau of Internal Revenue, and the Department of Justice.
In 1934 she became involved in a particularly odd case, in which a Canadian-registered ship, the I'm Alone, sank after being chased into international waters off the US. She decoded several messages that demonstrated that a US citizen had actually paid for the ship, which therefore had ostensibe US-ownership. The result expanded the law regarding police chases, allowing a ship involved in illegal activity to be followed into international waters, and thereby extracting the US from an embarrassing political scandal.
During World War II Elizebeth Friedman moved to the OSS and became one of their chief cryptologists. She became involved in a particularly famous case in which a husband-and-wife team were sending coded messages to the Japanese, written on dolls that the wife sold through a thriving mail-order business. Velvalee Dickinson became known as "The Doll Woman" when the case was broken to the press. Elizebeth retired after her husband's death in 1969 and lived on until 1980.
* http://www.nsa.gov/honor/w_friedman.html
* http://www.sans.org/rr/history/friedman.php
In 1929, Secretary of State Henry L. Stimson withdrew the Bureau's funds, on the ground that "gentlemen do not read each other's mail." Yardley, jobless in the Depression, awoke America to the importance of cryptology in his best-selling The American Black Chamber (1931). His bureau's work was assumed by the army's tiny Signal Intelligence Service (SIS) under the brilliant cryptologist William F. Friedman. During World War I, Friedman, at the Riverbank Laboratories, a think tank near Chicago, had broken new paths for cryptanalysis; soon after he joined the War Department as a civilian employee in 1921, he reconstructed the locations and starting positions of the rotors in a cipher machine. His work placed the United States at the forefront of world cryptology.
Beginning in 1931, he expanded the SIS, hiring mathematicians first. By 1940, a team under the cryptanalyst Frank B. Rowlett had reconstructed the chief Japanese diplomatic cipher machine, which the Americans called purple. These solutions could not prevent Pearl Harbor because no messages saying anything like "We will attack Pearl Harbor" were ever transmitted; the Japanese diplomats themselves were not told of the attack. Later in the war, however, the solutions of the radiograms of the Japanese ambassador in Berlin, enciphered in purple, provided the Allies with what Army Chief of Staff General George C. Marshall called "our main basis of information regarding Hitler's intentions in Europe." One revealed details of Hitler's Atlantic Wall defenses.
The U.S. Navy's OP-20-G, established in 1924 under Lieutenant Laurence F. Safford, solved Japanese naval codes. This work flowered when the solutions of its branch in Hawaii made possible the American victory at Midway in 1942, the midair shootdown of Admiral Isoroku Yamamoto in 1943, and the sinking of Japanese freighters throughout the Pacific war, strangling Japan. Its headquarters in Washington cooperated with the British code breaking agency, the Government Code and Cypher School, at Bletchley Park, northwest of London, to solve U-boat messages encrypted in the Enigma rotor cipher machine. This enabled Allied convoys to dodge wolf packs and so help win the Battle of the Atlantic. Teams of American cryptanalysts and tabulating machine engineers went to the British agency to cooperate in solving German Enigma and other cipher systems, shortening the land war in Europe. No other source of information— not spies, aerial photographs, or prisoner interrogations—provided such trustworthy, high-level, voluminous, detailed, and prompt intelligence as code breaking.
Wallace Clement Sabine (1868-1919)
Sabine's Reverberation Formula
Wallace Clement Sabine was a pioneer in architectural acoustics. A century ago he started experiments in the Fogg lecture room at Harvard, to investigate the impact of absorption on the reverberation time. It was on the 29th of October 1898 that he discovered the type of relation between these quantities. Sabine derived an expression for the duration T of the residual sound to decay below the audible intensity, starting from a 1,000,000 times higher initial intensity:
T = 0.161 V/A
where V is the room volume in cubic meters, and A is the total absorption in square meters. Sabine's reverberation formula has been applied successfully for many years to determine material absorption coefficients by means of reverberation rooms. Keeping in mind some conditions with regard to the sound field diffusion and the value of A, Sabine's formula is still widely accepted as a very useful estimation method for the reverberation time in rooms.
Sabin as Unit of Sound Absorption
The unit of sound absorption is square meter, referring to the area of open window. This unit stems from the fact that sound energy travelling toward an open window in a room will not be reflected at all, but completely disappear in the open air outside. The effect would be the same if the open window would be replaced with 100 % absorbing material of the same dimensions.
Therefore, 1 square meter of 100 % absorbing material has an absorption of 1 square meter of open window. In honor of W.C. Sabine, the unit of absorption is also named sabin or metric sabin. However, these units are used not very often. One sabin is the absorption of one square foot of open window, and one metric sabin is the absorption of one square meter of open window.
Symphony Hall
The first auditorium that was designed by Sabine, applying his new insight in acoustics, was the new Boston Music Hall, currently known as the Symphony Hall. It was formally opened on October 15, 1900. Nowadays, it is still considered one of the three finest concert halls in the world.
Acoustic Levitation & Nonlinear Sound
Acoustic Levitation: While the Levitation Machine may have never been operational, the groundwork for the principles of acoustic levitation were laid at Riverbank Labs. Acoustic levitation is a method for suspending matter in a medium by using acoustic radiation pressure from intense sound waves in the medium. Acoustic levitation is possible because of the non-linear effects of intense sound waves.
The idea that something so intangible can lift objects can seem unbelievable, but it's a real phenomenon. Acoustic levitation takes advantage of the properties of sound to cause solids, liquids and heavy gases to float. The process can take place in normal or reduced gravity. In other words, sound can levitate objects on Earth or in gas-filled enclosures in space. Scientists have developed a sound generator so powerful its shock waves can stun, and even kill people. Another group of researchers have developed another unusual application for sound: a method of "acoustic levitation" that could help maintain colonies on Mars or the moon by using high-pitched sound waves to remove alien dust.
Wired explains,Blasting a high-pitched noise from a tweeter into a pipe that focuses the sound waves can create enough pressure to lift troublesome alien dust off surfaces, according to a study published January in the Journal of the Acoustical Society of America. Extra-terrestrial missions have been plagued by dust and debris, which cling to rovers and astronauts because lunar and Martian environments lack the Earth's water or atmosphere that can displace the particles.
According to Wired, Electrostatic charging from solar winds and UV radiation on the Moon makes this sharp dust cling to everything, including astronaut suits where it can work its way through the glove air locks. It also sticks to the solar panels that power rovers and other instruments.
See acoustic levitation for yourself in the video below! Using only sound waves, the scientists are able to lift mock "Martian and lunar dust" off of a solar panel. Cool!
WATCH: http://www.huffingtonpost.com/2010/01/20/acoustic-levitation-stere_n_429558.html
To understand how acoustic levitation works, you first need to know a little about gravity, air and sound. First, gravity is a force that causes objects to attract one another. The simplest way to understand gravity is through Isaac Newton's law of universal gravitation. This law states that every particle in the universe attracts every other particle. The more massive an object is, the more strongly it attracts other objects. The closer objects are, the more strongly they attract each other. An enormous object, like the Earth, easily attracts objects that are close to it, like apples hanging from trees. Scientists haven't decided exactly what causes this attraction, but they believe it exists everywhere in the universe.
Second, air is a fluid that behaves essentially the same way liquids do. Like liquids, air is made of microscopic particles that move in relation to one another. Air also moves like water does -- in fact, some aerodynamic tests take place underwater instead of in the air. The particles in gasses, like the ones that make up air, are simply farther apart and move faster than the particles in liquids.
Third, sound is a vibration that travels through a medium, like a gas, a liquid or a solid object. A sound's source is an object that moves or changes shape very rapidly. For example, if you strike a bell, the bell vibrates in the air. As one side of the bell moves out, it pushes the air molecules next to it, increasing the pressure in that region of the air. This area of higher pressure is a compression. As the side of the bell moves back in, it pulls the molecules apart, creating a lower-pressure region called a rarefaction. The bell then repeats the process, creating a repeating series of compressions and rarefactions. Each repetition is one wavelength of the sound wave.
The sound wave travels as the moving molecules push and pull the molecules around them. Each molecule moves the one next to it in turn. Without this movement of molecules, the sound could not travel, which is why there is no sound in a vacuum.Acoustic levitation uses sound traveling through a fluid -- usually a gas -- to balance the force of gravity. On Earth, this can cause objects and materials to hover unsupported in the air. In space, it can hold objects steady so they don't move or drift. The process relies on of the properties of sound waves, especially intense sound waves.
The Physics of Sound Levitation A basic acoustic levitator has two main parts -- a transducer, which is a vibrating surface that makes sound, and a reflector. Often, the transducer and reflector have concave surfaces to help focus the sound. A sound wave travels away from the transducer and bounces off the reflector. Three basic properties of this traveling, reflecting wave help it to suspend objects in midair. First, the wave, like all sound, is a longitudinal pressure wave. In a longitudinal wave, movement of the points in the wave is parallel to the direction the wave travels. It's the kind of motion you'd see if you pushed and pulled one end of a stretched Slinky. Most illustrations, though, depict sound as a transverse wave, which is what you would see if you rapidly moved one end of the Slinky up and down. This is simply because transverse waves are easier to visualize than longitudinal waves.
Second, the wave can bounce off of surfaces. It follows the law of reflection, which states that the angle of incidence -- the angle at which something strikes a surface -- equals the angle of reflection -- the angle at which it leaves the surface. In other words, a sound wave bounces off a surface at the same angle at which it hits the surface. A sound wave that hits a surface head-on at a 90 degree angle will reflect straight back off at the same angle. The easiest way to understand wave reflection is to imagine a Slinky that is attached to a surface at one end. If you picked up the free end of the Slinky and moved it rapidly up and then down, a wave would travel the length of the spring. Once it reached the fixed end of the spring, it would reflect off of the surface and travel back toward you. The same thing happens if you push and pull one end of the spring, creating a longitudinal wave.
Finally, when a sound wave reflects off of a surface, the interaction between its compressions and rarefactions causes interference. Compressions that meet other compressions amplify one another, and compressions that meet rarefactions balance one another out. Sometimes, the reflection and interference can combine to create a standing wave. Standing waves appear to shift back and forth or vibrate in segments rather than travel from place to place. This illusion of stillness is what gives standing waves their name. Standing sound waves have defined nodes, or areas of minimum pressure, and antinodes, or areas of maximum pressure. A standing wave's nodes are at the heart of acoustic levitation. Imagine a river with rocks and rapids. The water is calm in some parts of the river, and it is turbulent in others. Floating debris and foam collect in calm portions of the river. In order for a floating object to stay still in a fast-moving part of the river, it would need to be anchored or propelled against the flow of the water. This is essentially what an acoustic levitator does, using sound moving through a gas in place of water.
Acoustic levitation uses sound pressure to allow objects to float.
By placing a reflector the right distance away from a transducer, the acoustic levitator creates a standing wave. When the orientation of the wave is parallel to the pull of gravity, portions of the standing wave have a constant downward pressure and others have a constant upward pressure. The nodes have very little pressure.
In space, where there is little gravity, floating particles collect in the standing wave's nodes, which are calm and still. On Earth, objects collect just below the nodes, where the acoustic radiation pressure, or the amount of pressure that a sound wave can exert on a surface, balances the pull of gravity. Acoustic Videos Nonlinear Sound and Acoustic Levitation Ordinary standing waves can be relatively powerful. For example, a standing wave in an air duct can cause dust to collect in a pattern corresponding to the wave's nodes. A standing wave reverberating through a room can cause objects in its path to vibrate. Low-frequency standing waves can also cause people to feel nervous or disoriented -- in some cases, researchers find them in buildings people report to be haunted. But these feats are small potatoes compared to acoustic levitation. It takes far less effort to influence where dust settles or to shatter a glass than it takes to lift objects from the ground. Ordinary sound waves are limited by their linear nature. Increasing the amplitude of the wave causes the sound to be louder, but it doesn't affect the shape of the wave form or cause it to be much more physically powerful.
However, extremely intense sounds -- like sounds that are physically painful to human ears -- are usually nonlinear. They can cause disproportionately large responses in the substances they travel through. Some nonlinear affects include:
Other Uses for Nonlinear Sound
Several medical procedures rely on nonlinear acoustics. For example, ultrasound imaging uses nonlinear effects to allow doctors to examine babies in the womb or view internal organs. High-intensity ultrasound waves can also pulverize kidney stones, cauterize internal injuries and destroy tumors. Levitating objects with sound isn't quite as simple as aiming a high-powered transducer at a reflector. Scientists also must use sounds of the correct frequency to create the desired standing wave. Any frequency can produce nonlinear effects at the right volume, but most systems use ultrasonic waves, which are too high-pitched for people to hear. In addition to the frequency and volume of the wave, researchers also must pay attention to a number of other factors:
Other Levitator Setups
Although a levitator with one transducer and one reflector can suspend objects, some setups can increase stability or allow movement. For example, some levitators have three pairs of transducers and reflectors, which are positioned along the X, Y and Z axes. Others have one large transmitter and one small, movable reflector; the suspended object moves when the reflector moves. Objects hover in a slightly different area within the sound field depending on the influence of gravity. It takes more than just ordinary sound waves to supply this amount of pressure.
Some methods can levitate objects without creating sound heard by the human ear such as the one demonstrated at Otsuka Lab,[2] acrylic glass tank to create a large acoustic field. Acoustic levitation is usually used for containerless processing electromagnetic levitation but has the advantage of being able to levitate nonconducting materials. There is no known theoretical limit to what acoustic levitation can lift given enough vibratory sound, but in practice current technology limits the amount that can be lifted by this force to at most a few kilograms.[3] Acoustic levitators are used mostly in industry and for researchers of anti-gravity effects such as NASA; however some are commercially available to the public.Some are silent while others produce some audible sound. There are many ways of creating this effect, from creating a wave underneath the object and reflecting it back to its source, to using an which has become more important of late due to the small size and resistance of microchips and other such things in industry. Containerless processing may also be used for applications requiring very-high-purity materials or chemical reactions too rigorous to happen in a container. This method is harder to control than other methods of containerless processing.
Different forms of levitation have different scientific applications. Electrostatic levitation is the process of using an electric field to levitate a charged object and counteract the effects of gravity. It was used, for instance, in Robert Millikan's oil drop experiment and is used to suspend the gyroscopes in Gravity Probe B during launch. Magnetic levitation, maglev, or magnetic suspension is a method by which an object is suspended with no support other than magnetic fields. Magnetic pressure is used to counteract the effects of the gravitational and any other accelerations. Optical levitation is a method developed by Arthur Ashkin whereby a material is levitated against the downward force of gravity by an upward force stemming from photonmomentum transfer. Typically photon radiation pressure of a vertical upwardly directed and focused laser beam of enough intensity counters the downward force of gravity to allow for a stable optical trap capable of holding small particles in suspension. Aerodynamic levitation is the use of gas pressure to levitate materials so that they are no longer in physical contact with any container. In scientific experiments this removes contamination and nucleation issues associated with physical contact with a container.
The Rise and Fall of the Third Reich (1960), by William L. Shirer, is a general history of Nazi Germany (1933–45), based upon captured Third Reich documents, the available diaries of propaganda minister Joseph Goebbels, General Franz Halder, and of the Italian Foreign Minister Galeazzo Ciano, evidence and testimony from the Nuremberg Trials, British Foreign Office reports, and the author’s recollections of six years’ of Third Reich reportage, for newspapers, the United Press International (UPI), and CBSradio, ended by Nazi censorship in 1940.[1] In 1961, The Rise and Fall of the Third Reich earned a National Book Award, and was adapted to television as a miniseries and broadcast by the American Broadcasting Company network in 1966.Whereas nearly all American journalists praised the book, academics were split. Some of these acknowledged Shirer's achievement, but most condemned it.[12] The harshest criticism tended to come from those who disagreed with the Sonderweg or "Luther to Hitler" thesis mentioned above. Klaus Epstein listed "four major failings": a crude understanding of German history; a lack of balance, leaving important gaps; no understanding of a modern totalitarian regime; and ignorance of current scholarship of the Nazi period.[9] Elizabeth Wiskemann stated in a 1961 review that the book was "not sufficiently scholarly nor sufficiently well written to satisfy more academic demands ... It is too long and cumbersome... Mr Shirer, has, however compiled a manual ... which will certainly prove useful."[16]
The National Security Agency can be traced to the May 20, 1949, originally the Armed Forces Security Agency (AFSA).[9] This organization was originally established within the U.S. Department of Defense under the command of the Joint Chiefs of Staff. The AFSA was to direct the communications and electronic intelligence activities of the U.S. military intelligence units: the Army Security Agency, the Naval Security Group, and the Air Force Security Service. However, that agency had little power and lacked a centralized coordination mechanism. The creation of NSA resulted from a December 10, 1951, memo sent by CIA Director Walter Bedell Smith to James S. Lay, Executive Secretary of the National Security Council.[10] The memo observed that "control over, and coordination of, the collection and processing of Communications Intelligence had proved ineffective" and recommended a survey of communications intelligence activities. The proposal was approved on December 13, 1951, and the study authorized on December 28, 1951. The report was completed by June 13, 1952. Generally known as the "Brownell Committee Report," after committee chairman Herbert Brownell, it surveyed the history of U.S. communications intelligence activities and suggested the need for a much greater degree of coordination and direction at the national level. As the change in the security agency's name indicated, the role of NSA was extended beyond the armed forces.
The creation of NSA was authorized in a letter written by President Harry S. Truman in June 1952. The agency was formally established through a revision of National Security Council Intelligence Directive (NSCID) 9 on October 24, 1952,[10] and officially came into existence on November 4, 1952. President Truman's letter was itself classified and remained unknown to the public for more than a generation.
The idea that something so intangible can lift objects can seem unbelievable, but it's a real phenomenon. Acoustic levitation takes advantage of the properties of sound to cause solids, liquids and heavy gases to float. The process can take place in normal or reduced gravity. In other words, sound can levitate objects on Earth or in gas-filled enclosures in space. Scientists have developed a sound generator so powerful its shock waves can stun, and even kill people. Another group of researchers have developed another unusual application for sound: a method of "acoustic levitation" that could help maintain colonies on Mars or the moon by using high-pitched sound waves to remove alien dust.
Wired explains,Blasting a high-pitched noise from a tweeter into a pipe that focuses the sound waves can create enough pressure to lift troublesome alien dust off surfaces, according to a study published January in the Journal of the Acoustical Society of America. Extra-terrestrial missions have been plagued by dust and debris, which cling to rovers and astronauts because lunar and Martian environments lack the Earth's water or atmosphere that can displace the particles.
According to Wired, Electrostatic charging from solar winds and UV radiation on the Moon makes this sharp dust cling to everything, including astronaut suits where it can work its way through the glove air locks. It also sticks to the solar panels that power rovers and other instruments.
See acoustic levitation for yourself in the video below! Using only sound waves, the scientists are able to lift mock "Martian and lunar dust" off of a solar panel. Cool!
WATCH: http://www.huffingtonpost.com/2010/01/20/acoustic-levitation-stere_n_429558.html
To understand how acoustic levitation works, you first need to know a little about gravity, air and sound. First, gravity is a force that causes objects to attract one another. The simplest way to understand gravity is through Isaac Newton's law of universal gravitation. This law states that every particle in the universe attracts every other particle. The more massive an object is, the more strongly it attracts other objects. The closer objects are, the more strongly they attract each other. An enormous object, like the Earth, easily attracts objects that are close to it, like apples hanging from trees. Scientists haven't decided exactly what causes this attraction, but they believe it exists everywhere in the universe.
Second, air is a fluid that behaves essentially the same way liquids do. Like liquids, air is made of microscopic particles that move in relation to one another. Air also moves like water does -- in fact, some aerodynamic tests take place underwater instead of in the air. The particles in gasses, like the ones that make up air, are simply farther apart and move faster than the particles in liquids.
Third, sound is a vibration that travels through a medium, like a gas, a liquid or a solid object. A sound's source is an object that moves or changes shape very rapidly. For example, if you strike a bell, the bell vibrates in the air. As one side of the bell moves out, it pushes the air molecules next to it, increasing the pressure in that region of the air. This area of higher pressure is a compression. As the side of the bell moves back in, it pulls the molecules apart, creating a lower-pressure region called a rarefaction. The bell then repeats the process, creating a repeating series of compressions and rarefactions. Each repetition is one wavelength of the sound wave.
The sound wave travels as the moving molecules push and pull the molecules around them. Each molecule moves the one next to it in turn. Without this movement of molecules, the sound could not travel, which is why there is no sound in a vacuum.Acoustic levitation uses sound traveling through a fluid -- usually a gas -- to balance the force of gravity. On Earth, this can cause objects and materials to hover unsupported in the air. In space, it can hold objects steady so they don't move or drift. The process relies on of the properties of sound waves, especially intense sound waves.
The Physics of Sound Levitation A basic acoustic levitator has two main parts -- a transducer, which is a vibrating surface that makes sound, and a reflector. Often, the transducer and reflector have concave surfaces to help focus the sound. A sound wave travels away from the transducer and bounces off the reflector. Three basic properties of this traveling, reflecting wave help it to suspend objects in midair. First, the wave, like all sound, is a longitudinal pressure wave. In a longitudinal wave, movement of the points in the wave is parallel to the direction the wave travels. It's the kind of motion you'd see if you pushed and pulled one end of a stretched Slinky. Most illustrations, though, depict sound as a transverse wave, which is what you would see if you rapidly moved one end of the Slinky up and down. This is simply because transverse waves are easier to visualize than longitudinal waves.
Second, the wave can bounce off of surfaces. It follows the law of reflection, which states that the angle of incidence -- the angle at which something strikes a surface -- equals the angle of reflection -- the angle at which it leaves the surface. In other words, a sound wave bounces off a surface at the same angle at which it hits the surface. A sound wave that hits a surface head-on at a 90 degree angle will reflect straight back off at the same angle. The easiest way to understand wave reflection is to imagine a Slinky that is attached to a surface at one end. If you picked up the free end of the Slinky and moved it rapidly up and then down, a wave would travel the length of the spring. Once it reached the fixed end of the spring, it would reflect off of the surface and travel back toward you. The same thing happens if you push and pull one end of the spring, creating a longitudinal wave.
Finally, when a sound wave reflects off of a surface, the interaction between its compressions and rarefactions causes interference. Compressions that meet other compressions amplify one another, and compressions that meet rarefactions balance one another out. Sometimes, the reflection and interference can combine to create a standing wave. Standing waves appear to shift back and forth or vibrate in segments rather than travel from place to place. This illusion of stillness is what gives standing waves their name. Standing sound waves have defined nodes, or areas of minimum pressure, and antinodes, or areas of maximum pressure. A standing wave's nodes are at the heart of acoustic levitation. Imagine a river with rocks and rapids. The water is calm in some parts of the river, and it is turbulent in others. Floating debris and foam collect in calm portions of the river. In order for a floating object to stay still in a fast-moving part of the river, it would need to be anchored or propelled against the flow of the water. This is essentially what an acoustic levitator does, using sound moving through a gas in place of water.
Acoustic levitation uses sound pressure to allow objects to float.
By placing a reflector the right distance away from a transducer, the acoustic levitator creates a standing wave. When the orientation of the wave is parallel to the pull of gravity, portions of the standing wave have a constant downward pressure and others have a constant upward pressure. The nodes have very little pressure.
In space, where there is little gravity, floating particles collect in the standing wave's nodes, which are calm and still. On Earth, objects collect just below the nodes, where the acoustic radiation pressure, or the amount of pressure that a sound wave can exert on a surface, balances the pull of gravity. Acoustic Videos Nonlinear Sound and Acoustic Levitation Ordinary standing waves can be relatively powerful. For example, a standing wave in an air duct can cause dust to collect in a pattern corresponding to the wave's nodes. A standing wave reverberating through a room can cause objects in its path to vibrate. Low-frequency standing waves can also cause people to feel nervous or disoriented -- in some cases, researchers find them in buildings people report to be haunted. But these feats are small potatoes compared to acoustic levitation. It takes far less effort to influence where dust settles or to shatter a glass than it takes to lift objects from the ground. Ordinary sound waves are limited by their linear nature. Increasing the amplitude of the wave causes the sound to be louder, but it doesn't affect the shape of the wave form or cause it to be much more physically powerful.
However, extremely intense sounds -- like sounds that are physically painful to human ears -- are usually nonlinear. They can cause disproportionately large responses in the substances they travel through. Some nonlinear affects include:
- Distorted wave forms
- Shock waves, like sonic booms
- Acoustic streaming, or the constant flow of the fluid the wave travels through
- Acoustic saturation, or the point at which the matter can no longer absorb any more energy from the sound wave
Other Uses for Nonlinear Sound
Several medical procedures rely on nonlinear acoustics. For example, ultrasound imaging uses nonlinear effects to allow doctors to examine babies in the womb or view internal organs. High-intensity ultrasound waves can also pulverize kidney stones, cauterize internal injuries and destroy tumors. Levitating objects with sound isn't quite as simple as aiming a high-powered transducer at a reflector. Scientists also must use sounds of the correct frequency to create the desired standing wave. Any frequency can produce nonlinear effects at the right volume, but most systems use ultrasonic waves, which are too high-pitched for people to hear. In addition to the frequency and volume of the wave, researchers also must pay attention to a number of other factors:
- The distance between the transducer and the reflector must be a multiple of half of the wavelength of the sound the transducer produces. This produces a wave with stable nodes and antinodes. Some waves can produce several usable nodes, but the ones nearest the transducer and reflector usually not suitable for levitating objects. This is because the waves create a pressure zone close to the reflective surfaces.
- In a microgravity environment, such as outer space, the stable areas within the nodes must be large enough to support the floating object. On Earth, the high-pressure areas just below the node must be large enough as well. For this reason, the object being levitated should measure between one third and half of the wavelength of the sound. Objects larger than two thirds of the sound's wavelength are too large to be levitated -- the field isn't big enough to support them. The higher the frequency of the sound, the smaller the diameter of the objects it's possible to levitate.
- Objects that are the right size to levitate must also be of the right mass. In other words, scientists must evaluate the density of the object and determine whether the sound wave can produce enough pressure to counteract the pull of gravity on it.
- Drops of liquid being levitated must have a suitable Bond number, which is a ratio that describes the liquid's surface tension, density and size in the context of gravity and the surrounding fluid. If the Bond number is too low, the drop will burst.
- The intensity of the sound must not overwhelm the surface tension of liquid droplets being levitated. If the sound field is too intense, the drop will flatten into a donut and then burst.
- Manufacturing very small electronic devices and microchips often involves robots or complex machinery. Acoustic levitators can perform the same task by manipulating sound. For example, levitated molten materials will gradually cool and harden, and in a properly tuned field of sound, the resulting solid object is a perfect sphere. Similarly, a correctly shaped field can force plastics to deposit and harden only on the correct areas of a microchip.
- Some materials are corrosive or otherwise react with ordinary containers used during chemical analysis. Researchers can suspend these materials in an acoustic field to study them without the risk of contamination from or destruction of containers.
- The study of foam physics has a big obstacle -- gravity. Gravity pulls the liquid downward from foam, drying and destroying it. Researchers can contain foam with in acoustic fields to study it in space, without the interference of gravity. This can lead to a better understanding of how foam performs tasks like cleaning ocean water.
Other Levitator Setups
Although a levitator with one transducer and one reflector can suspend objects, some setups can increase stability or allow movement. For example, some levitators have three pairs of transducers and reflectors, which are positioned along the X, Y and Z axes. Others have one large transmitter and one small, movable reflector; the suspended object moves when the reflector moves. Objects hover in a slightly different area within the sound field depending on the influence of gravity. It takes more than just ordinary sound waves to supply this amount of pressure.
Some methods can levitate objects without creating sound heard by the human ear such as the one demonstrated at Otsuka Lab,[2] acrylic glass tank to create a large acoustic field. Acoustic levitation is usually used for containerless processing electromagnetic levitation but has the advantage of being able to levitate nonconducting materials. There is no known theoretical limit to what acoustic levitation can lift given enough vibratory sound, but in practice current technology limits the amount that can be lifted by this force to at most a few kilograms.[3] Acoustic levitators are used mostly in industry and for researchers of anti-gravity effects such as NASA; however some are commercially available to the public.Some are silent while others produce some audible sound. There are many ways of creating this effect, from creating a wave underneath the object and reflecting it back to its source, to using an which has become more important of late due to the small size and resistance of microchips and other such things in industry. Containerless processing may also be used for applications requiring very-high-purity materials or chemical reactions too rigorous to happen in a container. This method is harder to control than other methods of containerless processing.
Different forms of levitation have different scientific applications. Electrostatic levitation is the process of using an electric field to levitate a charged object and counteract the effects of gravity. It was used, for instance, in Robert Millikan's oil drop experiment and is used to suspend the gyroscopes in Gravity Probe B during launch. Magnetic levitation, maglev, or magnetic suspension is a method by which an object is suspended with no support other than magnetic fields. Magnetic pressure is used to counteract the effects of the gravitational and any other accelerations. Optical levitation is a method developed by Arthur Ashkin whereby a material is levitated against the downward force of gravity by an upward force stemming from photonmomentum transfer. Typically photon radiation pressure of a vertical upwardly directed and focused laser beam of enough intensity counters the downward force of gravity to allow for a stable optical trap capable of holding small particles in suspension. Aerodynamic levitation is the use of gas pressure to levitate materials so that they are no longer in physical contact with any container. In scientific experiments this removes contamination and nucleation issues associated with physical contact with a container.
The Rise and Fall of the Third Reich (1960), by William L. Shirer, is a general history of Nazi Germany (1933–45), based upon captured Third Reich documents, the available diaries of propaganda minister Joseph Goebbels, General Franz Halder, and of the Italian Foreign Minister Galeazzo Ciano, evidence and testimony from the Nuremberg Trials, British Foreign Office reports, and the author’s recollections of six years’ of Third Reich reportage, for newspapers, the United Press International (UPI), and CBSradio, ended by Nazi censorship in 1940.[1] In 1961, The Rise and Fall of the Third Reich earned a National Book Award, and was adapted to television as a miniseries and broadcast by the American Broadcasting Company network in 1966.Whereas nearly all American journalists praised the book, academics were split. Some of these acknowledged Shirer's achievement, but most condemned it.[12] The harshest criticism tended to come from those who disagreed with the Sonderweg or "Luther to Hitler" thesis mentioned above. Klaus Epstein listed "four major failings": a crude understanding of German history; a lack of balance, leaving important gaps; no understanding of a modern totalitarian regime; and ignorance of current scholarship of the Nazi period.[9] Elizabeth Wiskemann stated in a 1961 review that the book was "not sufficiently scholarly nor sufficiently well written to satisfy more academic demands ... It is too long and cumbersome... Mr Shirer, has, however compiled a manual ... which will certainly prove useful."[16]
The National Security Agency can be traced to the May 20, 1949, originally the Armed Forces Security Agency (AFSA).[9] This organization was originally established within the U.S. Department of Defense under the command of the Joint Chiefs of Staff. The AFSA was to direct the communications and electronic intelligence activities of the U.S. military intelligence units: the Army Security Agency, the Naval Security Group, and the Air Force Security Service. However, that agency had little power and lacked a centralized coordination mechanism. The creation of NSA resulted from a December 10, 1951, memo sent by CIA Director Walter Bedell Smith to James S. Lay, Executive Secretary of the National Security Council.[10] The memo observed that "control over, and coordination of, the collection and processing of Communications Intelligence had proved ineffective" and recommended a survey of communications intelligence activities. The proposal was approved on December 13, 1951, and the study authorized on December 28, 1951. The report was completed by June 13, 1952. Generally known as the "Brownell Committee Report," after committee chairman Herbert Brownell, it surveyed the history of U.S. communications intelligence activities and suggested the need for a much greater degree of coordination and direction at the national level. As the change in the security agency's name indicated, the role of NSA was extended beyond the armed forces.
The creation of NSA was authorized in a letter written by President Harry S. Truman in June 1952. The agency was formally established through a revision of National Security Council Intelligence Directive (NSCID) 9 on October 24, 1952,[10] and officially came into existence on November 4, 1952. President Truman's letter was itself classified and remained unknown to the public for more than a generation.
HIGH WEIRDNESS:
Before Gallup and the Friedman's were Owen and Donnelly.
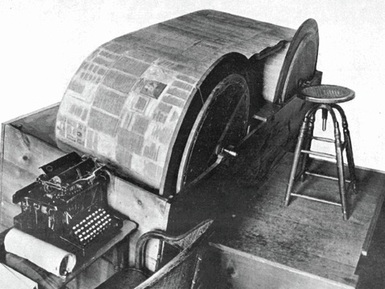
Orville Ward Owen's "cipher wheel", which he used to decipher the cryptograms in Shakespeare's works and "prove" that Bacon was the true author. Elizabeth Gallup was Owen's former assistant. Fabyan funded Owen's project, too.
1885 The English Bacon Society comes into being, to advance the idea that Bacon authored Shakespeare's plays.[112]
1888 Former Republican congressman Ignatius Donnelly publishes The Great Cryptogram in which he claims to have discovered "mystic ciphers" in Shakespeare's plays proving they had been written by Francis Bacon.
1892–93 A 15-month debate is conducted in the Boston monthly The Arena, with Donnelly as one of the plaintiffs, F.J.Furnivall on the defence, and a 25-member jury including Henry George, Edmund Gosse, and Henry Irving. The verdict heavily favours William Shakespeare of Stratford.[113]
The cipher wheel Owen used to decode Francis Bacon's hidden ciphers.[114]
1893 After reading Donnelly, Dr. Orville Ward Owen begins publishing the multi-volume Sir Francis Bacon's Cipher Story, in which he deciphers Bacon's biography from his writings and the works of Shakespeare, in the process discovering that Francis Bacon was the secret son of Queen Elizabeth. Owen constructed a "cipher wheel", a 1,000-foot long strip of canvas on which he had pasted the works of Shakespeare and other writers and mounted on two parallel wheels so he could quickly collate pages with key words as he turned them for decryption.[115]
1894 Elizabeth Wells Gallup met and began working with Owen of Detroit.
1895 Attorney Wilbur Gleason Zeigler publishes the novel Was Marlowe: A Story of the Secret of Three Centuries, in which he sets out in the preface for the first time the theory that Marlowe survived his 1593 death and wrote Shakespeare's plays.[116]
1903 The Invention of the Biliteral Cipher by Elizabeth Wells Gallup from BACONIANA 1903
The bi-lateral cypher of Sir Francis Bacon, Volume 3 - full text
http://books.google.com/books?id=Y6c3AAAAIAAJ&printsec=frontcover&dq=elizabeth+wells+gallup&source=bl&ots=i-4_17RK53&sig=1ZKypxJHOrjvWkcW301Ja7eVKX0&hl=en&ei=x43HTI2HG5GcsQPCmLnQDQ&sa=X&oi=book_result&ct=result&resnum=3&ved=0CBoQ6AEwAjgK#v=onepage&q&f=false
Not a little of the discussion concerning the existence of the Biliteral Cipher in the works of Francis Bacon has centered about the fact that Italian type in two forms in the same text existed in books printed before Bacon's time, that this use increased during the period in which he wrote, and was continued long after his death. This has led to many conjectures. By some it is thought to be an irrefutable argument against the use for cipher purposes in the books in which the cipher has been found; by others, that it is an evidence that its use was not confined to Bacon, but was much more widely extended, was familiar to many writers besides Bacon, and used long after his day entirely for cipher purposes.
I have in various ways sought to make plain what seems to me the real explanation, and may, in this connection, repeat what is already familiar to some readers. Many, however, do not understand it, and this is my excuse for further brief reference to the subject. It is conceded that Bacon was the inventor of the Biliteral system. Inventions usually result from the suggestion or adaptation of something already in existence. How mixed fonts came to be used before Bacon's time, is impossible to ascertain. The poverty or necessities of some printing office compelling "a make shift" to supply the lack of italic type may have been the beginning. To some other printer it appeared as "a new style," and was adopted as the latest fashion.
Bacon saw that by method in the arrangement of these two forms of letters already at hand, a cipher could be enclosed in the printed page, yet attract no attention--that it would be absolutely undiscoverable without the key--- and he incorporated a communication in his first book, The Shepherds' Calendar of 1579. The success and secrecy of his plan became at once apparent, and it was continued in his writings. Publishers of other books observed the permanence of "the new fashion" of two forms of type, and followed it for no particular reason, until a considerable part of the literature of the day appeared in this mixed form. The larger the number printed in this manner, with no method in the arrangement of letters, the greater the safety of the hidden matter in those of Bacon; and the disclosures show that he, becoming bolder, ventured to place the gravest secrets of his life in this two-formed type. The very success of its hiding caused him at length to fear that he had done his work too well, and that he must give some hint of its existence, or it would never be discovered. In 1605, we have the first mention of a Biliteral Cipher, but it was not until 1623 that the full explanation of it was given, after it had been in use forty-four years.
I have found the cipher in Bacon's works up to 1635. In one case-- that of the Sylva Sylvarum-- I found the cipher in the edition of 1635, but not in one of later date nor in one or earlier. The letters in two forms are there, but indiscriminately placed. I have examined the works of many authors--books printed in Bacon's lifetime and before, in which these differing forms of letters appear--but have failed to find in them the Biliteral method in groups of five. I do not say that no cipher exists in these books, but that the method delineated by Bacon in De Augmentis does not exist in those I have thus far examined.
I come to the conclusion, therefore, and this is confirmed in the cipher writings, that Bacon selected his types from those in general use, and that after his death the cipher was incorporated in the editions printed by Rawley, or some other confidant of Bacon, but not in all the editions that appeared. Time and strength were wanting to continue the examination of Rawley's later editions, but there is every reason to believe that, at least, some of these contain a continuation of the hidden writings.
1905 Fabyan Estate established, future home of Riverbank Labs.
1907 Orville Ward Owen decodes detailed instructions revealing the site where a box containing Bacon's literary treasures and proof of his authorship had been buried in the Wye river by Chepstow Castle on the Duke of Beaufort's property. His expensively rented dredging machinery fails to retrieve the concealed manuscripts.[118] Owen's former assistant, Elizabeth Wells Gallup, also sails to England after decoding a different message using a bilateral cipher, which reveals that Bacon's secret manuscripts were hidden behind some panels in Canonbury Tower, Islington.[119] They never found them, since the basis of the search was erroneous.
1912 Around 1912 she was hired by George Fabyan to work at his Riverbank Laboratories to decipher the manuscripts there, with the assistance of a staff and photographic equipment for enlarging letters of the First Folio. It had been known for some time that Francis Bacon belonged to a secret society called the Rosicrucian Society. They believed in conducting scientific experiments that in those times was often considered witchcraft. Due to Bacon’s position with the Queen of England, he ran the Queen’s printing press, and had devised what was called a biliteral cipher utilizing wide and thin letters to represent the alphabet. Colonel Fabyan also believed in the Baconian theory. Mrs. Gallup believed Bacon was the real Shakespeare for two reasons: 1) Bacon had invented the biliteral cipher and used it in printed publications, and 2) the original printed folios of Shakespeare’s plays used a variety of different typefaces. Colonel Fabyan was introduced to Mrs. Gallup by wealthy Bostonian friends and he persuaded her to move to his estate to continue her work. Her exact arrival date at Riverbank is not known, but it is thought to be around 1912 or 1913. Fabyan provided her and her sister living and working conditions, staff, and an excellent library of the works of Shakespeare. It is believed that she began her research at Riverbank in the Engledew Cottage, which has since been demolished. She and her sister later lived and worked in The Lodge.
Elizabeth Wells Gallup (1848, Paris, New York – 1934) was an American educator and exponent of the Baconian theory of Shakespearian authorship.Elizabeth Wells studied at Michigan State Normal College (now Eastern Michigan University), the Sorbonne and the University of Marburg. She taught in Michigan for some twenty years and became a high school principal. She was interested in the life and work of Francis Bacon and, together with her sister Kate Wells, initially worked on the theories of Dr Orville Ward Owen. She subsequently became convinced of the use of the bi-literal cipher in early Shapespeare printing to conceal messages concerning the authorship of the works and other statements about the secret history of the times. Her work was largely sponsored by Colonel George Fabyan at his Riverbank Laboratories in Geneva, Illinois. Fabyan, who had also funded Owen's work, supported a research staff working on her theory, which initially included the cryptographers William Friedman and Elizebeth Friedman. The Friedmans later published a careful study of her theory showing that the range of type forms used in the printing of the works of Shakespeare conformed to the normal printing practices of the time.
Dr Orville Ward Owen (January 1, 1854 – March 31, 1924) was an American physician and exponent of the Baconian theory of Shakespearean authorship. New Year See also New Year The Ancient Romans began their consular year on January 1st since 153 BC Year 1854 ( MDCCCLIV) was a Common year starting on Sunday (link will display the full calendar of the Gregorian Calendar (or a Common year Events 307 - After divorcing his wife Minervina, Constantine marries Fausta, the daughter of the retired Roman Emperor Year 1924 ( MCMXXIV) was a Leap year starting on Tuesday (link will display the full calendar of the Gregorian calendar. The Baconian theory of Shakespearean authorship holds that Sir Francis Bacon wrote the plays conventionally attributed to William Shakespeare
Owen's "cipher wheel" was a device for quickly collating printed pages from the works of Bacon and other authors, combining passages that appeared to have some connexion with key words or phrases. Owen described this as the word cipher. The method is discussed by the Friedmans who conclude that it has no cryptographic validity. Cryptography (or cryptology; from Greek grc κρυπτός kryptos, "hidden secret" and grc γράφω gráphō, "I write" Indeed Dr Frederick Mann, a close friend of Owen, published a severe critique soon after Owen's book first appeared.
Owen drew on the works normally attributed to Bacon, Shakespeare, Robert Greene, George Peele, Edmund Spenser and Robert Burton, some of which did not appear until over 20 years after Bacon's death. George Peele (born in London and baptized 25 July 1556 – buried 9 November 1596) was an English Dramatist Edmund Spenser (c 1552 – 13 January, 1599) was an important English Poet and Poet Laureate best known for The Robert Burton may refer to Robert Burton Sr (21st century printing industry executive Robert Burton (athlete (born 1885 British He believed that these revealed a secret history of the Elizabethan period, in which Bacon, the illegitimate son of Queen Elizabeth I and Robert Dudley, Earl of Leicester, had written the works attributed to the other authors. Robert Dudley 1st Earl of Leicester ( 24 June 1532 /1533 – 4 September 1588) was the long standing Favourite of Elizabeth
Owen was led to the belief that original manuscripts were hidden at Chepstow Castle, and made several expeditions to attempt to recover them in 1909-10. Chepstow Castle (Cas-gwent located in Chepstow, Monmouthshire in Wales on top of cliffs overlooking the River Wye, is the oldest surviving stone fortification Unfortunately nothing was found.
Owen's cipher wheel was discovered in a warehouse in Detroit [1] by Virginia Fellows (1910-2006), a supporter of Owen's theory, who presented it to her publisher.
The Shakespeare Code
by Virginia M. Fellows
Review by William C. House
Editor, Reverse Spins
July 7, 2006
Every so often a truly extraordinary book comes along. Many of the books these days are trying to ride the coat tails of The Da Vinci Code. Not this one. It was first published in August of 2000 with this title, long before The Da Vinci Code. The coincidence won't hurt however. Unlike The Da Vinci Code, The Shakespeare Code actually centers around real codes and ciphers created by one of the greatest minds of the 17th century or any other century for that matter. Many of you have already guessed of whom I am speaking especially if you have looked at the cover closely. But let me digress for a moment.
The author of the Shakespeare plays imbedded his true story out of necessity. Ciphers arose out of fear from retribution from either a tyrannical ruler or an overbearing dogmatic Church. This very same author spent a life time endeavoring to pull civilization, kicking and screaming, out from the dark ages. His goal was freedom in all its manisfestations—exploration, science, culture and religion. There was an inherent risk that was unavoidable—too much freedom. We are now over loaded with an excess of information and sensory input. To reach an audience with a message that is considered unimaginable by many, is difficult.
Virginia Fellows did a magnificent job writing this book. It took her thirty years of research. She started it very late in life. Perhaps because she was getting on in years (she passed away in the fall of 2005), she omitted one crucial element to the story: a good explanation of how the various ciphers work, but most especially, the cipher wheel. The fact that it was a self-published book with numerous errors and bland cover did not help. The very freedoms that her subject fought to bring about, threatened to bury her book in obscurity. The publishers of this new edition have rescued this work and have created a book worthy of any best seller list. They added a chapter at the end of the book dealing strictly with ciphers. An excellent cover as well as many illustrations were added. Additional corrobative sources were sought and all the grammatical errors corrected. Three hundred and eighty years after his death, the true story of Sir Francis Bacon is finally ready to be disseminated throughout the world.
Sir Francis Bacon; Baron Verulam and Viscount St Alban
The opening words by the Editors introduce you to this fascinating hidden story:
"In November 1623, the First Folio of the plays of William Shakespeare was published. The Folio is one of the most closely studied works of English literature, yet it raises many unanswered questions. In October 1623, a month earlier, Francis Bacon, one of the leading figures of the English Renaissance, published a book containing a complete description of a new and ingenious system of concealing messages in code. Is it just a coincidence that these two books were published one month apart?
In fact, the code that Bacon described unlocks many of the mysteries of the First Folio. The key to the Shakespeare code was embedded in a book that was widely circulated in his time and to the present. Yet it was more than 250 years before anyone realized that Bacon's writings on ciphers were not just theoretical, but they were describing his method for recording a secret history of his times.
Francis Bacon used this and other codes to conceal his work in books published under his own name and under the names of Shakespeare, Spenser, Marlowe and others of the time. The hidden messages tell a startling story. They reveal state secrets and scandals—the marriage of a "Virgin Queen," murder and intrigue, corruption and lies at the highest levels of the government. And they also tell the personal life story of Francis Bacon himself.
These stories could not be safely told in Bacon's own day—more than one person was severely punished for daring to speak these truths. So Bacon concealed them in code, hoping for a future time when they could be discovered and a day when men could be free to speak and to know the truth. The codes and the secrets they contain were discovered in the late 1800s. ... This book is an account not so much of the intricacies of ciphers and the detective work of those who discovered them, but of the hidden story itself. It does fill in details of history but, more importantly, it sets the record straight about Francis Bacon, one of the most remarkable men the world has seen. ..."
There have been others who have paved the way for this story, namely Ignatius Donnelly, Elizabeth Wells Gallup and Alfred Dodd; but it took a young physician from Detroit at the end of the 19th century, Dr. Orville Owen, to come up with the definitive device for cracking the code. Virginia Fellows was able to track down the original invention of Dr. Owen. The one who possessed this cipher wheel then gave it to her.
Dr. Owen built the cipher wheel exactly as Francis Bacon intended. Here are the instructions that were found in a Shakespearean cipher:
The easiest way to carry on the work is to
Take your knife and cut all books asunder;
And set the leaves on a great firm wheel
Which rolls and rolls.
Dr. Orville Owen's cipher wheel: This illustration, from Dr. Owen's original publication of the cipher story, shows the cipher wheel set up as he used it in his workshop. As he read passages from the wheel, his assistant would type them. The sheets would then be sorted according to the key-words typed at the top of each page. Illustration and description from p. 14 of The Shakespeare Code "Used by permission of Snow Mountain Press"
Francis Bacon used several types of ciphers, some even explained how to use other types of ciphers which told the broader history of his life. Dr. Owen discovered the most important of codes: "word ciphers." Through the use of the cipher wheel above, key words are found that include whole sentences on either side of the word. These various passages are then joined, unveiling the secrets of Bacon's life.
The publishers, Snow Mountain Press, recently unraveled the cipher wheel to get a closer look."Used by permission of Snow Mountain Press"
I did not see the two wheels and the operation of the cipher wheel but I have seen the scroll itself, coiled, standing vertical at eye level. I had the feeling of standing before some immense Tibetan prayer wheel filled with wonderful secrets—prayers from the heart of Bacon himself that he hoped would one day fly across The Globe. Looking at those old, brown pages on faded cloth, I was tempted to give the wound up scroll a spin to help them along. This review will be my spin instead. I could see for myself the marvelous scribblings of Dr. Owen as he underlined, highlighted and crossed out words and passages from the copies of original texts as Bacon had written them.
Closeup of Dr. Owen's marks on one row of pages. Four rows of pages stretch across a thousand feet of linen-like material. "Used by permission of Snow Mountain Press"
Dr. Owen trained assistants to operate the wheel and he invited others to test his discovery. In 1896, after being shown how the wheel worked, P.J. Sherman wrote about his findings. Here is an excerpt:
"The cipher reveals the fact that all the works of William Shakespeare, Robert Greene, George Peel, Christopher Marlowe's stage plays, the "Fairy Queen," "Shepherd's Calendar"; and all the works of Edmund Spenser; the "Anatomy of Melancholy" of Burton; Bacon's "History of Henry VII," the "Natural History," the "Interpretation of Nature," the "Great Instauration," the "Advancement of Learning," the "De Augmentis," "Essays," and all his other works were actually written by Sir Francis Bacon only, he using the other names as masks to conceal his own identity...."
The Shakespeare Code is not a dry, laborious explanation of ciphers but of the fascinating story of Bacon himself. You might think you have had a difficult life at times. Wait till you see what Bacon had to go through. His greatest degradations often times came from his own mother—the queen. It's a tale of trials, intrigue and testings that has largely been kept secret until now. Ultimately it is a story of supreme hope and inspiration. Despite all the attacks and opposition, no other living person has done more to elevate mankind since the time of Jesus Christ, than the soul of Francis Bacon. It's time for the rest of the story to be told.
William House
1885 The English Bacon Society comes into being, to advance the idea that Bacon authored Shakespeare's plays.[112]
1888 Former Republican congressman Ignatius Donnelly publishes The Great Cryptogram in which he claims to have discovered "mystic ciphers" in Shakespeare's plays proving they had been written by Francis Bacon.
1892–93 A 15-month debate is conducted in the Boston monthly The Arena, with Donnelly as one of the plaintiffs, F.J.Furnivall on the defence, and a 25-member jury including Henry George, Edmund Gosse, and Henry Irving. The verdict heavily favours William Shakespeare of Stratford.[113]
The cipher wheel Owen used to decode Francis Bacon's hidden ciphers.[114]
1893 After reading Donnelly, Dr. Orville Ward Owen begins publishing the multi-volume Sir Francis Bacon's Cipher Story, in which he deciphers Bacon's biography from his writings and the works of Shakespeare, in the process discovering that Francis Bacon was the secret son of Queen Elizabeth. Owen constructed a "cipher wheel", a 1,000-foot long strip of canvas on which he had pasted the works of Shakespeare and other writers and mounted on two parallel wheels so he could quickly collate pages with key words as he turned them for decryption.[115]
1894 Elizabeth Wells Gallup met and began working with Owen of Detroit.
1895 Attorney Wilbur Gleason Zeigler publishes the novel Was Marlowe: A Story of the Secret of Three Centuries, in which he sets out in the preface for the first time the theory that Marlowe survived his 1593 death and wrote Shakespeare's plays.[116]
1903 The Invention of the Biliteral Cipher by Elizabeth Wells Gallup from BACONIANA 1903
The bi-lateral cypher of Sir Francis Bacon, Volume 3 - full text
http://books.google.com/books?id=Y6c3AAAAIAAJ&printsec=frontcover&dq=elizabeth+wells+gallup&source=bl&ots=i-4_17RK53&sig=1ZKypxJHOrjvWkcW301Ja7eVKX0&hl=en&ei=x43HTI2HG5GcsQPCmLnQDQ&sa=X&oi=book_result&ct=result&resnum=3&ved=0CBoQ6AEwAjgK#v=onepage&q&f=false
Not a little of the discussion concerning the existence of the Biliteral Cipher in the works of Francis Bacon has centered about the fact that Italian type in two forms in the same text existed in books printed before Bacon's time, that this use increased during the period in which he wrote, and was continued long after his death. This has led to many conjectures. By some it is thought to be an irrefutable argument against the use for cipher purposes in the books in which the cipher has been found; by others, that it is an evidence that its use was not confined to Bacon, but was much more widely extended, was familiar to many writers besides Bacon, and used long after his day entirely for cipher purposes.
I have in various ways sought to make plain what seems to me the real explanation, and may, in this connection, repeat what is already familiar to some readers. Many, however, do not understand it, and this is my excuse for further brief reference to the subject. It is conceded that Bacon was the inventor of the Biliteral system. Inventions usually result from the suggestion or adaptation of something already in existence. How mixed fonts came to be used before Bacon's time, is impossible to ascertain. The poverty or necessities of some printing office compelling "a make shift" to supply the lack of italic type may have been the beginning. To some other printer it appeared as "a new style," and was adopted as the latest fashion.
Bacon saw that by method in the arrangement of these two forms of letters already at hand, a cipher could be enclosed in the printed page, yet attract no attention--that it would be absolutely undiscoverable without the key--- and he incorporated a communication in his first book, The Shepherds' Calendar of 1579. The success and secrecy of his plan became at once apparent, and it was continued in his writings. Publishers of other books observed the permanence of "the new fashion" of two forms of type, and followed it for no particular reason, until a considerable part of the literature of the day appeared in this mixed form. The larger the number printed in this manner, with no method in the arrangement of letters, the greater the safety of the hidden matter in those of Bacon; and the disclosures show that he, becoming bolder, ventured to place the gravest secrets of his life in this two-formed type. The very success of its hiding caused him at length to fear that he had done his work too well, and that he must give some hint of its existence, or it would never be discovered. In 1605, we have the first mention of a Biliteral Cipher, but it was not until 1623 that the full explanation of it was given, after it had been in use forty-four years.
I have found the cipher in Bacon's works up to 1635. In one case-- that of the Sylva Sylvarum-- I found the cipher in the edition of 1635, but not in one of later date nor in one or earlier. The letters in two forms are there, but indiscriminately placed. I have examined the works of many authors--books printed in Bacon's lifetime and before, in which these differing forms of letters appear--but have failed to find in them the Biliteral method in groups of five. I do not say that no cipher exists in these books, but that the method delineated by Bacon in De Augmentis does not exist in those I have thus far examined.
I come to the conclusion, therefore, and this is confirmed in the cipher writings, that Bacon selected his types from those in general use, and that after his death the cipher was incorporated in the editions printed by Rawley, or some other confidant of Bacon, but not in all the editions that appeared. Time and strength were wanting to continue the examination of Rawley's later editions, but there is every reason to believe that, at least, some of these contain a continuation of the hidden writings.
1905 Fabyan Estate established, future home of Riverbank Labs.
1907 Orville Ward Owen decodes detailed instructions revealing the site where a box containing Bacon's literary treasures and proof of his authorship had been buried in the Wye river by Chepstow Castle on the Duke of Beaufort's property. His expensively rented dredging machinery fails to retrieve the concealed manuscripts.[118] Owen's former assistant, Elizabeth Wells Gallup, also sails to England after decoding a different message using a bilateral cipher, which reveals that Bacon's secret manuscripts were hidden behind some panels in Canonbury Tower, Islington.[119] They never found them, since the basis of the search was erroneous.
1912 Around 1912 she was hired by George Fabyan to work at his Riverbank Laboratories to decipher the manuscripts there, with the assistance of a staff and photographic equipment for enlarging letters of the First Folio. It had been known for some time that Francis Bacon belonged to a secret society called the Rosicrucian Society. They believed in conducting scientific experiments that in those times was often considered witchcraft. Due to Bacon’s position with the Queen of England, he ran the Queen’s printing press, and had devised what was called a biliteral cipher utilizing wide and thin letters to represent the alphabet. Colonel Fabyan also believed in the Baconian theory. Mrs. Gallup believed Bacon was the real Shakespeare for two reasons: 1) Bacon had invented the biliteral cipher and used it in printed publications, and 2) the original printed folios of Shakespeare’s plays used a variety of different typefaces. Colonel Fabyan was introduced to Mrs. Gallup by wealthy Bostonian friends and he persuaded her to move to his estate to continue her work. Her exact arrival date at Riverbank is not known, but it is thought to be around 1912 or 1913. Fabyan provided her and her sister living and working conditions, staff, and an excellent library of the works of Shakespeare. It is believed that she began her research at Riverbank in the Engledew Cottage, which has since been demolished. She and her sister later lived and worked in The Lodge.
Elizabeth Wells Gallup (1848, Paris, New York – 1934) was an American educator and exponent of the Baconian theory of Shakespearian authorship.Elizabeth Wells studied at Michigan State Normal College (now Eastern Michigan University), the Sorbonne and the University of Marburg. She taught in Michigan for some twenty years and became a high school principal. She was interested in the life and work of Francis Bacon and, together with her sister Kate Wells, initially worked on the theories of Dr Orville Ward Owen. She subsequently became convinced of the use of the bi-literal cipher in early Shapespeare printing to conceal messages concerning the authorship of the works and other statements about the secret history of the times. Her work was largely sponsored by Colonel George Fabyan at his Riverbank Laboratories in Geneva, Illinois. Fabyan, who had also funded Owen's work, supported a research staff working on her theory, which initially included the cryptographers William Friedman and Elizebeth Friedman. The Friedmans later published a careful study of her theory showing that the range of type forms used in the printing of the works of Shakespeare conformed to the normal printing practices of the time.
Dr Orville Ward Owen (January 1, 1854 – March 31, 1924) was an American physician and exponent of the Baconian theory of Shakespearean authorship. New Year See also New Year The Ancient Romans began their consular year on January 1st since 153 BC Year 1854 ( MDCCCLIV) was a Common year starting on Sunday (link will display the full calendar of the Gregorian Calendar (or a Common year Events 307 - After divorcing his wife Minervina, Constantine marries Fausta, the daughter of the retired Roman Emperor Year 1924 ( MCMXXIV) was a Leap year starting on Tuesday (link will display the full calendar of the Gregorian calendar. The Baconian theory of Shakespearean authorship holds that Sir Francis Bacon wrote the plays conventionally attributed to William Shakespeare
Owen's "cipher wheel" was a device for quickly collating printed pages from the works of Bacon and other authors, combining passages that appeared to have some connexion with key words or phrases. Owen described this as the word cipher. The method is discussed by the Friedmans who conclude that it has no cryptographic validity. Cryptography (or cryptology; from Greek grc κρυπτός kryptos, "hidden secret" and grc γράφω gráphō, "I write" Indeed Dr Frederick Mann, a close friend of Owen, published a severe critique soon after Owen's book first appeared.
Owen drew on the works normally attributed to Bacon, Shakespeare, Robert Greene, George Peele, Edmund Spenser and Robert Burton, some of which did not appear until over 20 years after Bacon's death. George Peele (born in London and baptized 25 July 1556 – buried 9 November 1596) was an English Dramatist Edmund Spenser (c 1552 – 13 January, 1599) was an important English Poet and Poet Laureate best known for The Robert Burton may refer to Robert Burton Sr (21st century printing industry executive Robert Burton (athlete (born 1885 British He believed that these revealed a secret history of the Elizabethan period, in which Bacon, the illegitimate son of Queen Elizabeth I and Robert Dudley, Earl of Leicester, had written the works attributed to the other authors. Robert Dudley 1st Earl of Leicester ( 24 June 1532 /1533 – 4 September 1588) was the long standing Favourite of Elizabeth
Owen was led to the belief that original manuscripts were hidden at Chepstow Castle, and made several expeditions to attempt to recover them in 1909-10. Chepstow Castle (Cas-gwent located in Chepstow, Monmouthshire in Wales on top of cliffs overlooking the River Wye, is the oldest surviving stone fortification Unfortunately nothing was found.
Owen's cipher wheel was discovered in a warehouse in Detroit [1] by Virginia Fellows (1910-2006), a supporter of Owen's theory, who presented it to her publisher.
The Shakespeare Code
by Virginia M. Fellows
Review by William C. House
Editor, Reverse Spins
July 7, 2006
Every so often a truly extraordinary book comes along. Many of the books these days are trying to ride the coat tails of The Da Vinci Code. Not this one. It was first published in August of 2000 with this title, long before The Da Vinci Code. The coincidence won't hurt however. Unlike The Da Vinci Code, The Shakespeare Code actually centers around real codes and ciphers created by one of the greatest minds of the 17th century or any other century for that matter. Many of you have already guessed of whom I am speaking especially if you have looked at the cover closely. But let me digress for a moment.
The author of the Shakespeare plays imbedded his true story out of necessity. Ciphers arose out of fear from retribution from either a tyrannical ruler or an overbearing dogmatic Church. This very same author spent a life time endeavoring to pull civilization, kicking and screaming, out from the dark ages. His goal was freedom in all its manisfestations—exploration, science, culture and religion. There was an inherent risk that was unavoidable—too much freedom. We are now over loaded with an excess of information and sensory input. To reach an audience with a message that is considered unimaginable by many, is difficult.
Virginia Fellows did a magnificent job writing this book. It took her thirty years of research. She started it very late in life. Perhaps because she was getting on in years (she passed away in the fall of 2005), she omitted one crucial element to the story: a good explanation of how the various ciphers work, but most especially, the cipher wheel. The fact that it was a self-published book with numerous errors and bland cover did not help. The very freedoms that her subject fought to bring about, threatened to bury her book in obscurity. The publishers of this new edition have rescued this work and have created a book worthy of any best seller list. They added a chapter at the end of the book dealing strictly with ciphers. An excellent cover as well as many illustrations were added. Additional corrobative sources were sought and all the grammatical errors corrected. Three hundred and eighty years after his death, the true story of Sir Francis Bacon is finally ready to be disseminated throughout the world.
Sir Francis Bacon; Baron Verulam and Viscount St Alban
The opening words by the Editors introduce you to this fascinating hidden story:
"In November 1623, the First Folio of the plays of William Shakespeare was published. The Folio is one of the most closely studied works of English literature, yet it raises many unanswered questions. In October 1623, a month earlier, Francis Bacon, one of the leading figures of the English Renaissance, published a book containing a complete description of a new and ingenious system of concealing messages in code. Is it just a coincidence that these two books were published one month apart?
In fact, the code that Bacon described unlocks many of the mysteries of the First Folio. The key to the Shakespeare code was embedded in a book that was widely circulated in his time and to the present. Yet it was more than 250 years before anyone realized that Bacon's writings on ciphers were not just theoretical, but they were describing his method for recording a secret history of his times.
Francis Bacon used this and other codes to conceal his work in books published under his own name and under the names of Shakespeare, Spenser, Marlowe and others of the time. The hidden messages tell a startling story. They reveal state secrets and scandals—the marriage of a "Virgin Queen," murder and intrigue, corruption and lies at the highest levels of the government. And they also tell the personal life story of Francis Bacon himself.
These stories could not be safely told in Bacon's own day—more than one person was severely punished for daring to speak these truths. So Bacon concealed them in code, hoping for a future time when they could be discovered and a day when men could be free to speak and to know the truth. The codes and the secrets they contain were discovered in the late 1800s. ... This book is an account not so much of the intricacies of ciphers and the detective work of those who discovered them, but of the hidden story itself. It does fill in details of history but, more importantly, it sets the record straight about Francis Bacon, one of the most remarkable men the world has seen. ..."
There have been others who have paved the way for this story, namely Ignatius Donnelly, Elizabeth Wells Gallup and Alfred Dodd; but it took a young physician from Detroit at the end of the 19th century, Dr. Orville Owen, to come up with the definitive device for cracking the code. Virginia Fellows was able to track down the original invention of Dr. Owen. The one who possessed this cipher wheel then gave it to her.
Dr. Owen built the cipher wheel exactly as Francis Bacon intended. Here are the instructions that were found in a Shakespearean cipher:
The easiest way to carry on the work is to
Take your knife and cut all books asunder;
And set the leaves on a great firm wheel
Which rolls and rolls.
Dr. Orville Owen's cipher wheel: This illustration, from Dr. Owen's original publication of the cipher story, shows the cipher wheel set up as he used it in his workshop. As he read passages from the wheel, his assistant would type them. The sheets would then be sorted according to the key-words typed at the top of each page. Illustration and description from p. 14 of The Shakespeare Code "Used by permission of Snow Mountain Press"
Francis Bacon used several types of ciphers, some even explained how to use other types of ciphers which told the broader history of his life. Dr. Owen discovered the most important of codes: "word ciphers." Through the use of the cipher wheel above, key words are found that include whole sentences on either side of the word. These various passages are then joined, unveiling the secrets of Bacon's life.
The publishers, Snow Mountain Press, recently unraveled the cipher wheel to get a closer look."Used by permission of Snow Mountain Press"
I did not see the two wheels and the operation of the cipher wheel but I have seen the scroll itself, coiled, standing vertical at eye level. I had the feeling of standing before some immense Tibetan prayer wheel filled with wonderful secrets—prayers from the heart of Bacon himself that he hoped would one day fly across The Globe. Looking at those old, brown pages on faded cloth, I was tempted to give the wound up scroll a spin to help them along. This review will be my spin instead. I could see for myself the marvelous scribblings of Dr. Owen as he underlined, highlighted and crossed out words and passages from the copies of original texts as Bacon had written them.
Closeup of Dr. Owen's marks on one row of pages. Four rows of pages stretch across a thousand feet of linen-like material. "Used by permission of Snow Mountain Press"
Dr. Owen trained assistants to operate the wheel and he invited others to test his discovery. In 1896, after being shown how the wheel worked, P.J. Sherman wrote about his findings. Here is an excerpt:
"The cipher reveals the fact that all the works of William Shakespeare, Robert Greene, George Peel, Christopher Marlowe's stage plays, the "Fairy Queen," "Shepherd's Calendar"; and all the works of Edmund Spenser; the "Anatomy of Melancholy" of Burton; Bacon's "History of Henry VII," the "Natural History," the "Interpretation of Nature," the "Great Instauration," the "Advancement of Learning," the "De Augmentis," "Essays," and all his other works were actually written by Sir Francis Bacon only, he using the other names as masks to conceal his own identity...."
The Shakespeare Code is not a dry, laborious explanation of ciphers but of the fascinating story of Bacon himself. You might think you have had a difficult life at times. Wait till you see what Bacon had to go through. His greatest degradations often times came from his own mother—the queen. It's a tale of trials, intrigue and testings that has largely been kept secret until now. Ultimately it is a story of supreme hope and inspiration. Despite all the attacks and opposition, no other living person has done more to elevate mankind since the time of Jesus Christ, than the soul of Francis Bacon. It's time for the rest of the story to be told.
William House
Who Wrote Shakespeare's Plays? Pathology of Cryptology

Who Wrote Shakespeare's Plays? Steven Dutch, Natural and Applied Sciences,
In 1888, Ignatius Loyola Donnelley published The Great Cryptogram in which he proposed that Shakespeare's plays had been written by Francis Bacon, an idea that was popular during the late 19th and early 20th century. Elizabeth Gallup embraced his notion and convinced George Fabyan to underwrite extensive research and cryptological investigation.
For sheer longevity, no conspiracy theory can match the notion that William Shakespeare did not write tile plays that have been attributed to him. The plays contain too much accurate detail about distant places of affairs at court to have been written by someone of as low social standing as Shakespeare, goes one argument. The plays display too wide a range of style, goes another. Shakespeare was not educated enough and Stratford-on-Avon was too backward a place to have produced a playwright of such caliber, goes a third. And so, almost every prominent Elizabethan has been suggested at one time or another as the author of one or more of Shakespeare's plays: Ben Jonson, Christopher Marlowe, the Earl of Derby, the Earl of Rutland, the Earl of Southampton, the Earl of Essex, Sir Walter Raleigh and of course, Francis Bacon.
Bacon is a favorite candidate because he wrote some of the earliest modern works on codes and ciphers, and so generations of effort have been wasted trying to find hidden ciphers in the Bard's plays that would prove them to be Bacon's work. Why Bacon, or anyone else, would be content to ghost write plays and remain silent while they were receiving acclaim is a mystery the Baconians do not really address properly; it certainly does not fit the personalities of most Elizabethan court celebrities.
I've seen the argument that writing plays was considered a low-class occupation beneath the dignity of the aristocracy, or that the author needed to remain anonymous for fear of reprisals, but surely if Shakespeare's plays were on target enough to make such measures necessary, Elizabethan society would have been abuzz with speculation as to who the "real" author was. We need only recall the flap over the novel Primary Colors to see that.
It must be admitted that there are literary works with hidden codes and messages. An anonymous Latin work of 1616 uses the first letters of each of its 53 paragraphs to spell "Franciscus Godwinvvs Landavensis Episcopus hos conscripsit" --- "Francis Godwin, Bishop of Llandalf, wrote these lines". The spelling and grammar are flawless. A Spanish history of New Mexico published in 1812 was supposedly written by Don Pedro Baptista Pino, Count of Torene, but the real ghost-writer slipped his identity in anyway. The first letters of each sentence in three particular paragraphs spell out Juan Lopez Cancelada. In both these cases there is no doubt the hidden message is real; a simple rule brings out a straight-forward, error-free message. The same cannot be said for any of the alleged Shakespearean ciphers.
A central figure in the Shakespeare-Bacon theory is the redoubtable Ignatius Donnelly, who has been aptly dubbed "The Prince of U.S. Cranks". Donnelly found time to pursue a career in politics as well as develop not one but three major crank theories: Ragnarok, a catastrophe myth very similar in many ways to the ideas of Velikovsky, the Lost Continent of Atlantis, and the existence of a hidden message in Shakespeare's plays. The latter idea he developed in 1888 in a massive two-volume work, The Great Cryptogram. According to Donnely's own account, he had been working for a long time on proofs that Bacon was really the author of Shakespeare's plays. Quite by accident, he found a reference to Bacon's cipher in a book belonging to his young son, a book of children's amusements of the sort popular in the late 19th century. Here we see in sharp clarity the essential shallowness of the psaudoscientist. Donnelly had supposedly been studying the Bacon-Shakespeare question for a long time, yet he was entirely unaware of Bacon's well-known interest in ciphers until he stumbled accidentally across a reference to it in a child's puzzle book.
As William Friedman notes in The Shakesperean Ciphers Examined, Donnelly completely misunderstood Bacon's method. The cipher Donnelly was so entranced by actually depended on embedding a message in a longer dummy text using different type faces. Obviously such a cipher could only be decoded from the original printing of Shakespeare's/Bacon's plays. Donnelly eventually developed complex numerical schemes for working out the hidden messages, but Donnelly's methods left enormous latitude for varying the rules to make the message come out right. Friedman actually reproduced some of Donnelly's analysis of Act II, Scene I from Henry IV; it is a maze of complexity that would awe Rube Goldberg. Donnelly's rules were so flexible that one could literally use them to obtain any desired text. One of Donnelly' rules was that names could be spelled approximately or phonetically. Joseph Gilpin Pyle used Donnelly's methods to obtain this message from Hamlet: "Don nil hee (Donnelly) the author, politician and mountebanke, will work out the secret of this play. The Sage is a Daysie"! A British clergyman, A. Nicholson, found "Master Will I Am Shak'st spurre writ the play and was engaged at the curtain" using Donnelly's rules and the same text that Donnelly used to work out his system!
Incidentally, one can also "prove" that Shakespeare helped produce the King James Bible. When the King James Bible came out in 1611, Shakespeare was 46 years of age. The 46th word of Psalm 46 is "shake", and the 46th word from the end of Psalm 46 is "spear"! Actually, there is no real evidence that Shakespeare collaborated in translating the King James Bible. The 46th Psalm looks impressive, but is pure coincidence.
Never spoof pseudoscience. You'll be taken seriously every time. An American, Herbert Janvrin growne, published a pamphlet in 1887 that purportedly deciphered Shakespeare's epitaph, using rules that were a good deal simpler than Donnelly's, and found the message "Francis Bacon wrote Shakespeare's plays". Although Browne repeated on a number of occasions that the pamphlet was intended as satire, it was taken seriously by Baconians for some time. This makes a good deal of sense. A sense of humor is a sense of the ridiculous. A person who falls for ridiculous ideas is not likely to recognize satire. Small wonder most pseudoscientists and extremists in general (the political equivalents of pseudoscientists) are humorless except when it comes to ridiculing their opponents. One of Donnelly's more pointed critics wrote: "When men like Donnelly are born, they are given a kind of intellectual armor which will protect them from ridicule at the same time as it insulates them from reason. Perhaps it is just as well; to be at once ridiculous and sensitive to ridicule would be far more harrowing."
Another leading figure in the Bacon saga was Elizabeth Wells Gallup, one of the few Baconians to try actually using Bacon's ciphers to try to find hidden messages in Shakespeare's plays. Her work came to the attention of "Colonel" George Fabyan, a wealthy textile executive who never actually saw military service. Fabyan set up a research center for Mrs. Gallup at Riverbank Laboratories on his estate at t Geneva, Illinois. One of the researchers at Riverbank was William F. Friedman, who was hired in 1915 and who met his wife Elizabeth at Riverbank. The two left Riverbank in 1920 to work for the Government, and during World War II were leaders in U.S. code-breaking efforts. In a final irony, in 1957 the Friedmans turned their talents to the Bacon theory and wrote The Shakespearean Ciphers Examined, using professional cryptographic techniques to evaluate the many theories about hidden codes in Shakespeare. Though they expressed deep respect for Mrs. Gallup and gratitude for her and Fabyan's support in their early careers, their final conclusion was that neither Fabyan, nor Gallup, nor anyone else, had ever found a real code in Shakespeare. The author of Willaim Shakespeare's plays was William Shakespeare.
TIME MAGAZINE:
Besides the many scholars and crackpots who have used historical clues to show that someone else—usually Sir Francis Bacon—must have written Shakespeare's plays, scores have turned to cryptology to prove that the Bard's words were in a kind of cipher that concealed messages from their true author. Last week, in a new book called The Shakespearean Ciphers Examined (Cambridge University; $5), U.S. Cryptologists William and Elizebeth Friedman gave evidence that should discredit these investigators once and for all. The Friedmans' credentials are impressive: William led the team that broke the Japanese "purple" code a few months before Pearl Harbor (TIME, May 14, 1956).
Inner History. The first major cipher controversy began in the 1880s, when Minnesota Politician Ignatius Donnelly happened to pick up one of his children's copies of Routledge's Every Boy's Annual. There he found a description of an intricate cipher invented by Sir Francis Bacon. Already convinced that Bacon was Shakespeare, Donnelly set out to prove that Sir Francis used this cipher in writing the plays. Through an elaborate series of manipulations involving key page numbers, word counts and "root numbers," Donnelly finally "deciphered" such statements as "Seas ill (Cecil) said that More low (Marlowe) or Shak'st spurre (Shakespeare) never writ a word of them," convinced himself that Bacon had written the plays to conceal "the inner history of his times, in cipher." But no sooner had Donnelly published his theory than another scholar used his methods to produce the message: "Master Will I Am Shak'st spurre writ the play."
For some other Baconians, Shakespeare's epitaph was the source of all sorts of speculation. Using Bacon's cipher, one man translated the inscription to read SAEHR/BAYEEP/RFTAXA/RAWAR, crossed out the letters S-H-A-X-P-E-A-R-E, and by rearranging the remaining letters got FRA BAWRT EAR AY (i.e., "Francis Bacon wrote Shakespeare's plays"). Another investigator made each capital in the inscription stand for one, and, after counting the number of letters between them, produced: 1,3,1,7,4,4,8,1,3,6,3,1,4,1, 3,3,1,1,6,4,2,2,6,3,1,1,5,1,9,1,1,2,7,1,4, By making one stand for the most frequently used letter E, and two stand for A, etc.—and then by cheating just a bit—he got the words: Elesennrela Ledelleemn Aam-leetedeeasen. After some more hocuspocus, he changed this to read: Elesennre Laede Wedge Eere Aamleet Edeeasen—which he was sure meant "Elsinore laid wedge first Hamlet edition."
A Detroit physician named Orville Owen went so overboard on his own cipher theory that he declared Bacon was not only Shakespeare but also such authors as Marlowe, Edmund Spenser and Robert Burton. Another Baconian found his inspiration in the fact that both Bacon and Shakespeare used the word honorificabili-tudinitatibus. He divided the word into two parts, spelled the first backward (BACIFIRONOH), declared this to be an anagram for FR BACONO. From the rest of the letters, he got HI LUDI TUITI NATI SIBI, which taken all together spelled "These Plays, produced by Francis Bacon, guarded for themselves."
33 & 46. In 1938 Economist Wallace Cunningham, who entertained the notion that the plays had been written by a group of Rosicrucians and Freemasons, including Bacon, sent a book to Doubleday, Doran purporting to prove that the plays contained hidden stories (e.g., "The Asse Will Shakespeare . . . beares sland'rous tales to Hatton"). Doubleday sent the book to Cryptologist Friedman, who used Cunningham's own "Masonic Code" to get the message: "Dear Reader, Theodore Roosevelt is the true author of this play, but I, Bacon, stole it from him."
Meanwhile, the onetime president of England's Bacon Society, Frank Woodward, tried to prove his case through numerology. Assuming that A equals one and B equals two, etc., he added BACON up to 33, found it "very significant" that in one passage of Part I of Henry IV in the First Folio, the name Francis appears 33 times. Another numerologist noted that SHAKESPEAR has four vowels and six consonants. He then turned to the 46th Psalm, declared that the 46th word from the beginning was SHAKE and the 46th from the end was SPEAR. His conclusion, according to the Friedmans: "Since Shakespeare wrote the Psalms, and Shakespeare was not the real Shakespeare, the Authorized Version must show the hidden hand of Francis Bacon."
In dealing with these various theories, the Friedmans more than once use the methods set forth to prove that William Friedman himself wrote the plays (e.g., in attacking one favorite numerological theory, they show that WM. FRIEDMAN and FRANCIS BACON both equal 100). Through a meticulous study of Elizabethan printing methods, combined with a whole series of highly technical cryptological checks, they also demolish the theories of the late Elizabeth Gallup, who in the '20s and '30s attracted a large following among Baconians. So far as cryptology is concerned, conclude the Friedmans sternly, Shakespeare is still Shakespeare. "We suggest that those who wish to dispute the authorship of his plays should not in future resort to cryptographic evidence, unless they show themselves in some way competent to do so."
Read more: http://www.time.com/time/magazine/article/0,9171,862780,00.html#ixzz13W5nch4S
In 1888, Ignatius Loyola Donnelley published The Great Cryptogram in which he proposed that Shakespeare's plays had been written by Francis Bacon, an idea that was popular during the late 19th and early 20th century. Elizabeth Gallup embraced his notion and convinced George Fabyan to underwrite extensive research and cryptological investigation.
For sheer longevity, no conspiracy theory can match the notion that William Shakespeare did not write tile plays that have been attributed to him. The plays contain too much accurate detail about distant places of affairs at court to have been written by someone of as low social standing as Shakespeare, goes one argument. The plays display too wide a range of style, goes another. Shakespeare was not educated enough and Stratford-on-Avon was too backward a place to have produced a playwright of such caliber, goes a third. And so, almost every prominent Elizabethan has been suggested at one time or another as the author of one or more of Shakespeare's plays: Ben Jonson, Christopher Marlowe, the Earl of Derby, the Earl of Rutland, the Earl of Southampton, the Earl of Essex, Sir Walter Raleigh and of course, Francis Bacon.
Bacon is a favorite candidate because he wrote some of the earliest modern works on codes and ciphers, and so generations of effort have been wasted trying to find hidden ciphers in the Bard's plays that would prove them to be Bacon's work. Why Bacon, or anyone else, would be content to ghost write plays and remain silent while they were receiving acclaim is a mystery the Baconians do not really address properly; it certainly does not fit the personalities of most Elizabethan court celebrities.
I've seen the argument that writing plays was considered a low-class occupation beneath the dignity of the aristocracy, or that the author needed to remain anonymous for fear of reprisals, but surely if Shakespeare's plays were on target enough to make such measures necessary, Elizabethan society would have been abuzz with speculation as to who the "real" author was. We need only recall the flap over the novel Primary Colors to see that.
It must be admitted that there are literary works with hidden codes and messages. An anonymous Latin work of 1616 uses the first letters of each of its 53 paragraphs to spell "Franciscus Godwinvvs Landavensis Episcopus hos conscripsit" --- "Francis Godwin, Bishop of Llandalf, wrote these lines". The spelling and grammar are flawless. A Spanish history of New Mexico published in 1812 was supposedly written by Don Pedro Baptista Pino, Count of Torene, but the real ghost-writer slipped his identity in anyway. The first letters of each sentence in three particular paragraphs spell out Juan Lopez Cancelada. In both these cases there is no doubt the hidden message is real; a simple rule brings out a straight-forward, error-free message. The same cannot be said for any of the alleged Shakespearean ciphers.
A central figure in the Shakespeare-Bacon theory is the redoubtable Ignatius Donnelly, who has been aptly dubbed "The Prince of U.S. Cranks". Donnelly found time to pursue a career in politics as well as develop not one but three major crank theories: Ragnarok, a catastrophe myth very similar in many ways to the ideas of Velikovsky, the Lost Continent of Atlantis, and the existence of a hidden message in Shakespeare's plays. The latter idea he developed in 1888 in a massive two-volume work, The Great Cryptogram. According to Donnely's own account, he had been working for a long time on proofs that Bacon was really the author of Shakespeare's plays. Quite by accident, he found a reference to Bacon's cipher in a book belonging to his young son, a book of children's amusements of the sort popular in the late 19th century. Here we see in sharp clarity the essential shallowness of the psaudoscientist. Donnelly had supposedly been studying the Bacon-Shakespeare question for a long time, yet he was entirely unaware of Bacon's well-known interest in ciphers until he stumbled accidentally across a reference to it in a child's puzzle book.
As William Friedman notes in The Shakesperean Ciphers Examined, Donnelly completely misunderstood Bacon's method. The cipher Donnelly was so entranced by actually depended on embedding a message in a longer dummy text using different type faces. Obviously such a cipher could only be decoded from the original printing of Shakespeare's/Bacon's plays. Donnelly eventually developed complex numerical schemes for working out the hidden messages, but Donnelly's methods left enormous latitude for varying the rules to make the message come out right. Friedman actually reproduced some of Donnelly's analysis of Act II, Scene I from Henry IV; it is a maze of complexity that would awe Rube Goldberg. Donnelly's rules were so flexible that one could literally use them to obtain any desired text. One of Donnelly' rules was that names could be spelled approximately or phonetically. Joseph Gilpin Pyle used Donnelly's methods to obtain this message from Hamlet: "Don nil hee (Donnelly) the author, politician and mountebanke, will work out the secret of this play. The Sage is a Daysie"! A British clergyman, A. Nicholson, found "Master Will I Am Shak'st spurre writ the play and was engaged at the curtain" using Donnelly's rules and the same text that Donnelly used to work out his system!
Incidentally, one can also "prove" that Shakespeare helped produce the King James Bible. When the King James Bible came out in 1611, Shakespeare was 46 years of age. The 46th word of Psalm 46 is "shake", and the 46th word from the end of Psalm 46 is "spear"! Actually, there is no real evidence that Shakespeare collaborated in translating the King James Bible. The 46th Psalm looks impressive, but is pure coincidence.
Never spoof pseudoscience. You'll be taken seriously every time. An American, Herbert Janvrin growne, published a pamphlet in 1887 that purportedly deciphered Shakespeare's epitaph, using rules that were a good deal simpler than Donnelly's, and found the message "Francis Bacon wrote Shakespeare's plays". Although Browne repeated on a number of occasions that the pamphlet was intended as satire, it was taken seriously by Baconians for some time. This makes a good deal of sense. A sense of humor is a sense of the ridiculous. A person who falls for ridiculous ideas is not likely to recognize satire. Small wonder most pseudoscientists and extremists in general (the political equivalents of pseudoscientists) are humorless except when it comes to ridiculing their opponents. One of Donnelly's more pointed critics wrote: "When men like Donnelly are born, they are given a kind of intellectual armor which will protect them from ridicule at the same time as it insulates them from reason. Perhaps it is just as well; to be at once ridiculous and sensitive to ridicule would be far more harrowing."
Another leading figure in the Bacon saga was Elizabeth Wells Gallup, one of the few Baconians to try actually using Bacon's ciphers to try to find hidden messages in Shakespeare's plays. Her work came to the attention of "Colonel" George Fabyan, a wealthy textile executive who never actually saw military service. Fabyan set up a research center for Mrs. Gallup at Riverbank Laboratories on his estate at t Geneva, Illinois. One of the researchers at Riverbank was William F. Friedman, who was hired in 1915 and who met his wife Elizabeth at Riverbank. The two left Riverbank in 1920 to work for the Government, and during World War II were leaders in U.S. code-breaking efforts. In a final irony, in 1957 the Friedmans turned their talents to the Bacon theory and wrote The Shakespearean Ciphers Examined, using professional cryptographic techniques to evaluate the many theories about hidden codes in Shakespeare. Though they expressed deep respect for Mrs. Gallup and gratitude for her and Fabyan's support in their early careers, their final conclusion was that neither Fabyan, nor Gallup, nor anyone else, had ever found a real code in Shakespeare. The author of Willaim Shakespeare's plays was William Shakespeare.
TIME MAGAZINE:
Besides the many scholars and crackpots who have used historical clues to show that someone else—usually Sir Francis Bacon—must have written Shakespeare's plays, scores have turned to cryptology to prove that the Bard's words were in a kind of cipher that concealed messages from their true author. Last week, in a new book called The Shakespearean Ciphers Examined (Cambridge University; $5), U.S. Cryptologists William and Elizebeth Friedman gave evidence that should discredit these investigators once and for all. The Friedmans' credentials are impressive: William led the team that broke the Japanese "purple" code a few months before Pearl Harbor (TIME, May 14, 1956).
Inner History. The first major cipher controversy began in the 1880s, when Minnesota Politician Ignatius Donnelly happened to pick up one of his children's copies of Routledge's Every Boy's Annual. There he found a description of an intricate cipher invented by Sir Francis Bacon. Already convinced that Bacon was Shakespeare, Donnelly set out to prove that Sir Francis used this cipher in writing the plays. Through an elaborate series of manipulations involving key page numbers, word counts and "root numbers," Donnelly finally "deciphered" such statements as "Seas ill (Cecil) said that More low (Marlowe) or Shak'st spurre (Shakespeare) never writ a word of them," convinced himself that Bacon had written the plays to conceal "the inner history of his times, in cipher." But no sooner had Donnelly published his theory than another scholar used his methods to produce the message: "Master Will I Am Shak'st spurre writ the play."
For some other Baconians, Shakespeare's epitaph was the source of all sorts of speculation. Using Bacon's cipher, one man translated the inscription to read SAEHR/BAYEEP/RFTAXA/RAWAR, crossed out the letters S-H-A-X-P-E-A-R-E, and by rearranging the remaining letters got FRA BAWRT EAR AY (i.e., "Francis Bacon wrote Shakespeare's plays"). Another investigator made each capital in the inscription stand for one, and, after counting the number of letters between them, produced: 1,3,1,7,4,4,8,1,3,6,3,1,4,1, 3,3,1,1,6,4,2,2,6,3,1,1,5,1,9,1,1,2,7,1,4, By making one stand for the most frequently used letter E, and two stand for A, etc.—and then by cheating just a bit—he got the words: Elesennrela Ledelleemn Aam-leetedeeasen. After some more hocuspocus, he changed this to read: Elesennre Laede Wedge Eere Aamleet Edeeasen—which he was sure meant "Elsinore laid wedge first Hamlet edition."
A Detroit physician named Orville Owen went so overboard on his own cipher theory that he declared Bacon was not only Shakespeare but also such authors as Marlowe, Edmund Spenser and Robert Burton. Another Baconian found his inspiration in the fact that both Bacon and Shakespeare used the word honorificabili-tudinitatibus. He divided the word into two parts, spelled the first backward (BACIFIRONOH), declared this to be an anagram for FR BACONO. From the rest of the letters, he got HI LUDI TUITI NATI SIBI, which taken all together spelled "These Plays, produced by Francis Bacon, guarded for themselves."
33 & 46. In 1938 Economist Wallace Cunningham, who entertained the notion that the plays had been written by a group of Rosicrucians and Freemasons, including Bacon, sent a book to Doubleday, Doran purporting to prove that the plays contained hidden stories (e.g., "The Asse Will Shakespeare . . . beares sland'rous tales to Hatton"). Doubleday sent the book to Cryptologist Friedman, who used Cunningham's own "Masonic Code" to get the message: "Dear Reader, Theodore Roosevelt is the true author of this play, but I, Bacon, stole it from him."
Meanwhile, the onetime president of England's Bacon Society, Frank Woodward, tried to prove his case through numerology. Assuming that A equals one and B equals two, etc., he added BACON up to 33, found it "very significant" that in one passage of Part I of Henry IV in the First Folio, the name Francis appears 33 times. Another numerologist noted that SHAKESPEAR has four vowels and six consonants. He then turned to the 46th Psalm, declared that the 46th word from the beginning was SHAKE and the 46th from the end was SPEAR. His conclusion, according to the Friedmans: "Since Shakespeare wrote the Psalms, and Shakespeare was not the real Shakespeare, the Authorized Version must show the hidden hand of Francis Bacon."
In dealing with these various theories, the Friedmans more than once use the methods set forth to prove that William Friedman himself wrote the plays (e.g., in attacking one favorite numerological theory, they show that WM. FRIEDMAN and FRANCIS BACON both equal 100). Through a meticulous study of Elizabethan printing methods, combined with a whole series of highly technical cryptological checks, they also demolish the theories of the late Elizabeth Gallup, who in the '20s and '30s attracted a large following among Baconians. So far as cryptology is concerned, conclude the Friedmans sternly, Shakespeare is still Shakespeare. "We suggest that those who wish to dispute the authorship of his plays should not in future resort to cryptographic evidence, unless they show themselves in some way competent to do so."
Read more: http://www.time.com/time/magazine/article/0,9171,862780,00.html#ixzz13W5nch4S
The following article appeared in Baconiana Vol. LX. No.177, November 1977
by Neil Fermor
"In addition we understand from Group Captain F. Winterbotham, author of Ultra Secret, that Friedman admitted to him that he had been wrong to condemn all Baconian ciphers." In The Man Who Broke Purple (Weidenfeld and Nicolson; 1977), a biography of the American cryptologist [Colonel]William F. Friedman, Ronald W. Clark mentions a paper on"Shakespeare, Secret Intelligence and Statecraft" delivered by Friedman to the American Philosophical Society in 1962 (p.199). In this Friedman commented on "cryptologic" practices used by the "British Post Office" (sic) from about 1500 to 1844. He alluded in this context to Henry V (Act II, Scene II) where Bedford says of the traitors to his brother,
"The King hath note of all that they intend, By interception that they dream not of." Friedman's theory that the "interception" was of enciphered letters is intriguing in view of his expressed hostility to Baconian ciphers, with the grudging exception of Mrs. Gallup's Biliteral, in The Shakespearean Ciphers Examined, published in 1957, only five years before.
Although Shakespeare makes no other reference to the matter, the chroniclers Hall and Holinshed (used as a source by the playwright) related that Henry V was "credibly informed" of the treason. Friedman pointed out that no convincing explanation of the "commissions" handed by the King to the three traitors has been made to date, although each blanched on reading them. The suggestion is that the conspirators were given their own messages enciphered, and that a contemporary audience would have been aware of this.The scene seems irrelevant to the plot; but Mary, Queen of Scots, had been betrayed by the decipherment of her correspondence by Elizabeth's agents only thirteen years before......
If Friedman was right in this , as he believed, it is difficult to understand how he could have written The Shakespearean Ciphers Examined, which was in any case effectively answered by our President, Commander Pares, and Professor Henrion at the time.
However, it is worth recording that at a subsequent meeting in London, a trois , Pares had demonstrated the ciphers from the Colonel, and of Camden's Remaines without contradiction from the Colonel, and to the complete satisfaction of the Cambridge Professor of Mathematics, who was the third party ivolved. In addition we understand from Group Captain F. Winterbotham, author of Ultra Secret, that Friedman admitted to him that he had been wrong to condemn all Baconian ciphers.
In the interests of historical accuracy, and the slighting remarks on Baconians made in Ronald Clark's biography, and since Colonel Friedman is now dead, we feel amply justified in stating the true position as we see it. In doing so, however, we wish to point out that Friedman suffered increasingly from mental instability and paranoia in later years, as indeed is made clear in The Man Who Broke Purple.
One last point, unfortunately, has to be made clear. Readers of Baconiana may well remember the article Scientific Cryptography Examined by Pierre Henrion which appeared in no. 160, page 43 et sequitur. In this Herion was able to demonstrate the deliberate if subtle deceptions which appeared in the Friedmans' book. One professional cryptologist had rumbled another.
***** Kenneth R. Patton a student of the Shakespeare--Bacon system of ciphers for many years will be offering the readers of www.sirbacon.org an in depth study of his research from his forthcoming book "Setting the Record Straight", that will vindicate the intentional use of some Bacon ciphers in Shakespeare and he will illustrate the deliberate deceptions made by William Friedman in The Shakespearean Ciphers Examined. --Lawrence Gerald
by Neil Fermor
"In addition we understand from Group Captain F. Winterbotham, author of Ultra Secret, that Friedman admitted to him that he had been wrong to condemn all Baconian ciphers." In The Man Who Broke Purple (Weidenfeld and Nicolson; 1977), a biography of the American cryptologist [Colonel]William F. Friedman, Ronald W. Clark mentions a paper on"Shakespeare, Secret Intelligence and Statecraft" delivered by Friedman to the American Philosophical Society in 1962 (p.199). In this Friedman commented on "cryptologic" practices used by the "British Post Office" (sic) from about 1500 to 1844. He alluded in this context to Henry V (Act II, Scene II) where Bedford says of the traitors to his brother,
"The King hath note of all that they intend, By interception that they dream not of." Friedman's theory that the "interception" was of enciphered letters is intriguing in view of his expressed hostility to Baconian ciphers, with the grudging exception of Mrs. Gallup's Biliteral, in The Shakespearean Ciphers Examined, published in 1957, only five years before.
Although Shakespeare makes no other reference to the matter, the chroniclers Hall and Holinshed (used as a source by the playwright) related that Henry V was "credibly informed" of the treason. Friedman pointed out that no convincing explanation of the "commissions" handed by the King to the three traitors has been made to date, although each blanched on reading them. The suggestion is that the conspirators were given their own messages enciphered, and that a contemporary audience would have been aware of this.The scene seems irrelevant to the plot; but Mary, Queen of Scots, had been betrayed by the decipherment of her correspondence by Elizabeth's agents only thirteen years before......
If Friedman was right in this , as he believed, it is difficult to understand how he could have written The Shakespearean Ciphers Examined, which was in any case effectively answered by our President, Commander Pares, and Professor Henrion at the time.
However, it is worth recording that at a subsequent meeting in London, a trois , Pares had demonstrated the ciphers from the Colonel, and of Camden's Remaines without contradiction from the Colonel, and to the complete satisfaction of the Cambridge Professor of Mathematics, who was the third party ivolved. In addition we understand from Group Captain F. Winterbotham, author of Ultra Secret, that Friedman admitted to him that he had been wrong to condemn all Baconian ciphers.
In the interests of historical accuracy, and the slighting remarks on Baconians made in Ronald Clark's biography, and since Colonel Friedman is now dead, we feel amply justified in stating the true position as we see it. In doing so, however, we wish to point out that Friedman suffered increasingly from mental instability and paranoia in later years, as indeed is made clear in The Man Who Broke Purple.
One last point, unfortunately, has to be made clear. Readers of Baconiana may well remember the article Scientific Cryptography Examined by Pierre Henrion which appeared in no. 160, page 43 et sequitur. In this Herion was able to demonstrate the deliberate if subtle deceptions which appeared in the Friedmans' book. One professional cryptologist had rumbled another.
***** Kenneth R. Patton a student of the Shakespeare--Bacon system of ciphers for many years will be offering the readers of www.sirbacon.org an in depth study of his research from his forthcoming book "Setting the Record Straight", that will vindicate the intentional use of some Bacon ciphers in Shakespeare and he will illustrate the deliberate deceptions made by William Friedman in The Shakespearean Ciphers Examined. --Lawrence Gerald
Breaking codes was this couple's lifetime career

Breaking codes was this couple's lifetime career
By James R. Chiles, Smithsonian, June 1987 William and Elizebeth Friedman were roped into an odd profession by
a wealthy eccentric and became America's premier cryptologists
Toward the end of World War I, the British Army began manufacturing thousands of small cipher machines, "Pletts Cryptographs", for use by the Allied forces. The British asked the American forces to use them as well. No one in the French, British, or American military had been able to break the ciphers; the machine had a mechanism that regularly altered the ciphering scheme, so the first a might be turned into an f and the next a into an r.
Just to be sure that it was safe from enemy codebreakers, the American military passed it on to a remarkable husband-and-wife team in Illinois for testing. William and Elizebeth Friedman received a package with five telegram-length messages. It took them all of three hours to break the lot, after which they returned them to London, solved. The first of the five messages read: "This cipher is absolutely indecipherable."
Few ciphers were ever indecipherable to the Friedmans. By the end of his life, William Friedman was recognized as the greatest maker and breaker of secret messages in history--the Harry Houdini of codes and ciphers. Repeatedly, he accepted challenges to solve "unbreakable" ciphers, and succeeded. The papers he wrote brought cryptology, an ancient skill as obscure as witchcraft, into the scientific age. The team he trained and supervised broke into Japan's highest diplomatic cipher just before World War II; not only did the group penetrate the secret, it built a deciphering machine that worked as well as Japan's cipher machine. Elizebeth Friedman provided exceptional assistance to the U.S. Coast Guard and Navy, unraveling secret messages from rumrunners during Prohibition, narcotics traffickers during the 1930s and enemy agents during wartime. True to the shadowy world of intelligence work, the pair shunned publicity and avoided discussing their work -- even with each other.
Neither had planned a career of codebreaking. In keeping with the strangeness of their profession, it all began at a peculiar place called the Riverbank Laboratories. The Riverbank estate, located on the Fox River in a small suburb west of Chicago, was the magnificent hobby of Col. George Fabyan, an eccentric millionaire who had retired from cotton trading early in the century. Here, on 600 well-kept acres, Fabyan's stable of hired scientists pursued whatever he found interesting or worthwhile, from sound waves to cryptology to plant genetics. In the evenings, they enjoyed the genteel life of the "minor idle rich," in Elizebeth's words. Other employees tended his greenhouses, livestock- breeding operation, Dutch windmill, Japanese garden and caged vegetarian bears. A monkey and other pets had free access to Fabyan's house, which was also notable for its furniture hung from the ceiling by chains.
Fabyan, a large and loud man with iron-gray hair who wore frayed formal clothes in the city and a sort of horseman's outfit in the country, "had great natural gifts of energy and dynamism," the Friedmans wrote later. "He also had the trick of parroting other people's jargon; his conversation was usually impressive-superficially, anyway."
In the spring of 1915, Fabyan went hunting for a geneticist to improve crop strains. A professor at Cornell suggested William Friedman, a graduate student in genetics. Friedman, who had been born to a Russian Jewish family in 1891 and brought to America as an infant, was preparing for a future in biology. When Fabyan offered him the job, Friedman asked him what he raised on his estate. "I raise hell," Fabyan replied. Friedman signed on at a hundred dollars a month as head of Riverbank's Department of Genetics and began work the following September, taking up quarters in an upper floor of the windmill. In a short time Fabyan had him planting oats by the light of the moon, to see whether the phases made any difference.
The other half of the Friedman team, Elizebeth Smith, graduated from Hillsdale College in Michigan in 1915 with an English degree, and a year later sought work in Chicago. At the Newberry Library, a staff member mentioned to her that a George Fabyan was looking for someone to study Shakespeare and offered to call him at his Chicago office. Fabyan arrived in his chauffeured limousine and insisted that Elizebeth come to the estate immediately. "He was the kind of man who did not take 'no' for an answer," she would reminisce. That evening she met Elizabeth Wells Gallup, a woman who had convinced Fabyan that Francis Bacon was the real author of Shakespeare's plays and sonnets, and that Bacon had hidden a number of secret messages inside the original printed copies. Elizebeth agreed to assist Mrs. Gallup in this unusual project.
And so began the Friedmans' long involvement in the esoteric world of ciphers and codes. For most of the rest of us, here's the difference between the two: in a typical cipher (such as the Pletts Cryptograph solved by the Friedmans in 1918) each letter of the original message is changed into another letter or symbol according to some orderly scheme. To decipher the message, it helps to know that e is the most frequently used letter in English. With additional knowledge of the language and guesses based on the context of the emerging message, the rest of the alphabet follows.
Most ciphers, however, are vastly more complicated than a single substitution: e will be represented by different symbols at different points in the message. A basic way to accomplish this is to assign each letter of the alphabet a number: a is 1, b is 2, and so on. Then we add a key, a regularly repeating group of characters or words superimposed onto the message. Say we want to send the word "trouble," and our key is "fast." It works like this:
Message:
20(T) 18(R) 15(O) 21(U) 2(B) 12(L) 5(E)
Key:
6(F) 1(A) 19(S) 20(T) 6(F) I(A) 19(S)
Total them:
26 19 34 41 8 13 24
... and you have a cipher that your nosiest neighbor probably couldn't break. Your cousin on the other end will know the key, subtract it, and then distill the message. But it wouldn't even make lunchtime recreation for a cryptologist, who would aim a barrage of statistics at it and solve it in minutes.
A code is different. A typical code takes ideas in the message--words or even whole phrases--and changes them into something else, usually groups of numbers taken out of a codebook resembling a small dictionary. To compose a coded message, the sender first writes what he intends to say ("Attack is imminent") and then looks up the words in his codebook. "Attack" is 1140, and "imminent" is 4539. And that's his message: 1140 4539. To further confound the enemy, the sender might scramble the signal by using a key to encipher those numbers, by switching around the order, or both. The receiver must have an identical codebook and know anything extra the sender has done to scramble the number groups.
Codes and ciphers go back many centuries. Ancient Greek commanders scrambled messages by wrapping a strip of parchment or leather around a tapered staff in a tight spiral and writing their message down the length of the staff; unwound, the strip displayed a jumble of illegible letter fragments. A few centuries later, Julius Caesar wrote to associates in a simple cipher that took each letter of the message and substituted the letter three places farther down in the alphabet. Islamic people were the first to figure out how to attack ciphers in an organized way. During the Renaissance many European countries began setting up full-time codebreaking bureaus, called black chambers, to try to read each other's messages.
In 1625 Francis Bacon contributed a new kind of cipher to this busy scene, one that used only the letters a and b to represent the entire alphabet. In the table he set out, aaaaa stood for A, aaaab for B, aaaba for C, and so on. He called it the biliteral alphabet, and described how it could be disguised in an ordinary paragraph by using two different typefaces: one typeface representing a, and the other b.
Which brings us to Elizabeth Wells Gallup's Bacon-as-Shakespeare theory. It rested on two piers: Bacon had indeed invented the biliteral cipher, and the original printed folios of Shakespeare's plays employed an odd variety of typefaces.
Mrs. Gallup believed herself able to take printed lines from the plays and identify each character as either an a or a b typeface. Consulting the table that Bacon had published in 1625 she transformed each group of five a's and b's into a letter of the alphabet. The revelations she concocted were voluminous-one-fifth the length of the plays themselves--and sensational. Bacon, she claimed, not only wrote the plays but also was an illegitimate son of Queen Elizabeth I and the rightful heir to the throne. She convinced Fabyan to spend thousands of dollars digging holes around London, hunting for buried manuscripts. (Decades later, the Friedmans presented evidence that demolished the hidden-message theory. The peculiar typefaces were due to the economical habits of English printers, who preferred to repair old type rather than replace it.)
William Friedman spent time on the Bacon project as a photographer, taking close-up pictures of typefaces. Then, over the winter of 1916-17, with the approach of war, he turned over his genetics work to an assistant and joined Elizebeth in studying everything they could find on secret writings. Not much was available: the American literature, for example, consisted of a couple of short works by military men, and two articles and a story by Edgar Allan Poe. "We had a lot of pioneering to do." Elizebeth wrote later. "Literary ciphers may give you the swing of the thing, but they are in no sense scientific. There were no precedents for us to follow." In May 1917 the two married.
Meanwhile, Fabyan was bringing in coded diplomatic messages from unfriendly powers; he had offered his services free to the government, which had accepted. For almost a year, until the creation of the Army's Cipher Bureau, Riverbank was the only organization in the country capable of working out secret messages.
Among the most interesting problems to arrive at the large cottage where the Riverbank codebreakers worked were the cases involving the Hindu plotters. The first case was delivered personally by an official of Scotland Yard, who carried an attaché case packed with dozens of intercepted letters. For several years the Germans had been encouraging the aspirations of independence held by Indian citizens, on the theory that any trouble Indian radicals could stir up would siphon British strength from the war. Some of these radicals lived in the United States, and they had been passing cryptic messages around regarding arms shipments and internal politics.
One of the Hindu systems the couple broke into was a code that used numbers to indicate words and letters from a book that both sender and receiver had available. The cryptic number groups came in clusters of three, and the middle section always contained a 1 or a 2; that indicated a two-column page, probably a dictionary. The frequent use of some number groups indicated certain common words like "the" and "of." The first break was 99-2-14 in the code --page 99, the second column, the 14th word-- which they concluded from context was "you." That led to 99-2-17, which the couple guessed was near enough in the dictionary to be "your." Eventually they managed to make out nearly every word without having the actual dictionary at hand. Still, it was important to somehow obtain the dictionary for the upcoming trial of 155 Hindus in San Francisco. The Riverbank group polled large numbers of booksellers without results. Finally, having arrived in San Francisco to testify at the trial; William went into a university bookstore in Berkeley. He described what he was seeking (which must have been quite interesting in itself), and an employee dug around and produced the second volume of a German-English dictionary published in 1880. A quick check of the pages showed that this was, indeed, the book.
By late 1917 the Army had created its own Cipher Bureau, and the flow of intercepts to Riverbank ended. Fabyan determined to stay in the center of the action, arranged for the Friedmans to conduct classes in cryptography for Army officers.
Soon after the classes ended, William accepted a first lieutenant's commission in the Army and left for France. He spent the last five months of the war with General Pershing's staff, concentrating on breaking into the German codebooks. It was enough time to learn some important things about how armies employed codes and ciphers in wartime, and what could go wrong. For example, he observed that the German messages often began and ended with ritualized phrases, and that when a new code or cipher was introduced, the enemy's clerks were most likely to make a serious error (called a "bust" in the trade), exposing the system.
The following spring, William and Elizebeth returned to Riverbank. There William returned to the studies he had started before he left for Europe, which Fabyan issued as individual volumes in his Riverbank Publications series. In 1920 Friedman finished No. 22, titled The Index of Coincidence and its Applications in Cryptography. This booklet, says David Kahn, author of The Codebreakers, "must be regarded as the most important single publication in cryptology. It took the science into a new world." Friedman went beyond simple counts of letter frequency to discover techniques for applying statistical methods to cryptanalysis.
If you take any two lines of English text and place one above the other, so that each letter lines up with the one above or below it, there will occasionally be places where the same two letters appear in a vertical column. Friedman found that, for English, this coincidence consistently occurs in 6.67 columns out of every 100, or about seven percent of the time. He also found that this rate, the Index of Coincidence, is unique for each language. Such information can be very useful to a cryptanalyst with several enciphered messages from the same source. Usually these ciphers would be created using the same key, but the sender will have enciphered each message by starting at a different place in the key, according to some rule previously arranged between him and the receiver. Using the Index of Coincidence, the cryptanalyst can place the messages one above the other and, by sliding them back and forth, find the right "fit"-an indication that the key in the top message is vertically aligned with the same key in all the messages below it. Once the messages are aligned according to their key, he can work from message to message knowing that each letter in a vertical column has been enciphered with the same key letter as all the other letters in that column.
Shortly after this breakthrough the Army offered to employ the Friedmans as civilian "code experts" for a six-month trial period. With a few wary glances backward at Fabyan, wondering whether his tenacious grasp would reach to Washington, they left Riverbank for good and started military contract work in Washington, D.C., early in 1921.
In 1922, the War Department hired William permanently as chief codebreaker. Over the next few years he solved several "unbeatable" ciphers produced by machines. One of these, developed by Edward Hebern, foretold the hellishly complicated cipher machines that would dominate the next two decades. It used five movable rotors to scramble electrical signals between a keyboard and a set of glow lamps showing the enciphered letters. William had to determine the ciphering scheme, and then reconstruct much of the internal wiring. "He was discouraged to the point of blackout," Elizebeth said later. "Probably he sat for six weeks before he thought of a way to attack it.... It was all resolved in the end by the Index of Coincidence."
The Hebern solution was particularly important, says Louis Kruh, co-author of Machine Cryptography and Modern Cryptanalysis, because that machine "introduced a whole new concept of encipherment. It was the forerunner of any decent cipher machine between then and beyond World War II. Some of the report that he wrote on the solution is still classified today."
The latter part of that decade was exciting for Elizebeth. Her codebreaking began in earnest in 1927 as a "special agent" on loan from the Department of Justice to the Coast Guard, which was struggling to enforce the Volstead Act against a flood of smuggled shipborne liquor from the Bahamas, Canada and elsewhere.
The rumrunners' system required radio communications for rendezvous points, warnings and prices. It was this encoded and enciphered radio traffic that Elizebeth attacked. The early messages were elementary and quick to break. But as time went on and profits climbed, larger and more sophisticated syndicates took over the distribution network, and coding systems became more and more elaborate. In the first three years she and her assistants solved 12,000 messages using dozens of different schemes. In 1954 her decoding, and the detective work it inspired, cleared up a major diplomatic problem between the United States and Canada dating to 1929. She proved from old telegrams that the I'm Alone, a Canadian-flag schooner shelled and sunk by the Coast Guard in the Gulf of Mexico, had been secretly owned by an American smuggling ring.
Elizebeth, now working for the Treasury Department, was a star witness in a large and expensive trial in New Orleans of top officials of a Canadian outfit that controlled most of the liquor smuggling via the Gulf of Mexico and the Pacific. She deciphered and decoded cryptic radio messages that made prosecution possible.
The Friedman family, which by now included a son and a daughter, was aware that their mother's contact with organized crime had its dangers. Recalls daughter Barbara Atchison, "I remember Dad jesting once, when Mother was late getting home, that she might have been taken for a ride." And, in fact, while the I'm Alone case was under way, agents of the Treasury Department kept her under constant protection. Elizebeth broke open the code-ciphers used by narcotics smugglers. Her contributions to several sensational trials, and the associated convictions, earned her much unwanted attention from the press: "U.S. Woman Helps Smash Drug Ring," and "Key Woman of the T-Men," read two headlines.
War came and her work changed again. She devised a code system for William (Wild Bill) Donovan as he was organizing the Office of Strategic Services, and deciphered messages from German spies in Allied lands.
All this time William had been equally busy, but his work was well hidden from public view. In 1950 his responsibilities changed abruptly from the bookish work of composing codes. It was prompted by the closing of the Black Chamber, a cooperative codebreaking effort of the State Department and the Army that had evolved from the Army's old Cipher Bureau. The Black Chamber had decoded messages between Tokyo and the Japanese embassy, and in early 1929 Herbert Hoover's new Secretary of State, Henry Stimson, had removed his department's funding upon hearing about it. Years later, in his autobiography, he justified his action by saying that diplomats should not engage in such activities because "gentlemen do not read each other's mail." The Army quietly transferred the activities from the State Department to a new unit in the War Department, the Signal Intelligence Service (SIS). Friedman took charge as chief civilian cryptanalyst.
One of William's principal tasks was to train a new generation of experts to make and break codes, because all of the Black Chamber's personnel had dispersed. He started in the spring of 1930 with four spaces. He selected Frank Rowlett, a teacher from a small town in Virginia; Solomon Kullback and Abraham Sinkov, mathematicians from New York City; and John Hurt, the nephew of a congressman and an expert in Japanese.
The new team combed the files of the Black Chamber for useful information on Japanese cryptology. They read Friedman's booklets and worked through problems he concocted. He gave them assignments such as solving the Hebern cipher machine. "His teaching was such that we developed on our own," recalls Abraham Sinkov. "He just looked in from time to time to see how we were doing."
They operated on slim budgets--bringing their own pencils and writing on the back of old weather reports to save paper--but within two years they had progressed enough for Friedman to present them with the real thing: encrypted radio communications between Japanese diplomats.
By this time the Japanese knew that America had been reading secret diplomatic radio traffic. To protect its highest-level communications, Japan quickly switched to the new electromechanical cipher machine, "Angooki Taipu A." or "Red" to the Americans. It used a combination of wheels, rings and a rotor to scramble clear messages into a complex cipher. In 1935 the Army ordered Friedman's group to concentrate on breaking the system; by 1936 they were able to read the messages.
The passion for cryptology spilled over into the Friedmans' home life. William created a cipher game for children called "The Game of Secrecy" and tried it out on his son, John. He printed holiday greeting cards with cipher messages.
The most inventive of these pastimes were the progressive dinner parties hosted by the Friedmans. They divided their guests--a unique blend of codebreakers, newspapermen and scientists--into teams, and held the first course at one restaurant. "While they were eating, the restaurant owner gave them a piece of paper containing a clue about the next place to go," recalls John Friedman. "They'd go to five or six restaurants.... The first team to return home, won a prize."
William amused his children with enigmatic behavior. "He would come down to Sunday breakfast with six different ties on," remembers his daughter, Barbara. "He had a terrific sense of humor and whimsy, and women absolutely adored him."
Friedman had to leave most of his social life behind, however, when the Japanese decided to replace the Red machine with something much more secure. Labeled "Purple" by the SIS, the machine first contributed messages to Japan's radio circuits in February 1939. Unlike its predecessors, Purple used a type of switch identical to those used in automatic telephone exchanges to accomplish the main work of encipherment.
While dozens of others did the detailed statistical analysis necessary, William labored alone in his office on portions of the problem. He worked obsessively. The fear of failure--of what the Japanese were up to behind the screen of Purple--followed him home each night. "He'd be up until 2 or 3 in the morning," Elizebeth recalled later. "Sometimes I'd awaken and find him down in the kitchen making a Dagwood sandwich in the middle of the night." She remembered that her husband never discussed his difficulties with Purple, not even on the day in the fall of 1940 when the deciphering first succeeded. (For years, all he would tell his son, John, about his job was that he "worked for the Army.")
The team spent a total of 18 months puzzling out the mechanism and the nest of wiring from their calculations son how the original machine converted plaintext to cipher. Then, out of $684.65 worth of parts, they went ahead and built their own reconstruction of the Purple machine.
The Purple disclosures (codenamed "Magic") proved extremely valuable during the war. Ironically, says David Kahn, Magic "had its greatest effect on the war against Germany, not Japan, because we were getting a great deal of information that the Japanese ambassador in Berlin was sending ii back to Tokyo." For example, the ambassador, Baron Oshima, described Germany's new jet fighters in detail, and he listed German troop strength in the Balkans. Oshima even cabled a close description of the Normandy defenses in late 1943. Unfortunately, Magic did not clearly reveal the Japanese intention to attack Pearl Harbor --signals only indicated an impending crisis between America and Japan.
Codebreaking definitely changed the course of the war. The Allies made three major breakthroughs in all: the Japanese diplomatic cipher, Purple: the main German military cipher called "Enigma," which was broken by the Polish and British; and the Japanese fleet code, broken by the U.S. Navy, which made possible many American victories including the Battle of Midway. What made the breaking of Purple so extraordinary, says author Louis Kruh, is that the SIS had no pieces of the machine to study. When the team studied genuine Purple components after the war, he adds, they found that, out of all the thousands of soldered connections, "only two wiring connections turned out to have been interchanged."
Due largely to overwork on Purple, William suffered a mental breakdown at the turn of the year, and spent the next three months recovering in Walter Reed Hospital. Though the hospital recommended he return to duty, shortly afterward the Army discharged him from service. He served out the war as a civilian, organizing attacks on new cipher systems and rapidly training more cipher personnel.
"The war years were horrendous," recalls his daughter. "He was very, very involved in his work. I remember being worried to death about Dad." Attacks of depression severe enough to require psychiatric treatment or hospitalization would return again.
Wartime associates remember William as demanding and brilliant. "When working on a problem," recalls Frank Rowlett, "he was inclined to develop a plan of attack which he usually followed meticulously until the problem was either solved or it could be established that the attack would not be successful. His memory was excellent and he had a most unusual ability to grasp the complexity of a problem." Lambros Callimahos, a concert flutist who became a codebreaker in 1942, remembered Friedman as the "dapper figure with the Adolphe Menjou mustache, the characteristic bow tie, and the two-tone black-and-white shoes." Friedman was notoriously meticulous, even to the point of keeping carbon copies of handwritten notes. Judy Friedman, his daughter-in-law, remembers her he first weekend visit with the family. John had forewarned her that if his father failed to criticize her language, that meant she hadn't made the grade. Throughout the weekend, there was not a single comment from William about her speech. Judy was crushed. Then, upon leaving the house, he leaned close and whispered, "My dear, you made five grammatical errors this weekend," and proceeded to elaborate on them. Nothing could have pleased her more.
After the war, the Army restored William's rank and he served as a top ranking cryptanalyst in the various agencies leading up to the present National Security Agency (NSA). In 1956 Congress awarded him $100,000, partly in compensation for many of his inventions that were so sensitive and useful that the military had kept them off the market. One of these, a mechanism he had developed with Frank Rowlett, was the basis of the SIGABA machine, which the U.S. military used as its top-level enciphering device during World War II. The Axis never penetrated its messages.
William retired officially from the NSA in 1955 but continued to undertake various special and highly secret missions. His relations with the NSA were stormy at times; he believed the agency sometimes mistreated him and that it snooped excessively into citizens' communications. The NSA, in turn, occasionally saw him as a security risk: in 1958 three NSA employees appeared at his Capitol Hill house and carried off a stack of papers.
Elizebeth finished her professional career as a consultant for the International Monetary Fund, setting up a secure communications system there.
Toward the end of their careers (William died in 1969 and Elizebeth in 1980), the couple returned to the unlikely project that had first seduced them into the world of cryptography -the Shakespeare problem. Their incisive book, titled The Shakespearean Ciphers Examined, won them a Folger Shakespeare Library award in 1955. And in a classic demonstration of their life's work, Elizebeth and William Friedman included a hidden biliteral cipher on page 257 of the book. Buried in an italicized phrase, using two different typefaces, is their final verdict about the whole controversy: "I did not write the plays. E Bacon."
Additional Reading
The Codebreakers: The Story of Secret Writing
by David Kahn, Macmillan, 1967
The Shakespearean Ciphers Examined
by William F. and Elizebeth S. Friedman,
Cambridge University Press, 1957
The Man Who Broke Purple
by Ronald Clark, Little, Brown, 1977
Machine Cryptography and Modern Cryptanalysis
by Cipher A. Deavours and Louis Kruh,
Artech House (Dedham, Massachusetts), 1985
The Index of Coincidence and Its Applications in Cryptography
by William F. Friedman, (Riverbank publications, Vol. 9),
Aegean Part Press (Laguna Hills, California), 1979
By James R. Chiles, Smithsonian, June 1987 William and Elizebeth Friedman were roped into an odd profession by
a wealthy eccentric and became America's premier cryptologists
Toward the end of World War I, the British Army began manufacturing thousands of small cipher machines, "Pletts Cryptographs", for use by the Allied forces. The British asked the American forces to use them as well. No one in the French, British, or American military had been able to break the ciphers; the machine had a mechanism that regularly altered the ciphering scheme, so the first a might be turned into an f and the next a into an r.
Just to be sure that it was safe from enemy codebreakers, the American military passed it on to a remarkable husband-and-wife team in Illinois for testing. William and Elizebeth Friedman received a package with five telegram-length messages. It took them all of three hours to break the lot, after which they returned them to London, solved. The first of the five messages read: "This cipher is absolutely indecipherable."
Few ciphers were ever indecipherable to the Friedmans. By the end of his life, William Friedman was recognized as the greatest maker and breaker of secret messages in history--the Harry Houdini of codes and ciphers. Repeatedly, he accepted challenges to solve "unbreakable" ciphers, and succeeded. The papers he wrote brought cryptology, an ancient skill as obscure as witchcraft, into the scientific age. The team he trained and supervised broke into Japan's highest diplomatic cipher just before World War II; not only did the group penetrate the secret, it built a deciphering machine that worked as well as Japan's cipher machine. Elizebeth Friedman provided exceptional assistance to the U.S. Coast Guard and Navy, unraveling secret messages from rumrunners during Prohibition, narcotics traffickers during the 1930s and enemy agents during wartime. True to the shadowy world of intelligence work, the pair shunned publicity and avoided discussing their work -- even with each other.
Neither had planned a career of codebreaking. In keeping with the strangeness of their profession, it all began at a peculiar place called the Riverbank Laboratories. The Riverbank estate, located on the Fox River in a small suburb west of Chicago, was the magnificent hobby of Col. George Fabyan, an eccentric millionaire who had retired from cotton trading early in the century. Here, on 600 well-kept acres, Fabyan's stable of hired scientists pursued whatever he found interesting or worthwhile, from sound waves to cryptology to plant genetics. In the evenings, they enjoyed the genteel life of the "minor idle rich," in Elizebeth's words. Other employees tended his greenhouses, livestock- breeding operation, Dutch windmill, Japanese garden and caged vegetarian bears. A monkey and other pets had free access to Fabyan's house, which was also notable for its furniture hung from the ceiling by chains.
Fabyan, a large and loud man with iron-gray hair who wore frayed formal clothes in the city and a sort of horseman's outfit in the country, "had great natural gifts of energy and dynamism," the Friedmans wrote later. "He also had the trick of parroting other people's jargon; his conversation was usually impressive-superficially, anyway."
In the spring of 1915, Fabyan went hunting for a geneticist to improve crop strains. A professor at Cornell suggested William Friedman, a graduate student in genetics. Friedman, who had been born to a Russian Jewish family in 1891 and brought to America as an infant, was preparing for a future in biology. When Fabyan offered him the job, Friedman asked him what he raised on his estate. "I raise hell," Fabyan replied. Friedman signed on at a hundred dollars a month as head of Riverbank's Department of Genetics and began work the following September, taking up quarters in an upper floor of the windmill. In a short time Fabyan had him planting oats by the light of the moon, to see whether the phases made any difference.
The other half of the Friedman team, Elizebeth Smith, graduated from Hillsdale College in Michigan in 1915 with an English degree, and a year later sought work in Chicago. At the Newberry Library, a staff member mentioned to her that a George Fabyan was looking for someone to study Shakespeare and offered to call him at his Chicago office. Fabyan arrived in his chauffeured limousine and insisted that Elizebeth come to the estate immediately. "He was the kind of man who did not take 'no' for an answer," she would reminisce. That evening she met Elizabeth Wells Gallup, a woman who had convinced Fabyan that Francis Bacon was the real author of Shakespeare's plays and sonnets, and that Bacon had hidden a number of secret messages inside the original printed copies. Elizebeth agreed to assist Mrs. Gallup in this unusual project.
And so began the Friedmans' long involvement in the esoteric world of ciphers and codes. For most of the rest of us, here's the difference between the two: in a typical cipher (such as the Pletts Cryptograph solved by the Friedmans in 1918) each letter of the original message is changed into another letter or symbol according to some orderly scheme. To decipher the message, it helps to know that e is the most frequently used letter in English. With additional knowledge of the language and guesses based on the context of the emerging message, the rest of the alphabet follows.
Most ciphers, however, are vastly more complicated than a single substitution: e will be represented by different symbols at different points in the message. A basic way to accomplish this is to assign each letter of the alphabet a number: a is 1, b is 2, and so on. Then we add a key, a regularly repeating group of characters or words superimposed onto the message. Say we want to send the word "trouble," and our key is "fast." It works like this:
Message:
20(T) 18(R) 15(O) 21(U) 2(B) 12(L) 5(E)
Key:
6(F) 1(A) 19(S) 20(T) 6(F) I(A) 19(S)
Total them:
26 19 34 41 8 13 24
... and you have a cipher that your nosiest neighbor probably couldn't break. Your cousin on the other end will know the key, subtract it, and then distill the message. But it wouldn't even make lunchtime recreation for a cryptologist, who would aim a barrage of statistics at it and solve it in minutes.
A code is different. A typical code takes ideas in the message--words or even whole phrases--and changes them into something else, usually groups of numbers taken out of a codebook resembling a small dictionary. To compose a coded message, the sender first writes what he intends to say ("Attack is imminent") and then looks up the words in his codebook. "Attack" is 1140, and "imminent" is 4539. And that's his message: 1140 4539. To further confound the enemy, the sender might scramble the signal by using a key to encipher those numbers, by switching around the order, or both. The receiver must have an identical codebook and know anything extra the sender has done to scramble the number groups.
Codes and ciphers go back many centuries. Ancient Greek commanders scrambled messages by wrapping a strip of parchment or leather around a tapered staff in a tight spiral and writing their message down the length of the staff; unwound, the strip displayed a jumble of illegible letter fragments. A few centuries later, Julius Caesar wrote to associates in a simple cipher that took each letter of the message and substituted the letter three places farther down in the alphabet. Islamic people were the first to figure out how to attack ciphers in an organized way. During the Renaissance many European countries began setting up full-time codebreaking bureaus, called black chambers, to try to read each other's messages.
In 1625 Francis Bacon contributed a new kind of cipher to this busy scene, one that used only the letters a and b to represent the entire alphabet. In the table he set out, aaaaa stood for A, aaaab for B, aaaba for C, and so on. He called it the biliteral alphabet, and described how it could be disguised in an ordinary paragraph by using two different typefaces: one typeface representing a, and the other b.
Which brings us to Elizabeth Wells Gallup's Bacon-as-Shakespeare theory. It rested on two piers: Bacon had indeed invented the biliteral cipher, and the original printed folios of Shakespeare's plays employed an odd variety of typefaces.
Mrs. Gallup believed herself able to take printed lines from the plays and identify each character as either an a or a b typeface. Consulting the table that Bacon had published in 1625 she transformed each group of five a's and b's into a letter of the alphabet. The revelations she concocted were voluminous-one-fifth the length of the plays themselves--and sensational. Bacon, she claimed, not only wrote the plays but also was an illegitimate son of Queen Elizabeth I and the rightful heir to the throne. She convinced Fabyan to spend thousands of dollars digging holes around London, hunting for buried manuscripts. (Decades later, the Friedmans presented evidence that demolished the hidden-message theory. The peculiar typefaces were due to the economical habits of English printers, who preferred to repair old type rather than replace it.)
William Friedman spent time on the Bacon project as a photographer, taking close-up pictures of typefaces. Then, over the winter of 1916-17, with the approach of war, he turned over his genetics work to an assistant and joined Elizebeth in studying everything they could find on secret writings. Not much was available: the American literature, for example, consisted of a couple of short works by military men, and two articles and a story by Edgar Allan Poe. "We had a lot of pioneering to do." Elizebeth wrote later. "Literary ciphers may give you the swing of the thing, but they are in no sense scientific. There were no precedents for us to follow." In May 1917 the two married.
Meanwhile, Fabyan was bringing in coded diplomatic messages from unfriendly powers; he had offered his services free to the government, which had accepted. For almost a year, until the creation of the Army's Cipher Bureau, Riverbank was the only organization in the country capable of working out secret messages.
Among the most interesting problems to arrive at the large cottage where the Riverbank codebreakers worked were the cases involving the Hindu plotters. The first case was delivered personally by an official of Scotland Yard, who carried an attaché case packed with dozens of intercepted letters. For several years the Germans had been encouraging the aspirations of independence held by Indian citizens, on the theory that any trouble Indian radicals could stir up would siphon British strength from the war. Some of these radicals lived in the United States, and they had been passing cryptic messages around regarding arms shipments and internal politics.
One of the Hindu systems the couple broke into was a code that used numbers to indicate words and letters from a book that both sender and receiver had available. The cryptic number groups came in clusters of three, and the middle section always contained a 1 or a 2; that indicated a two-column page, probably a dictionary. The frequent use of some number groups indicated certain common words like "the" and "of." The first break was 99-2-14 in the code --page 99, the second column, the 14th word-- which they concluded from context was "you." That led to 99-2-17, which the couple guessed was near enough in the dictionary to be "your." Eventually they managed to make out nearly every word without having the actual dictionary at hand. Still, it was important to somehow obtain the dictionary for the upcoming trial of 155 Hindus in San Francisco. The Riverbank group polled large numbers of booksellers without results. Finally, having arrived in San Francisco to testify at the trial; William went into a university bookstore in Berkeley. He described what he was seeking (which must have been quite interesting in itself), and an employee dug around and produced the second volume of a German-English dictionary published in 1880. A quick check of the pages showed that this was, indeed, the book.
By late 1917 the Army had created its own Cipher Bureau, and the flow of intercepts to Riverbank ended. Fabyan determined to stay in the center of the action, arranged for the Friedmans to conduct classes in cryptography for Army officers.
Soon after the classes ended, William accepted a first lieutenant's commission in the Army and left for France. He spent the last five months of the war with General Pershing's staff, concentrating on breaking into the German codebooks. It was enough time to learn some important things about how armies employed codes and ciphers in wartime, and what could go wrong. For example, he observed that the German messages often began and ended with ritualized phrases, and that when a new code or cipher was introduced, the enemy's clerks were most likely to make a serious error (called a "bust" in the trade), exposing the system.
The following spring, William and Elizebeth returned to Riverbank. There William returned to the studies he had started before he left for Europe, which Fabyan issued as individual volumes in his Riverbank Publications series. In 1920 Friedman finished No. 22, titled The Index of Coincidence and its Applications in Cryptography. This booklet, says David Kahn, author of The Codebreakers, "must be regarded as the most important single publication in cryptology. It took the science into a new world." Friedman went beyond simple counts of letter frequency to discover techniques for applying statistical methods to cryptanalysis.
If you take any two lines of English text and place one above the other, so that each letter lines up with the one above or below it, there will occasionally be places where the same two letters appear in a vertical column. Friedman found that, for English, this coincidence consistently occurs in 6.67 columns out of every 100, or about seven percent of the time. He also found that this rate, the Index of Coincidence, is unique for each language. Such information can be very useful to a cryptanalyst with several enciphered messages from the same source. Usually these ciphers would be created using the same key, but the sender will have enciphered each message by starting at a different place in the key, according to some rule previously arranged between him and the receiver. Using the Index of Coincidence, the cryptanalyst can place the messages one above the other and, by sliding them back and forth, find the right "fit"-an indication that the key in the top message is vertically aligned with the same key in all the messages below it. Once the messages are aligned according to their key, he can work from message to message knowing that each letter in a vertical column has been enciphered with the same key letter as all the other letters in that column.
Shortly after this breakthrough the Army offered to employ the Friedmans as civilian "code experts" for a six-month trial period. With a few wary glances backward at Fabyan, wondering whether his tenacious grasp would reach to Washington, they left Riverbank for good and started military contract work in Washington, D.C., early in 1921.
In 1922, the War Department hired William permanently as chief codebreaker. Over the next few years he solved several "unbeatable" ciphers produced by machines. One of these, developed by Edward Hebern, foretold the hellishly complicated cipher machines that would dominate the next two decades. It used five movable rotors to scramble electrical signals between a keyboard and a set of glow lamps showing the enciphered letters. William had to determine the ciphering scheme, and then reconstruct much of the internal wiring. "He was discouraged to the point of blackout," Elizebeth said later. "Probably he sat for six weeks before he thought of a way to attack it.... It was all resolved in the end by the Index of Coincidence."
The Hebern solution was particularly important, says Louis Kruh, co-author of Machine Cryptography and Modern Cryptanalysis, because that machine "introduced a whole new concept of encipherment. It was the forerunner of any decent cipher machine between then and beyond World War II. Some of the report that he wrote on the solution is still classified today."
The latter part of that decade was exciting for Elizebeth. Her codebreaking began in earnest in 1927 as a "special agent" on loan from the Department of Justice to the Coast Guard, which was struggling to enforce the Volstead Act against a flood of smuggled shipborne liquor from the Bahamas, Canada and elsewhere.
The rumrunners' system required radio communications for rendezvous points, warnings and prices. It was this encoded and enciphered radio traffic that Elizebeth attacked. The early messages were elementary and quick to break. But as time went on and profits climbed, larger and more sophisticated syndicates took over the distribution network, and coding systems became more and more elaborate. In the first three years she and her assistants solved 12,000 messages using dozens of different schemes. In 1954 her decoding, and the detective work it inspired, cleared up a major diplomatic problem between the United States and Canada dating to 1929. She proved from old telegrams that the I'm Alone, a Canadian-flag schooner shelled and sunk by the Coast Guard in the Gulf of Mexico, had been secretly owned by an American smuggling ring.
Elizebeth, now working for the Treasury Department, was a star witness in a large and expensive trial in New Orleans of top officials of a Canadian outfit that controlled most of the liquor smuggling via the Gulf of Mexico and the Pacific. She deciphered and decoded cryptic radio messages that made prosecution possible.
The Friedman family, which by now included a son and a daughter, was aware that their mother's contact with organized crime had its dangers. Recalls daughter Barbara Atchison, "I remember Dad jesting once, when Mother was late getting home, that she might have been taken for a ride." And, in fact, while the I'm Alone case was under way, agents of the Treasury Department kept her under constant protection. Elizebeth broke open the code-ciphers used by narcotics smugglers. Her contributions to several sensational trials, and the associated convictions, earned her much unwanted attention from the press: "U.S. Woman Helps Smash Drug Ring," and "Key Woman of the T-Men," read two headlines.
War came and her work changed again. She devised a code system for William (Wild Bill) Donovan as he was organizing the Office of Strategic Services, and deciphered messages from German spies in Allied lands.
All this time William had been equally busy, but his work was well hidden from public view. In 1950 his responsibilities changed abruptly from the bookish work of composing codes. It was prompted by the closing of the Black Chamber, a cooperative codebreaking effort of the State Department and the Army that had evolved from the Army's old Cipher Bureau. The Black Chamber had decoded messages between Tokyo and the Japanese embassy, and in early 1929 Herbert Hoover's new Secretary of State, Henry Stimson, had removed his department's funding upon hearing about it. Years later, in his autobiography, he justified his action by saying that diplomats should not engage in such activities because "gentlemen do not read each other's mail." The Army quietly transferred the activities from the State Department to a new unit in the War Department, the Signal Intelligence Service (SIS). Friedman took charge as chief civilian cryptanalyst.
One of William's principal tasks was to train a new generation of experts to make and break codes, because all of the Black Chamber's personnel had dispersed. He started in the spring of 1930 with four spaces. He selected Frank Rowlett, a teacher from a small town in Virginia; Solomon Kullback and Abraham Sinkov, mathematicians from New York City; and John Hurt, the nephew of a congressman and an expert in Japanese.
The new team combed the files of the Black Chamber for useful information on Japanese cryptology. They read Friedman's booklets and worked through problems he concocted. He gave them assignments such as solving the Hebern cipher machine. "His teaching was such that we developed on our own," recalls Abraham Sinkov. "He just looked in from time to time to see how we were doing."
They operated on slim budgets--bringing their own pencils and writing on the back of old weather reports to save paper--but within two years they had progressed enough for Friedman to present them with the real thing: encrypted radio communications between Japanese diplomats.
By this time the Japanese knew that America had been reading secret diplomatic radio traffic. To protect its highest-level communications, Japan quickly switched to the new electromechanical cipher machine, "Angooki Taipu A." or "Red" to the Americans. It used a combination of wheels, rings and a rotor to scramble clear messages into a complex cipher. In 1935 the Army ordered Friedman's group to concentrate on breaking the system; by 1936 they were able to read the messages.
The passion for cryptology spilled over into the Friedmans' home life. William created a cipher game for children called "The Game of Secrecy" and tried it out on his son, John. He printed holiday greeting cards with cipher messages.
The most inventive of these pastimes were the progressive dinner parties hosted by the Friedmans. They divided their guests--a unique blend of codebreakers, newspapermen and scientists--into teams, and held the first course at one restaurant. "While they were eating, the restaurant owner gave them a piece of paper containing a clue about the next place to go," recalls John Friedman. "They'd go to five or six restaurants.... The first team to return home, won a prize."
William amused his children with enigmatic behavior. "He would come down to Sunday breakfast with six different ties on," remembers his daughter, Barbara. "He had a terrific sense of humor and whimsy, and women absolutely adored him."
Friedman had to leave most of his social life behind, however, when the Japanese decided to replace the Red machine with something much more secure. Labeled "Purple" by the SIS, the machine first contributed messages to Japan's radio circuits in February 1939. Unlike its predecessors, Purple used a type of switch identical to those used in automatic telephone exchanges to accomplish the main work of encipherment.
While dozens of others did the detailed statistical analysis necessary, William labored alone in his office on portions of the problem. He worked obsessively. The fear of failure--of what the Japanese were up to behind the screen of Purple--followed him home each night. "He'd be up until 2 or 3 in the morning," Elizebeth recalled later. "Sometimes I'd awaken and find him down in the kitchen making a Dagwood sandwich in the middle of the night." She remembered that her husband never discussed his difficulties with Purple, not even on the day in the fall of 1940 when the deciphering first succeeded. (For years, all he would tell his son, John, about his job was that he "worked for the Army.")
The team spent a total of 18 months puzzling out the mechanism and the nest of wiring from their calculations son how the original machine converted plaintext to cipher. Then, out of $684.65 worth of parts, they went ahead and built their own reconstruction of the Purple machine.
The Purple disclosures (codenamed "Magic") proved extremely valuable during the war. Ironically, says David Kahn, Magic "had its greatest effect on the war against Germany, not Japan, because we were getting a great deal of information that the Japanese ambassador in Berlin was sending ii back to Tokyo." For example, the ambassador, Baron Oshima, described Germany's new jet fighters in detail, and he listed German troop strength in the Balkans. Oshima even cabled a close description of the Normandy defenses in late 1943. Unfortunately, Magic did not clearly reveal the Japanese intention to attack Pearl Harbor --signals only indicated an impending crisis between America and Japan.
Codebreaking definitely changed the course of the war. The Allies made three major breakthroughs in all: the Japanese diplomatic cipher, Purple: the main German military cipher called "Enigma," which was broken by the Polish and British; and the Japanese fleet code, broken by the U.S. Navy, which made possible many American victories including the Battle of Midway. What made the breaking of Purple so extraordinary, says author Louis Kruh, is that the SIS had no pieces of the machine to study. When the team studied genuine Purple components after the war, he adds, they found that, out of all the thousands of soldered connections, "only two wiring connections turned out to have been interchanged."
Due largely to overwork on Purple, William suffered a mental breakdown at the turn of the year, and spent the next three months recovering in Walter Reed Hospital. Though the hospital recommended he return to duty, shortly afterward the Army discharged him from service. He served out the war as a civilian, organizing attacks on new cipher systems and rapidly training more cipher personnel.
"The war years were horrendous," recalls his daughter. "He was very, very involved in his work. I remember being worried to death about Dad." Attacks of depression severe enough to require psychiatric treatment or hospitalization would return again.
Wartime associates remember William as demanding and brilliant. "When working on a problem," recalls Frank Rowlett, "he was inclined to develop a plan of attack which he usually followed meticulously until the problem was either solved or it could be established that the attack would not be successful. His memory was excellent and he had a most unusual ability to grasp the complexity of a problem." Lambros Callimahos, a concert flutist who became a codebreaker in 1942, remembered Friedman as the "dapper figure with the Adolphe Menjou mustache, the characteristic bow tie, and the two-tone black-and-white shoes." Friedman was notoriously meticulous, even to the point of keeping carbon copies of handwritten notes. Judy Friedman, his daughter-in-law, remembers her he first weekend visit with the family. John had forewarned her that if his father failed to criticize her language, that meant she hadn't made the grade. Throughout the weekend, there was not a single comment from William about her speech. Judy was crushed. Then, upon leaving the house, he leaned close and whispered, "My dear, you made five grammatical errors this weekend," and proceeded to elaborate on them. Nothing could have pleased her more.
After the war, the Army restored William's rank and he served as a top ranking cryptanalyst in the various agencies leading up to the present National Security Agency (NSA). In 1956 Congress awarded him $100,000, partly in compensation for many of his inventions that were so sensitive and useful that the military had kept them off the market. One of these, a mechanism he had developed with Frank Rowlett, was the basis of the SIGABA machine, which the U.S. military used as its top-level enciphering device during World War II. The Axis never penetrated its messages.
William retired officially from the NSA in 1955 but continued to undertake various special and highly secret missions. His relations with the NSA were stormy at times; he believed the agency sometimes mistreated him and that it snooped excessively into citizens' communications. The NSA, in turn, occasionally saw him as a security risk: in 1958 three NSA employees appeared at his Capitol Hill house and carried off a stack of papers.
Elizebeth finished her professional career as a consultant for the International Monetary Fund, setting up a secure communications system there.
Toward the end of their careers (William died in 1969 and Elizebeth in 1980), the couple returned to the unlikely project that had first seduced them into the world of cryptography -the Shakespeare problem. Their incisive book, titled The Shakespearean Ciphers Examined, won them a Folger Shakespeare Library award in 1955. And in a classic demonstration of their life's work, Elizebeth and William Friedman included a hidden biliteral cipher on page 257 of the book. Buried in an italicized phrase, using two different typefaces, is their final verdict about the whole controversy: "I did not write the plays. E Bacon."
Additional Reading
The Codebreakers: The Story of Secret Writing
by David Kahn, Macmillan, 1967
The Shakespearean Ciphers Examined
by William F. and Elizebeth S. Friedman,
Cambridge University Press, 1957
The Man Who Broke Purple
by Ronald Clark, Little, Brown, 1977
Machine Cryptography and Modern Cryptanalysis
by Cipher A. Deavours and Louis Kruh,
Artech House (Dedham, Massachusetts), 1985
The Index of Coincidence and Its Applications in Cryptography
by William F. Friedman, (Riverbank publications, Vol. 9),
Aegean Part Press (Laguna Hills, California), 1979
Why Microwave Auditory Effect Crowd-Control Gun Won't Work Experts say you'd fry before you heard anything By Monica Heger / July 2008
reddit Slashdot Digg StumbleUpon delicious Facebook Twitter
PHOTO: Franco Vogt/Corbis
22 July 2008— New Scientist magazine recently reported that Sierra Nevada Corp., based in Sparks, Nevada, plans to build what it calls a nonlethal microwave ray gun with the ability to beam irritating sounds into people’s heads. But experts in the underlying biophysics say it cannot work: the device would kill you well before you were bothered by the noise.
The gun, which is being built by Lev Sadovnik at Sierra Nevada, would take advantage of a phenomenon known as the microwave auditory effect. When microwaves are delivered in short pulses, the cochlear tissue in the ear expands. That expansion is heard as an audible click to anyone receiving the radiation, a sound much like that of two rocks being hit together underwater. The company says that the device, called MEDUSA (for ”mob excess deterrent using silent audio”), could be used for crowd control.
However, experts say the gun wouldn’t work as advertised. There is no way the ray gun could deliver sound loud enough to be annoying at nonfatal power levels, says Kenneth Foster, a bioengineering professor at the University of Pennsylvania who first published research on the microwave auditory effect in 1974.
”Any kind of exposure you could give to someone that wouldn’t burn them to a crisp would produce a sound too weak to have any effect,” Foster says.
Bill Guy, a former professor at the University of Washington who has also published on the microwave auditory effect, agrees. ”There couldn’t possibly be a hazard from the sound, because the heat would get you first,” Guy says.
Guy says that experiments have demonstrated that radiation at 40 microjoules per pulse per square centimeter produces sound at zero decibels, which is just barely in hearing range. To produce sound at 60 decibels, or the sound of normal conversation, requires 40 watts per square centimeter of radiation. ”That would kill you pretty fast,” Guy says. Producing an unpleasant sound, at about 120 decibels, would take 40 million W/cm2 of energy. One milliwatt per square centimeter is considered to be the safety threshold.
”There’s a misunderstanding by the public and even some scientists about this auditory effect,” says Guy.
Theoretically, the gun could be used by the military, says James Lin, professor of bioengineering at the University of Illinois. ”With any weapon, the intent is to do damage,” he says. In this case, Lin says, the gun would be more likely to cause tissue damage, brain damage, or nerve cell damage than an auditory annoyance.
Sadovnik’s project received a grant from the U.S. Navy Small Business Innovation Research several years ago. The Navy awards grants in phases, and the MEDUSA failed to receive a grant beyond the first phase. Now Sadovnik is working on the project at Sierra Nevada. He declined to comment for this article.
reddit Slashdot Digg StumbleUpon delicious Facebook Twitter
PHOTO: Franco Vogt/Corbis
22 July 2008— New Scientist magazine recently reported that Sierra Nevada Corp., based in Sparks, Nevada, plans to build what it calls a nonlethal microwave ray gun with the ability to beam irritating sounds into people’s heads. But experts in the underlying biophysics say it cannot work: the device would kill you well before you were bothered by the noise.
The gun, which is being built by Lev Sadovnik at Sierra Nevada, would take advantage of a phenomenon known as the microwave auditory effect. When microwaves are delivered in short pulses, the cochlear tissue in the ear expands. That expansion is heard as an audible click to anyone receiving the radiation, a sound much like that of two rocks being hit together underwater. The company says that the device, called MEDUSA (for ”mob excess deterrent using silent audio”), could be used for crowd control.
However, experts say the gun wouldn’t work as advertised. There is no way the ray gun could deliver sound loud enough to be annoying at nonfatal power levels, says Kenneth Foster, a bioengineering professor at the University of Pennsylvania who first published research on the microwave auditory effect in 1974.
”Any kind of exposure you could give to someone that wouldn’t burn them to a crisp would produce a sound too weak to have any effect,” Foster says.
Bill Guy, a former professor at the University of Washington who has also published on the microwave auditory effect, agrees. ”There couldn’t possibly be a hazard from the sound, because the heat would get you first,” Guy says.
Guy says that experiments have demonstrated that radiation at 40 microjoules per pulse per square centimeter produces sound at zero decibels, which is just barely in hearing range. To produce sound at 60 decibels, or the sound of normal conversation, requires 40 watts per square centimeter of radiation. ”That would kill you pretty fast,” Guy says. Producing an unpleasant sound, at about 120 decibels, would take 40 million W/cm2 of energy. One milliwatt per square centimeter is considered to be the safety threshold.
”There’s a misunderstanding by the public and even some scientists about this auditory effect,” says Guy.
Theoretically, the gun could be used by the military, says James Lin, professor of bioengineering at the University of Illinois. ”With any weapon, the intent is to do damage,” he says. In this case, Lin says, the gun would be more likely to cause tissue damage, brain damage, or nerve cell damage than an auditory annoyance.
Sadovnik’s project received a grant from the U.S. Navy Small Business Innovation Research several years ago. The Navy awards grants in phases, and the MEDUSA failed to receive a grant beyond the first phase. Now Sadovnik is working on the project at Sierra Nevada. He declined to comment for this article.


